With politically motivated DDoS (distributed denial of service attack) attacks proliferating along with the overall increase in the supply of managed “DDoS for hire” services, it’s time to get back the basics, and find out just what makes an average DDoS bot used by cybercriminals successful.
Continuing the “A peek inside…” series, in this post I’ll profile the Darkness X (Optima) DDoS bot, available for purchase at selected cybercrime-friendly online communities since 2009.
More details:
The Darkness (Optima) DDoS bot is still under active development by Russian malware coders, according to a recent advertisement posted at a cybercrime-friendly online community. Let’s profile this ubiquitous platform for launching DDoS attacks.
More details on the bot’s history:
Before you learn all the features of our product, we would like to briefly tell the story. 8th March 2009 (nothing to do with the holiday on this day) was put up for sale in the first version of DDoS Bot’a Darkness. The product was surprisingly well received by audiences and sell “sack.” In the second version of the bot was also released an optimized version of the admin panel, which was called the “Optima”. Since then, the double name of our product “Darkness (Optima) DDoS Bot”. Since 2009, the year product was gradually developed, improved, acquired new functions. 1st October 2011 we presented the 10th version of our product – “Darkness X DDoS Bot”.
Among the main features of the bot are:
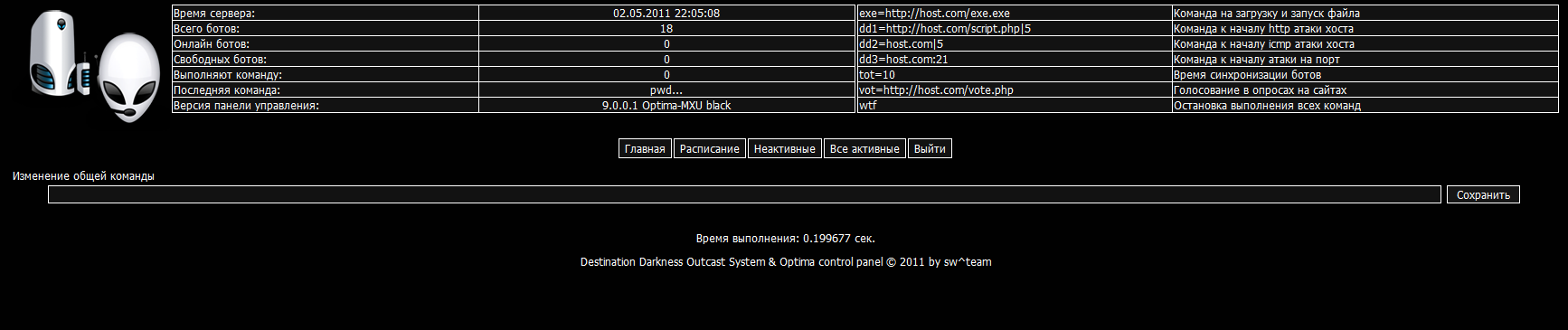
• 4 types of DDoS attacks: http, icmp (ping), syn, udp
• The ability to attack on several URL of a server.
• Ability to progruzhat and run your. Exe files.
• A sound system of granting user-agent and referral. Randomly generated for each call.
• Our bot is almost no load on the system, which allows him to remain invisible for a long time.
• Compatible with all series of the Microsoft Windows 95 – Windows7.
• Works correctly under 64-bit systems.
• Correctly works as a yuzersky uchetku and under admin.
• The file name is not in the numbers and not just a bunch of random letters and the word or abbreviation, however, generated randomly.
• Bypasses Windows Firewall
• Easy-crypt, from the version I have 10G Plus
• Immediately installed in the system, thus avoiding any suspicion among the victims.
• Works in 100 threads, it is possible to set a timeout. Moreover, the flow is almost perfectly synchronized with each other, which makes it possible to generate the maximum amount of HTTP traffic.
• The attack on the individual server (for example, a forum, news block, file storage). In this type of attack targets chosen by each instance of the bot separately, which, in turn, at times increases the load on the server, because the answer can not be cached.
• Bypass of some Anti-DDoS defenses.
• Modularity. You can buy add-on in the form of modules.
• Due to a very good code optimization bot has a good weight: 30-40 kb. packed and 90-130 kb. Uncompressed, depending
the availability of certain modules.
• Support for Socks5 proxy. The default port – 1080, you can change when you create a build. Note that the proxy normal and does not work through NAT.
• Real-time tech support.
The bot supports four different types of DDoS attacks, namely HTTP flood, ICMP flood, ping, SYN flood and UDP flood. The modular nature of the bot allows the sellers to offered it using flexible pricing schemes, based on the number and type of additional modules requested by the cybercriminals wanting to buy it.
Infected hosts can simultaneously launch up to 100 networks threats against the targeted web sites, with every request using a different user-agent and HTTP referer in an attempt to bypass Anti-DDoS protection solutions.
Screenshots of the Command and Control interface:
The Web-based command and control interface is called Optime. More details on the Optima Web-based command and control interface:
[Premium Features Admin Panel “Optima”]
• Simple, intuitive control panel; the most optimized, which reduces the load on the server.
• Easy to install.
• Ability to schedule the execution of commands.
• High degree of protection.
