Think you received a package? Think again. Cybercriminals are currently spamvertising millions of emails impersonating UPS (United Parcel Service) in an attempt to trick users into downloading the viewing the malicious .html attachment.
More details:
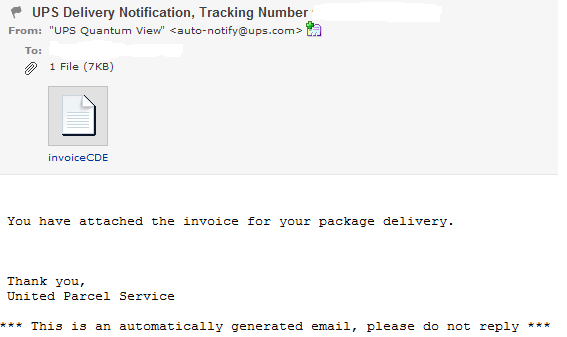
Subject: UPS Delivery Notification, Tracking Number CDE_RANDOM_NUMBER
Sample message: You have attached the invoice for your package delivery. Thank you, United Parcel Service. *** This is an automatically generated email, please do not reply ***
Sample attachment: invoiceCDE31400FCA9E1A9.html; MD5: 3df9cab56e3a354c56d0b50680a9e087 detected by 8 out of 42 antivirus scanners as HTML:Iframe-inf; Trojan.IframeRef; Mal/JSRedir-J
The attached .html file includes a tiny iFrame pointing to the client-side exploits serving domain hxxp://www7apps-myups.com/main.php?page=cde31400fca9e1a9 – 96.43.129.237, Email: zxhxnjsgh@126.com
Upon loading, it attempts to exploit CVE-2010-1885, served by the BlackHole web malware exploitation kit.
Sample client-side exploitation chain: hxxp://www7apps-myups.com/main.php?page=cde31400fca9e1a9 -> hxxp://www7apps-myups.com/Set.jar -> hxxp://www7apps-myups.com/data/ap2.php
Upon successful exploitaion the campaingn drops the following MD5 on the infected hosts, MD5: 5806aba72a0725a9d65eb12586846da3, currently detected by 8 out of 41 antivirus scanners as Gen:Variant.Kazy.74635; Trojan.PWS.Panda.655.
It’s worth pointing out that the initially spamvertised .html file doesn’t contain any exploit code in an attempt to trick antivirus scanners into thinking it’s a legitimate content.
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.