On a periodic basis, malicious cybercriminals spamvertise millions of emails attempting to trick end users into thinking that they’ve received a scanned document. Upon clicking on the links found in these emails, or viewing the malicious .html attachment, users are automatically exposed to the client-side exploits served by the latest version of the Black Hole Exploit Kit.
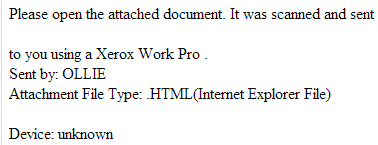
In this post, I will profile two currently circulating malicious campaigns. The first is mimicking a Xerox Pro printer, and the second is claiming to be a legitimate Wire Transfer. Both of these campaigns point to the same client-side exploits serving URL, indicating that they’ve been launched by the same cybercriminal/gang of cybercriminals.
More details: Sample screenshots of the spamvertised emails:
Client-side exploits serving URLs: hxxp://panalkinew.ru:8080/forum/links/column.php; hxxp://panalkinew.ru:8080/forum/links/column.php?rcgeyqil=0406080806&qkped=36&kwtgtko=3307093738070736060b&ucu=02000200020002
Spamvertised compromised URL used in the Wire Transfer themed campaign: hxxp://www.mm4management.com/indeaxo.htm
Upon loading, the URLs exploit CVE-2010-0188 in an attempt to drop a malicious PDF file on the affected host. The sample then drops additional malware.
Detection rate for a sample javascript obfuscation: MD5: 0a8a06770836493a67ea2e9a1af844bf – detected by 15 out of 43 antivirus scanners as Mal/JSRedir-M
Detection rate for the dropped malware: MD5: 194655f7368438ab01e80b35a5293875 – detected by 25 out of 43 antivirus scanners as Trojan-Ransom.Win32.PornoAsset.avzz
panalkinew.ru responds to the following IPs – 203.80.16.81, AS24514; 209.51.221.247, AS10297; 213.251.171.30, AS16276
Responding to the same IPs are also the following malicious domains part of the campaign’s infrastructure:
manekenppa.ru
kiladopje.ru
lemonadiom.ru
finitolaco.ru
fidelocastroo.ru
ponowseniks.ru
panasonicviva.ru
geforceexlusive.ru
limonadiksec.ru
linkrdin.ru
sonatanamore.ru
secondhand4u.ru
windowonu.ru
Deja vu! We’ve already seen one of these domains (sonatanamore.ru) used in the recently profiled “‘Regarding your Friendster password’ themed emails lead to Black Hole exploit kit” campaign, indicating that these campaigns have been launched by the same malicious party.
Name servers used in the campaign’s infrastructure:
ns1.panalkinew.ru – 62.76.186.190
ns2.panalkinew.ru – 84.22.100.108
ns3.panalkinew.ru – 50.22.102.132
ns4.panalkinew.ru – 213.251.171.30
ns1.manekenppa.ru – 85.143.166.170
ns2.manekenppa.ru – 132.248.49.112
ns3.manekenppa.ru – 84.22.100.108
ns4.manekenppa.ru – 213.251.171.30
ns1.kiladopje.ru – 85.143.166.170
ns2.kiladopje.ru – 132.248.49.112
ns3.kiladopje.ru – 84.22.100.108
ns4.kiladopje.ru – 213.251.171.30
ns1.lemonadiom.ru – 85.143.166.170
ns2.lemonadiom.ru – 132.248.49.112
ns3.lemonadiom.ru – 84.22.100.108
ns4.lemonadiom.ru – 213.251.171.30
ns1.finitolaco.ru – 85.143.166.170
ns2.finitolaco.ru – 132.248.49.112
ns3.finitolaco.ru – 84.22.100.108
ns4.finitolaco.ru – 213.251.171.30
ns1.fidelocastroo.ru – 85.143.166.170
ns2.fidelocastroo.ru – 132.248.49.112
ns3.fidelocastroo.ru – 84.22.100.108
ns4.fidelocastroo.ru – 213.251.171.30
ns1.ponowseniks.ru – 85.143.166.170
ns2.ponowseniks.ru – 132.248.49.112
ns3.ponowseniks.ru – 84.22.100.108
ns4.ponowseniks.ru – 213.251.171.30
ns1.panasonicviva.ru – 132.248.49.112
ns2.panasonicviva.ru – 84.22.100.108
ns3.panasonicviva.ru – 62.76.47.51
ns1.geforceexlusive.ru – 62.76.47.51
ns2.geforceexlusive.ru – 132.248.49.112
ns3.geforceexlusive.ru – 84.22.100.108
ns4.geforceexlusive.ru – 79.98.27.9
ns1.limonadiksec.ru – 62.76.46.195
ns2.limonadiksec.ru – 87.120.41.155
ns3.limonadiksec.ru – 132.248.49.112
ns4.limonadiksec.ru – 91.194.122.8
ns5.limonadiksec.ru – 62.76.188.246
ns1.linkrdin.ru – 85.143.166.170
ns2.linkrdin.ru – 132.248.49.112
ns3.linkrdin.ru – 84.22.100.108
ns4.linkrdin.ru – 79.98.27.9
ns1.sonatanamore.ru – 62.76.47.51
ns2.sonatanamore.ru – 132.248.49.112
ns3.sonatanamore.ru – 84.22.100.108
ns1.secondhand4u.ru – 85.143.166.170
ns2.secondhand4u.ru – 132.248.49.112
ns3.secondhand4u.ru – 84.22.100.108
ns4.secondhand4u.ru – 79.98.27.9
ns1.windowonu.ru – 85.143.166.170
ns2.windowonu.ru – 132.248.49.112
ns3.windowonu.ru – 84.22.100.108
ns4.windowonu.ru – 79.98.27.9
ns1.panalkinew.ru – 62.76.186.190
ns2.panalkinew.ru – 84.22.100.108
ns3.panalkinew.ru – 50.22.102.132
ns4.panalkinew.ru – 213.251.171.30
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.