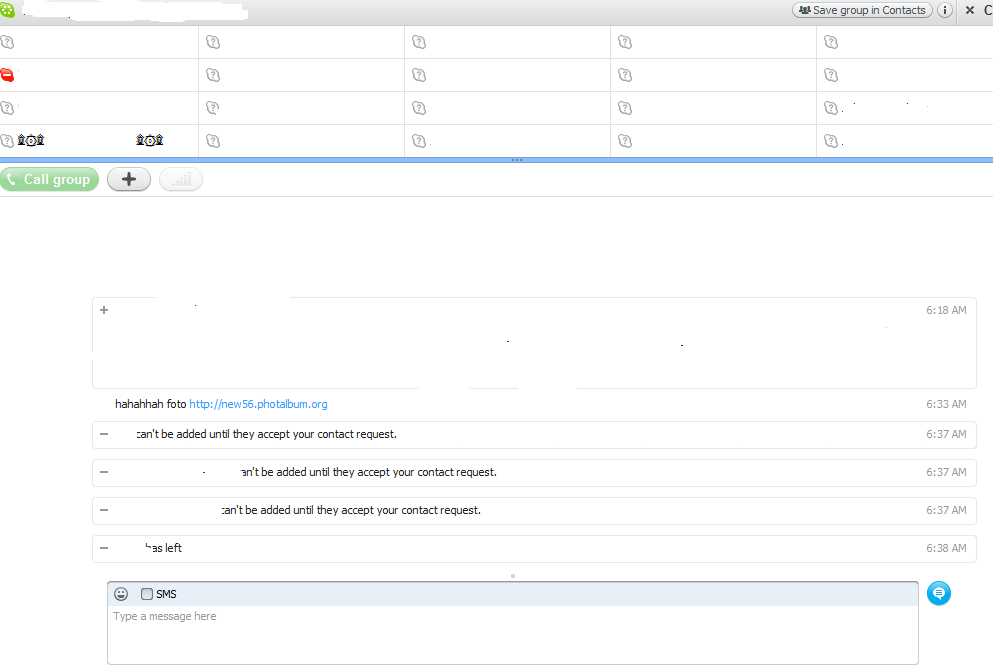
Last night, a friend of mine surprisingly messaged me at 6:33 AM on Skype, with a message pointing to what appeared to be a photo site with the message “hahahahaha foto” and a link to hxxp://random_subdomain.photalbum.org
What was particularly interesting is that he created a group, and was basically sending the same message to all of his contacts. Needless to say, the time has come for me to take a deeper look, and analyze what appeared to be a newly launched malware campaign using Skype as propagation vector.
More details:
Once the socially engineered clicked on the link, a Download window will automatically prompt them to download the following file – Photo9321092109313.JPG_www.facebook-com.exe. Notice how the cybercriminals behind the campaign try to trick end users into thinking that they’re about to open an image file, potentially coming from Facebook. In reality though, it’s an executable.
- Security tip: Windows users can see how they can enable full file extension here, and Mac OS X users can view how they can start displaying full file extensions here.
Malicious subdomains spamvertised over Skype messages:
- hxxp://new07.photalbum.org
- hxxp://new39.photalbum.org
- hxxp://new67.photalbum.org
- hxxp://new43.photalbum.org
- hxxp://new32.photalbum.org
- hxxp://new56.photalbum.org
photalbum.org – 98.124.198.1 (AS21740, DemandMedia) – Email: cuti@ilirida.net
The following domains were also registered using the same email address:
- photo-facebook.info
- Msn-gallery.net
- Ebunet.org
- Mut-article.net
- Megaarticles.biz
- Megaarticles.org
- Megaarticles.biz
- Mut-article.net
The Photo9321092109313.JPG_www.facebook-com.exe sample has the following MD5, MD5: bc3214da5aac705c58a2173c652e031e, currently detected as Trojan.Win32.Jorik.PoisonIvy.yy, Trojan.Win32.Diple!IK by 16 out of 42 antivirus engines.
Upon execution the binary, creates a batch script, installs a program to run automatically at logon, and creates a thread in a remote process.
It then it phones back to the following domains/IPs:
- hd.hidbiz.ru
- 4.45.182.239:1986
Another sample with MD5: fe18d433eb8933fa289b5d9a00e2f5c7 is known to have used these C&C domains/URLs before. It also modifies the browser’s start page to: Start Page = “hxxp://enaricles.com”.
More malware MD5’s that modify the browser’s start page to hxxp://enaricles.com:
MD5: 5de919fad7969043a3ebeff2e103b996
MD5: 23db2396cccc6f70f37153419ba14d6b
MD5: 45958771468f1ad3200e60c89126b285
MD5: 435a9835464ccff075339d7021508609
MD5: ec06e9ee54f8534beb35f45f03ac0cbc
Hijacked trusted and legitimate Skype accounts are invaluable from a social engineering perspective. Trust is vital, even novice end users know it. If the cybercriminals were to automatically register thousands of bogus accounts, they would attempt to only target users who allow the receiving of messages from users who are NOT on their contact list. Although millions of Skype users continue receiving these messages, the majority of successful malware campaigns using Skype as propagation vector, tend to involve trusted and compromised Skype accounts in an attempt to increase the probability of a successful infection.
- Security tip: In order to prevent receiving messages from people not on your contact list, follow the instructions offered here.
What’s so special about the payload anyway? The payload is a copy of the infamous Poison Ivy DIY RAT (Remote Access Tool) also known as a trojan horse or backdoor. The attackers chose this easy to obtain RAT for serving malicious code, compared to a situation where they would need to code it from scratch.
Webroot SecureAnywhere proactively protects against this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Well thas not good. I have seen this in the wild.
Thanks for the heads up… skype is my life
Wow, nice Post written by you guys. It is amazing and wonderful to visit your site. Thanks a ton for such a nice post.
I recently was hacked in my email by this skype thing and I dont use skype. I am sure it was a client of mine as 20 minutes later he left me a threatening call. However, it went through all my contacts and sent a link to all of them. So I did changed my password and notifited everyone on my contact list which took me two days. So what else can I do to ensure this does not happen again and that it is gone as I have your program on my computer, I run the scan everyday and nothing shows up. I have also received invitations to the linkin site which I do not use either. so now I dont want to open any emails and I dont have enough evidence to get this guy yet.