Security researchers and security vendors are constantly profiling and blocking the malicious operations launched by organized crime groups on the Internet.
In an attempt to increase the life cycle of their malicious campaigns, cybercriminals rely on a set of domains hosted on bulletproof servers. In addition to this tactic, they also rely on fast-fluxing, a technique where a domain’s IP automatically rotates on a specific time interval, with IPs from the botnet’s infected population — state of the art bulletproof hosting in a combination with cybercrime-friendly domain registrar.
In order to make it even harder for the security community to disrupt their campaigns, cybercriminals also implement the random domain name generation tactic. This makes it more difficult for researchers to assess and shut down their operations, as of all the randomly generated domains initiating “phone home” command and control server communications, only a few will actually respond and will be registered and operated by the cybercriminals behind the campaign.
In this post, I’ll profile a recently launched DIY malicious domain name registering/managing service which makes it easier for cybercriminals to manage their domains portfolios. The service allows them to register randomly generated domains in mass, instantly change IPs and Name Servers, and cross-reference with anti-spam checklists for verification of clean/flagged IPs.
More details:
Sample screenshot of the entry page for the service:
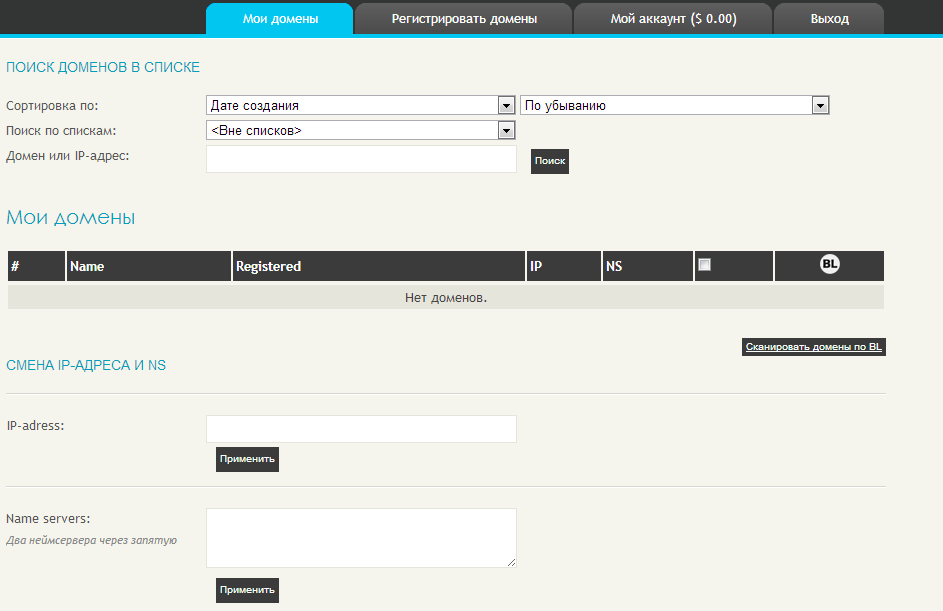
The service allows filtering of the domains database that you registered using the service, including a handy option from a cybercriminal’s perspective to check whether any of the domains has been flagged as malicious by multiple Black Lists.
Second screenshot of the service:
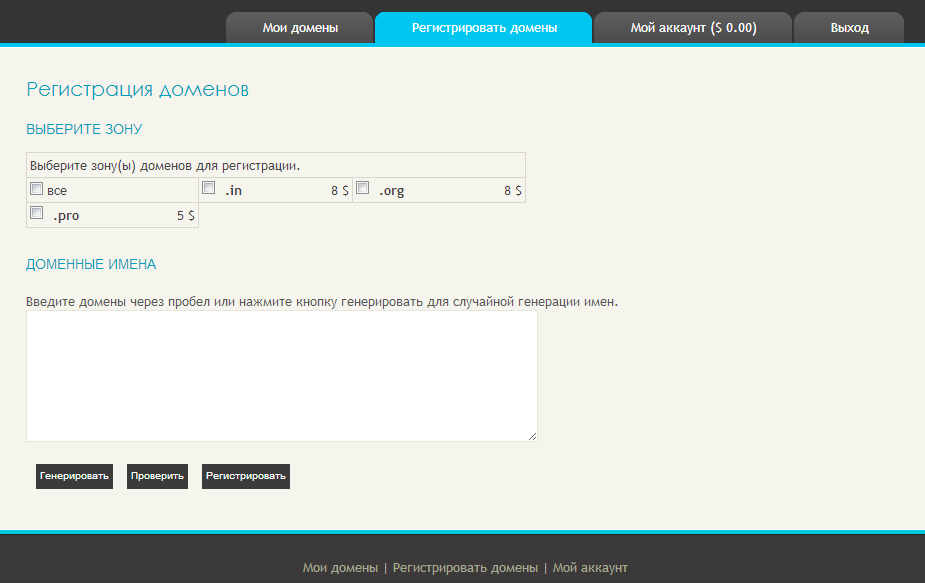
Next is the option allowing the cybercriminals to choose their TLD. For the time being, the service offers .in (for $8); .org (for $8); and .pro (for $5), as well as a combination of all of these TLDs.
Third screenshot of the service:
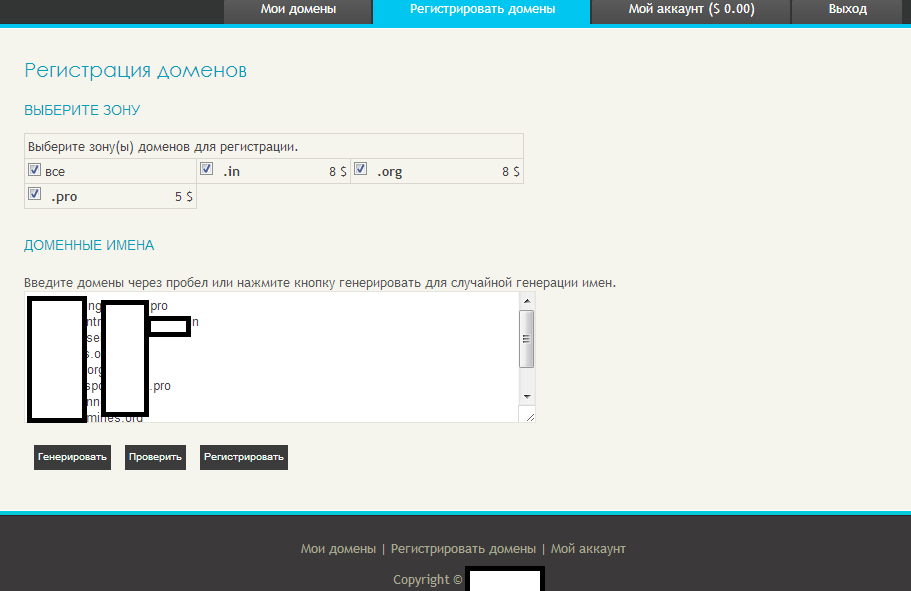
The service successfully generated a bunch of pseudo-random domains to be used in upcoming malicious campaigns.
Sample screenshot of the service in action:
Once the domains have been generated, the service offers an automatic “free domain” verification service, and naturally, all of the pseudo-randomly generated domains are free for registration and abuse:
We’ll continue monitoring the development of this trend, and post updates as soon as new services become available.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








Do the domain names have a common NS?
That would be useful to check to build a blacklist.
Did you try to register any or do you have a list of some of those running on this service?
Finding a trait like that can be interesting to create IDS rule(s)…
nice