Cybercriminals are currently mass mailing millions of emails, in an attempt to trick Bank of America customers into clicking on the exploit and malware-serving link found in the spamvertised email. Relying on bogus “Online Banking Passcode Changed” notifications and professionally looking email templates, the campaign is the latest indication of the systematic rotation of impersonated brands in an attempt to cover as many market segments as possible.
More details:
Screenshot of a sample spamvertised email:
Sample spamvertised and compromised URLs participating in the campaign – hxxp://kuj-pom.pl/wp-content/themes/simplenotes/resetPass.html; hxxp://mastropasticcere.bar.it/wp-content/themes/default/resetPass.html; hxxp://1980.mods.jp/wp-content/plugins/passchanged.html; hxxp://sunsetheroes.com/wp-content/plugins/1/passchanged.html; hxxp://www.jee-choi.com/test/wp-content/plugins/intensedebate/resetPass.html
Client-side exploits serving URL: hxxp://the-mesgate.net/detects/signOn_go.php – 183.81.133.121, AS38442 – Email: counseling72@yahoo.com
Also responding to the same IP are the following malicious domains:
stafffire.net – 183.81.133.121, AS38442
hotsecrete.net – Email: counseling1@yahoo.com
formexiting.net – suspended domain
navisiteseparation.net – suspended domain
Name servers part of the campaign’s infrastructure:
Name Server: NS1.TOPPAUDIO.COM – 91.216.93.61, AS50300 – Email: windowclouse@hotmail.com
Name Server: NS2.TOPPAUDIO.COM – 29.217.45.138 – Email: windowclouse@hotmail.com
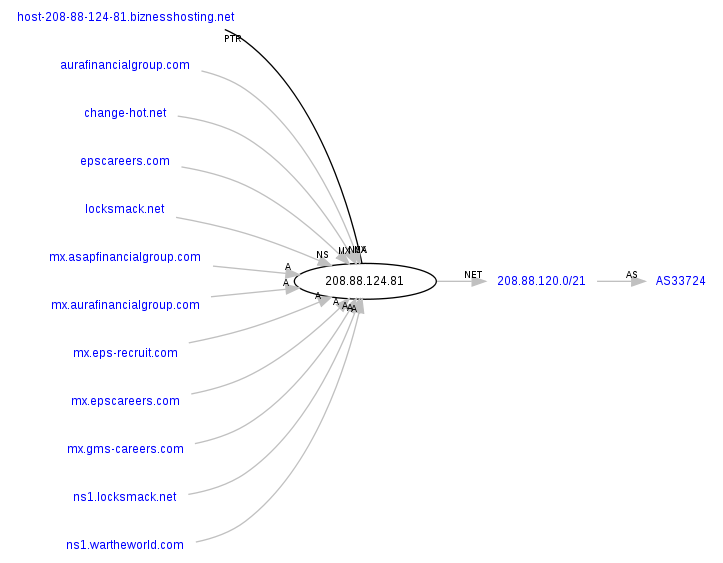
Name Server: NS1.TWEET-TOWEL.NET – 208.88.124.81 – Email: worldonaplate@rocketmail.com
Name Server: NS2.TWEET-TOWEL.NET – 5.88.90.51 – Email: worldonaplate@rocketmail.com
Name Server: NS1.ELEPHANT-TRAFFIC.COM – 217.11.251.172
Name Server: NS2.ELEPHANT-TRAFFIC.COM – 217.11.251.171
Name Server: NS3.ELEPHANT-TRAFFIC.COM – 217.31.59.77
We’ve already seen the same email (windowclouse@hotmail.com) used in a previously profiled malicious campaign impersonating Intuit – “‘Intuit Payroll Confirmation inquiry’ themed emails lead to the Black Hole exploit kit“, where the client-side exploit-serving URL (art-london.net) was also registered with the same email.
Related malicious domains responding the these IPs:
change-hot.net
locksmack.net
Money mule recruitment domains using the same IP as a mailserver:
aurafinancialgroup.com
epscareers.com
As you can see, this campaign is great example of the very existence of the cybercrime ecosystem. Not only are they spamvertising millions of exploits and malware serving emails, they’re also multitasking on multiple fronts, as these two domains are recruiting money mules to process fraudulently obtained assets from the affected victims.
The following malicious domains are also part of the campaign’s infrastructure:
dgstore.org
optioncommandescape.co.uk
www.cm
z6x8.com
netcenterc.com
www.ubegalore.com
blackbluerose.com
www.googletranslate.com
nokiaupdte.com – typosquatted domain impersonating Nokia Update
musiconlineshop24h.com
youngideafashion.com
twiiter.com – typosquatted domain impersonating Twitter
alexaworldserver.com
webcampagnes.com
fitzpatrickshoes.com
traderbmarkings.com
thephoenix-forums.com
clickbankstat.com
www.jmbrino.blogsot.com – typosquatted domain impersonating Google’s Blogspot
cc11tttttttt.com
cc22tttttttt.com
gbmainadv.com
zdata.in
novastore.in
amigohello.in
gringohello.in
secway.in
blogging4life123.net
etredir-001aa.net
adam-love.net
backserviceag.net
onlinebrg.net
bushadverl.net
obdomain.net
amigohello.net
gringohello.net
bigpointers.net
verybigdays.net
datawebnet.net
sampleadvert.net
fieldmanv.net
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.