On their way to occupy an even bigger market share, spammers constantly look for new ways to increase visitor conversion, and target as many users as possible with the least amount of time and money invested.
For years, their tactics included the development of cybercrime friendly online communities, sophisticated harvesting and validation of emails and user names across popular Web services, abusing the Domain Keys Identified Mail (DKIM) trust established between the most popular providers of free Web based email, development of DIY image spam generating platforms, conversion of malware-infected hosts into spam spewing zombies, and most importantly, efficient ways to bypass anti-spam filters put in place by the security industry.
In this post, I’ll profile a recently advertised Ask.fm spamming tool, capable of spamming thousands of users through the use of proxies, which are in fact malware-infected hosts converted to anonymization proxies.
More details:
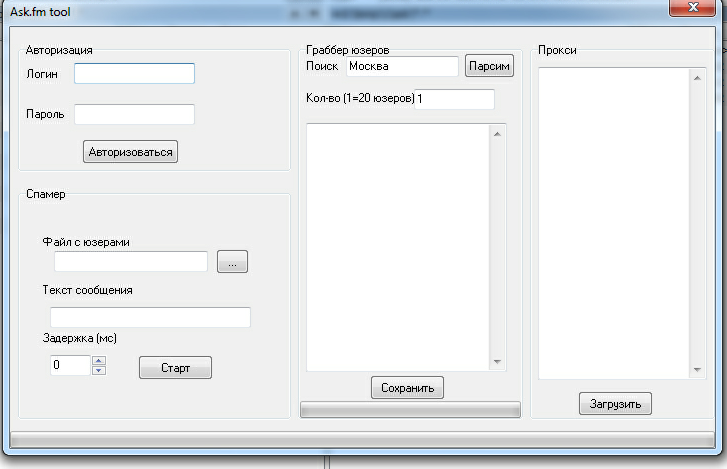
Screenshot of the Ask.fm spamming tool:
Based on its features, it requires a valid account at Ask.fm to be used as a foundation of the campaign. It then requires a user names list, the spam message, and the speed of the spam campaign, in milliseconds. It also claims to have the capability to harvest user names of Ask.fm users based on a particular city. It also offers the ability to user proxies as a way to prevent the automatic detection of the spam campaign in cases when it’s relying on a single IP for the initial start of the campaign.
Would this DIY spamming tool have an impact on the popular Ask.fm service? Not at all. Thanks to the tool’s inability to support multiple automatically registered accounts in combination with proxies, I can conclude that it will have a very limited impact on the overall spam level at Ask.fm.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







someone found this tool?