Cybercriminals are currently mass mailing millions of emails impersonating Microsoft Corporation in an attempt to trick users into clicking on a link in a bogus ‘License Order” confirmation email. Upon clicking on the link, users are exposed to the client-side exploits served by the latest version of the Black Hole Exploit Kit.
More details:
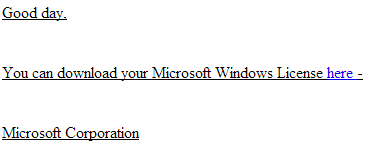
Sample screenshot of the spamvertised email:
Sample compromised URL used in the campaign: hxxp://kalender.mn-welt.de/page2.htm
Sample client-side exploits serving URL: hxxp://fidelocastroo.ru:8080/forum/links/column.php
Sample payload serving URL: hxxp://fidelocastroo.ru:8080/forum/links/column.php?sojhnkxv=030a380233&vjmm=3307093738070736060b&qkzwsj=03&jqgvx=hszplzo&maxtgox=obazeot
Sample client-side exploit served: CVE-2010-0188
Malicious domain name reconnaissance:
fidelocastroo.ru – 209.51.221.247; 203.80.16.81
Name server: ns1.fidelocastroo.ru – 85.143.166.170
Name server: ns2.fidelocastroo.ru – 132.248.49.112
Name server: ns3.fidelocastroo.ru – 84.22.100.108
Name server: ns4.fidelocastroo.ru – 213.251.171.30
The following domains also respond to 209.51.221.247:
kennedyana.ru
leprasmotra.ru
windowonu.ru
bakface.ru
wikipediastore.ru
linkrdin.ru
secondhand4u.ru
We’ve already seen secondhand4u.ru and linkrdin.ru used in the previously profiled “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit” malicious campaign, indicating that both campaigns have been launched by the same party.
Upon successful client-side exploitation, the Microsoft Windows License themed campaign drops MD5: d5211a7882c3c3e66f4a7db04c2a0280 – detected by 37 out of 44 antivirus scanners as Trojan.Win32.Bublik.obv
Once executed, the sample creates the following file on the affected host: %AppData%KB00121600.exe – MD5: D5211A7882C3C3E66F4A7DB04C2A0280 – detected by 37 out of 44 antivirus scanners as Trojan.Win32.Bublik.obv
It then phones back to 188.40.0.138:8080/AJtw/UCygrDAA/Ud+asDAA (AS24940). We’ve already seen the same pseudo-random characters used in the “‘American Express Alert: Your Transaction is Aborted’ themed emails serve client-side exploits and malware” campaign.
More MD5s are known to have phoned back to the same IP in the past. For instance:
MD5: 850c3b497224cee9086ad9ad6a2f71e6 – detected by 4 out of 44 antivirus scanners as UDS:DangerousObject.Multi.Generic
MD5: 2c20575eb1c1ac2da222d0b47639434e – detected by 34 out of 44 antivirus scanners as Trojan-Ransom.Win32.PornoAsset.ascm
MD5: d9eaad9b06e500f7a0cd90a02f537364 – detected by 29 out of 44 antivirus scanners as PWS:Win32/Zbot
MD5: 92978246ab42f68c323c36e62593d4ee – detected by 31 out of 43 antivirus scanners as HEUR:Trojan.Win32.Invader
MD5: 03f5311ef1b9f7f09f6e13ff9599f367 – detected by 35 out of 44 antivirus scanners as Worm:Win32/Cridex.E
MD5: d343eb0ab2703ae3623eb1504f321018 – detected by 37 out of 44 antivirus scanners as Worm:Win32/Cridex.E
MD5: 7b9f0a74820a00b34cc57e7c02d1492c – detected by 39 out of 44 antivirus scanners as W32.Cridex
MD5: cdbc0ba05ce8214d8877c658b648bc7e – detected by 36 out of 44 antivirus scanners as W32.Cridex
MD5: 7515448fa3aa1ee585311b80dab7ca87 – detected by 38 out of 44 antivirus scanners as Trojan-Ransom.Win32.PornoAsset.aaql
MD5: 19f481447e1adf70245582d4f4f5719c – detected by 40 out of 43 antivirus scanners as Worm:Win32/Cridex.E
MD5: ABD0A8FCF1B728B14A9412F6ECF32586 – detected by 27 out of 44 antivirus scanners as Heuristic.BehavesLike.Win32.Suspicious-BAY.K
MD5: 63F0092762566A87BE777A008CE3C511 – detected by 31 out of 44 antivirus scanners as Trojan.Reveton.AN
MD5: BFFC8545808E0F5E1148BDD2A0FBF79E – detected by 39 out of 43 antivirus scanners as Worm:Win32/Cridex.E
MD5: C83877421A4A88B38F155DF2BF786B6A – detected by 24 out of 44 antivirus scanners as Gen:Variant.Kazy.105014
MD5: C379D30CCDC4A57088F8D137DF525CCD – detected by 29 out of 44 antivirus scanners as Trojan.Win32.Bublik.nrz
MD5: 42F36DB25B25196B454771751F8C1B89 – detected by 35 out of 44 antivirus scanners as Malware.Cridex
MD5: 3A8CE3D72B60B105783D74DBC65C37A6 – detected by 33 out of 42 antivirus scanners as Trojan.Win32.Bublik.ols
MD5: EB242D0BFCE8DAA6CC2B45CA339512A0 – detected by 25 out of 43 antivirus scanners as Win32:LockScreen-LV [Trj]
MD5: CDBC0BA05CE8214D8877C658B648BC7E – detected by 36 out of 44 antivirus scanners as Win32:Kryptik-KGB [Trj]
MD5: 733D33FF69013658D50328221254E80C – detected by 25 out of 43 antivirus scanners as Win32.Citadel
MD5: 963FE8239C00318DFF5BF55B866252C3 – detected by 39 out of 44 antivirus scanners as Trojan:W32/Injector.AH
MD5: 0D4FE02D89102B67A722027759EB40D1 – detected by 40 out of 44 antivirus scanners as Gen:Variant.Kazy.102147
MD5: F8254130C26B227616C0939FBE73B9C7
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.