Cybercriminals are currently mass mailing tens of thousands of emails, impersonating Chase in an attempt to trick its customers into executing the malicious attachment found in the fake email. Upon execution, the sample downloads additional malware on the affected hosts, and opens a backdoor allowing the cybercriminals behind the campaign complete access to the host.
More details:
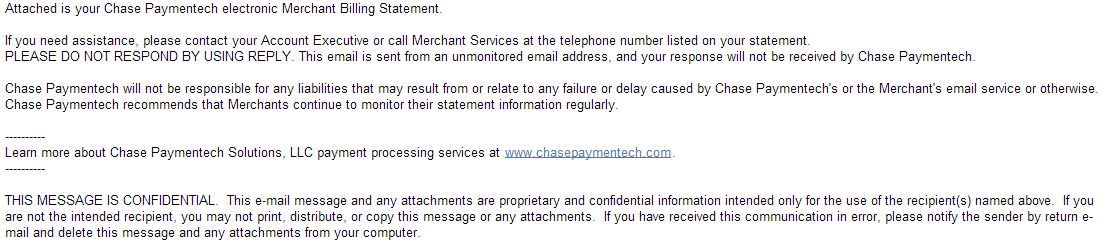
Sample screenshot of the spamvertised email:
We managed to intercept two separate campaigns launched by the same malicious party. What’s particularly interesting about the first is that, the cybercriminal/cybercriminals behind it applied low QA (Quality Assurance) since the actual filename found in the malicious archive exceeds 260 characters, resulting in a failed extraction process on Windows hosts.
“C:UsersWorkstationDesktopStatement_random_number.pdf.zip: Cannot create Statement_ID_random_number.pdf.exe
Total path and file name length must not exceed 260 characters. The system cannot find the path specified.”
Sample detection rate for the spamvertised attachment: MD5: 676c1a01739b855425f9492126b34d23 – detected by 42 out of 46 antivirus scanners as Trojan-PSW.Win32.Tepfer.cbrv.
The same MD5 is known to have downloaded two additional MD5s:
MD5: ED3C1D1EFC3789FABEDD630E3995F24B – detected by 35 out of 46 antivirus scanners as Trojan.Win32.Agent2.fjti
MD5: 6C7B44F2BC4FCF175C3CA5C0634E127C – detected by 30 out of 40 antivirus scanners as VirTool:Win32/Obfuscator.ACV
Upon execution, the sample attempts to download the following malicious executables:
hxxp://mjorart.com/jTc.exe
hxxp://bestinsighttours.com/bZ6.exe
hxxp://rdquark.com/cAB.exe
hxxp://quranaqiq.com/1kH.exe
hxxp://www.westquimica.com/AuNP5.exe
hxxp://www.superelectronico.com/cPY.exe
hxxp://www.jagatoko.com/W14C.exe
hxxp://muzikmeno.com/Y5m0Sx.exe
hxxp://eds-kurier.de/mpzna.exe
All of these files have an identical MD5 – MD5: 77d94b9d2fa0569ef5aecf1b93985d81 – detected by 34 out of 45 antivirus scanners as W32/Kryptik.ALRY!tr.
Upon execution, it creates the following files on the affected host:
%AppData%Labuguimuffo.exe – MD5: 567C27851F534F624279B6B97E8D6B44
%AppData%jianp.odq – MD5: C2327617D125D6612AF63D182C05F23B
%Temp%tmp06c81ac7.bat – MD5: FBE24DEE826D245D60EDC053B9A86B31
As well as the following process:
C:Documents and Settings<USER>Application DataIdukahowit.exe
To mark its presence on the system, the malware also creates the following Mutexes:
Global{CB561546-E774-D5EA-8F92-61FCBA8C42EE}
Local{744F300D-C23F-6AF3-8F92-61FCBA8C42EE}
Global{C517129D-E0AF-DBAB-0508-B06D3016937F}
Global{C517129D-E0AF-DBAB-7109-B06D4417937F}
Global{C517129D-E0AF-DBAB-490A-B06D7C14937F}
Global{C517129D-E0AF-DBAB-610A-B06D5414937F}
Global{C517129D-E0AF-DBAB-8D0A-B06DB814937F}
Global{C517129D-E0AF-DBAB-990A-B06DAC14937F}
Global{C517129D-E0AF-DBAB-350B-B06D0015937F}
Global{C517129D-E0AF-DBAB-610B-B06D5415937F}
Global{C517129D-E0AF-DBAB-B90B-B06D8C15937F}
Global{C517129D-E0AF-DBAB-1D0C-B06D2812937F}
Global{C517129D-E0AF-DBAB-410C-B06D7412937F}
Global{C517129D-E0AF-DBAB-690C-B06D5C12937F}
Global{C517129D-E0AF-DBAB-BD0D-B06D8813937F}
Global{C517129D-E0AF-DBAB-2D0E-B06D1810937F}
Global{C517129D-E0AF-DBAB-650E-B06D5010937F}
Global{C517129D-E0AF-DBAB-F508-B06DC016937F}
Global{C517129D-E0AF-DBAB-ED0B-B06DD815937F}
Global{C517129D-E0AF-DBAB-050D-B06D3013937F}
Global{C517129D-E0AF-DBAB-B90E-B06D8C10937F}
Global{C517129D-E0AF-DBAB-750F-B06D4011937F}
Global{C517129D-E0AF-DBAB-C90D-B06DFC13937F}
Makes DNS request to 3.soundfactor.org, then it establishes a TCP connection with 184.184.247.60:14511, as well as UDP connections to the following IPs:
184.184.247.60:23089
99.124.198.193:13197
78.93.215.24:14225
68.167.50.61:28650
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Hello! I’m at work browsing your blog from my neew iphone 3gs!
Just wantred to say I love reading your blog and look forward
to all your posts! Carryy on the superb
work!