What would an attacker do if they were attempting to inject malicious iFrames on as many Web sites as possible? Would they rely on search engines’ reconnaissance as a foundation fo their efficient exploitation process, data mine a botnet’s infected population for accounting data related to CPanel, FTP and SSH accounts, purchase access to botnet logs, unethically pen-test a Web property’s infrastructure, or hit the jackpot with an ingenious idea that’s been trending as of recently within the cybercrime ecosystem? No, they wouldn’t rely on any of these. They would just seek access to servers hosting as many domains as possible and efficiently embed malicious iFrames on each and every .php/.html/.js found within these domains. At least that’s what the cybercriminal operations that I’ll elaborate on in this post are all about. Let’s take a peek at a recently advertised DIY mass iFrame injecting Apache 2.x module that appears to have already been responsible for a variety of security incidents across the globe.
This module makes it virtually impossible for a webmaster to remove the infection from their Web site, affects millions of users in the process, and earns thousands of dollars for the cybercriminals operating it. More details: The Apache 2.x based stealth module is capable of inserting and rotating iFrames on all pages at a particular website hosted on the compromised server. The process will only work with a cookie+unique IP in an attempt by the cybercriminal behind the kit to make the process of analyzing the module harder to perform. The module would also not reveal the iFrame URL to search engines, Google Chrome and Linux users, as well as local IP. For the time being its price is $1,000. Sample screenshot of the underground market advertisement of the malicious Apache 2 module:

What’s worth emphasizing about this particular cybercrime ecosystem ad is the fact that the author of the Apache 2 module is OPSEC-unaware (Operational Security). What he did is to basically mention research articles profiling the activities of his cybercrime-friendly release, referring to it as – Feedback from “customers” 🙂 –
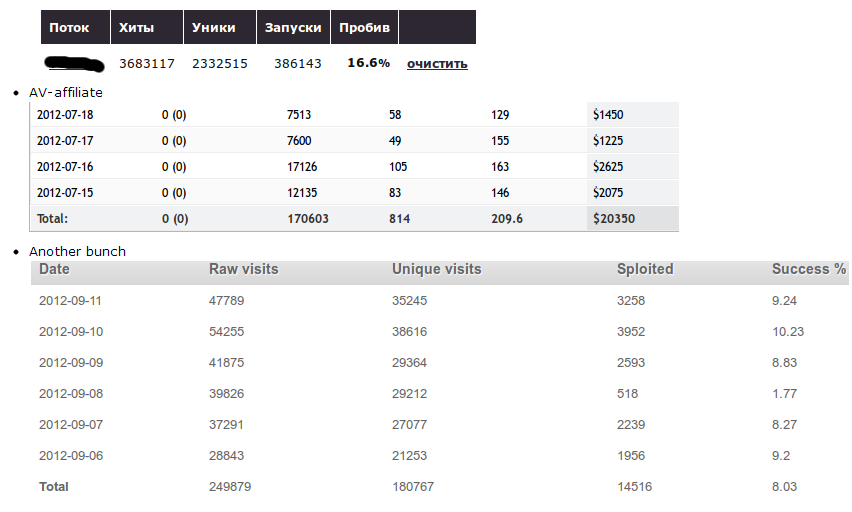
A logical question emerges – what’s the ROI (Return on Investment) from this practice? Pretty decent according to statistics released by the author in an attempt to demonstrate just how much money selling scareware (fake security software) can be made using his malicious module. Sample statistics released by the author of the malicious module:
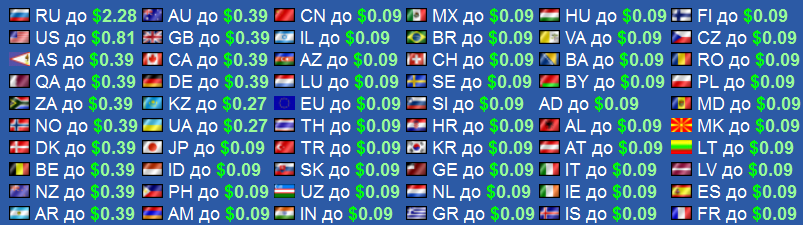
As you can see in the attached screenshot, thousands of users continue installing and purchasing fake antivirus software products, driving a steady flow of income to the accounts of the cybercriminal(s) operating these campaigns. Moreover, the statistics also indicate that thousands of users, visiting their favorite and trusted websites, are getting exploited through client-side exploits like the ones served by the market leading Black Hole Exploit Kit, thanks to the malicious Apache 2 module. Is the development of such stealth modules a trend or a fad? Cybercriminals aren’t suffering from a shortage of legitimate traffic, at least for the time being. Geolocated underground Web traffic exchanges supply a constant stream of unique IPs to be converted to malware-infected hosts, through practices such as spam, black hat SEO (search engine optimization), malvertising, cybercrime-friendly search engines, and bogus multi-topic content farms spread across legitimate Web properties. Sample price list for iFrame driven geolocated traffic for a thousand unique visitors:
We’ll continue monitoring this emerging trend, and post updates as soon as new developments take place. You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








Thanks for all of your feedback, Alexis! Glad you enjoy the information 🙂
If you would like to further participate with us, please join our Webroot Community where you can find solutions to all different kinds of problems and maybe even be able to help someone else yourself! We’d love to have you join.
https://community.webroot.com/
Warm Regards,
Josh P.
Webroot Community Support