• A demo access.
• Admin panel shows the version of the bot, OS version and type of account – the administrator or user. A / U, respectively.
• Bilingual (RU, EN).
• Outstanding protection against unscrupulous downloaders (if the boat is loaded on a PC is infected, it will report this to the admin panel of the word FIAL).
• Real-time tech. Support.
The Darkness (Optima) DDoS bot comes with five different plugins, allowing the release of hybrid versions of the bot, each of them offering additional malicious models at the disposal of the malicious attacker.
More details on the plugins available for additional sale:
1) ThiefX. Version: 1.3. Grabber passwords. This module is able to “rob” the passwords for
14 programs (at your option can be added to additional programs):
• Fxp (ftp)
• Total commander (ftp)
• Filezilla (ftp)
• Wsftp (ftp)
• Mozilla Firefox (including version 7 of) (web, forms)
• Opera (including the latest version) (web, forms, ftp)
• CuteFTP (ftp)
• Qip2005 (icq)
• Qip2010 (icq, eml)
• QipInfium (icq, eml)
• The bat (eml)
• RDP (rdp)
• Google Chrome (web)
• Safari (web)2) Tunnel. Version: 1.0. Back-Connect (Reverse) Socks 5 module. Allows you to use your bots as proxies.
3) Substitution. Version: 1.0. Module that allows online editing / hosts file to replace your bots.
4) the possible development of a module for the substitution of Webmoney purses in the clipboard. If you have any questions, please icq.
5) MKL Keylogger. Version: 1.1. Keylogger that supports Cyrillic and the ability to send logs to HTML / FTP
Like in other underground malware releases, in Darkness (Optima) DDoS bot’s case, the malware coders are also issuing a license agreement which potential buyers have to accept once they purchase a copy of the bot. Basically, the agreement states that the bot is to be used for testing purposes only.
What about prices? Thanks to the bot’s modular nature, the Russian malware coders behind it have created multiple market propositions, aiming to satisfy the needs of multiple potential customers, from different market segments.
Types of subscriptions:
• Minimum: DDoS bot no free upgrades = $ 450
• Standard: DDoS bot + Month Free Upgrades = $ 499
• Bronze: DDoS bot + 3 months free upgrades plus one free rebild. = $ 570
• Silver: DDoS Bot + months of free updates + three free rebilda. = $ 650
• Gold: DDoS Bot + unlimited free upgrades + 5 free rebilda + 5% discount on our products. + Module “password grabber” as a gift = $ 699
• Platinum: DDoS Bot + Free Updates on forever + free + rebildy without restrictions 25% discount on our products + 2 modules to choose a gift = $ 825
• Diamond: DDoS Bot + Free updates + Free unlimited rebildy without limitation + 30% discount on all our products + plug-ins as a gift. = $ 999
• ReBuild (change domain) – $ 35.
• Sources – discussed separately.
• New function – is discussed separately.
The prices for the different modules available for sale with the DDoS bot are as follows:
• ThiefX. Grabber passwords. – $ 50
• Substituion. Substitution of hosts. – $ 35
• Tunnel. Back-Connect socks. – $ 250
• MKL Keylogger. – $ 55 Also, this module can be purchased as a separate product at a price of $ 85.
• Development of new modules. – Discussed separately
What’s particularly interesting about the Darkness (Optima) DDoS bot is the fact in order to achieve an increased market penetration from day one, the Russian malware coders behind the bot, have also introduced an affiliate-based reselling platform, allowing third-parties who resell the bot, the chance to earn additional revenue. In this case that’s $45 to $100 for a single client referred by a third-party user part of the affiliate network.
On the 16th of February, 2012, the authors of the kit posted an update explaining the newest features and improvements introduced in the bot:
1) New update Xi. List of changes:
– Rewrote the UDP flood attack power increased by 10-15%
– Added new methods to bypass Anti-DDoS protection through clever use of cookies and user-agents.
– Fixed a rare bug that did not properly identify the country bot
– Fixed rare bug where the bot “fell” in obtaining multi-team
– Fixed rare bug where the bot is not properly reported to the admin-panel version of the bot
– Other minor bug fixes.2) You will soon see the update pass-grabber, and other add-ons bot.3) Very soon we will conclude an agreement with several kriptovschikami, so the bot will crypts
even easier.
Webroot’s security researchers will continue monitoring the bot’s development to ensure that Webroot SecureAnywhere customers are protected from this threat.
Related posts:
- A peek inside the Elite Malware Loader
- A peek inside the Ann Malware Loader
- A peek inside the Smoke Malware Loader
- A peek inside the uBot malware bot
- A peek inside the PickPocket Botnet
- A peek inside the Umbra malware loader
- A peek inside the Cythosia v2 DDoS Bot
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.









I say we fight back against these guys by giving them a dose of their own medicine
Indeed FIGHT…but how is it at all possible to ever get ahead of such evil doers? It is like the modern day war against EVIL and Good. We all try to put our trust in security software that has been around for a while.
So the newcomer (User) has no idea in what to believe. So in most cases it is by their research and then the reviews of those that use it.
Which does make one real solution clear….”Research and reviews Never saying yes until we do”.
Even then……what is lurking within???