Despite the fact that on the majority of occasions cybercriminals tend to rely on efficient and automated exploitation techniques like the ones utilized by the market leading Black Hole Exploit Kit, they are no strangers to good old fashioned ‘visual social engineering’ tricks. Throughout 2012, we emphasized on the emerging trend of using malicious DIY Java applet distribution tools for use in targeted attacks, or widespread campaigns.
Is this still an emerging trend? Let’s find out. In this post, I’ll profile one of the most recently released DIY Java applet distribution platforms, both version 1.0 and version 2.0.
More details:
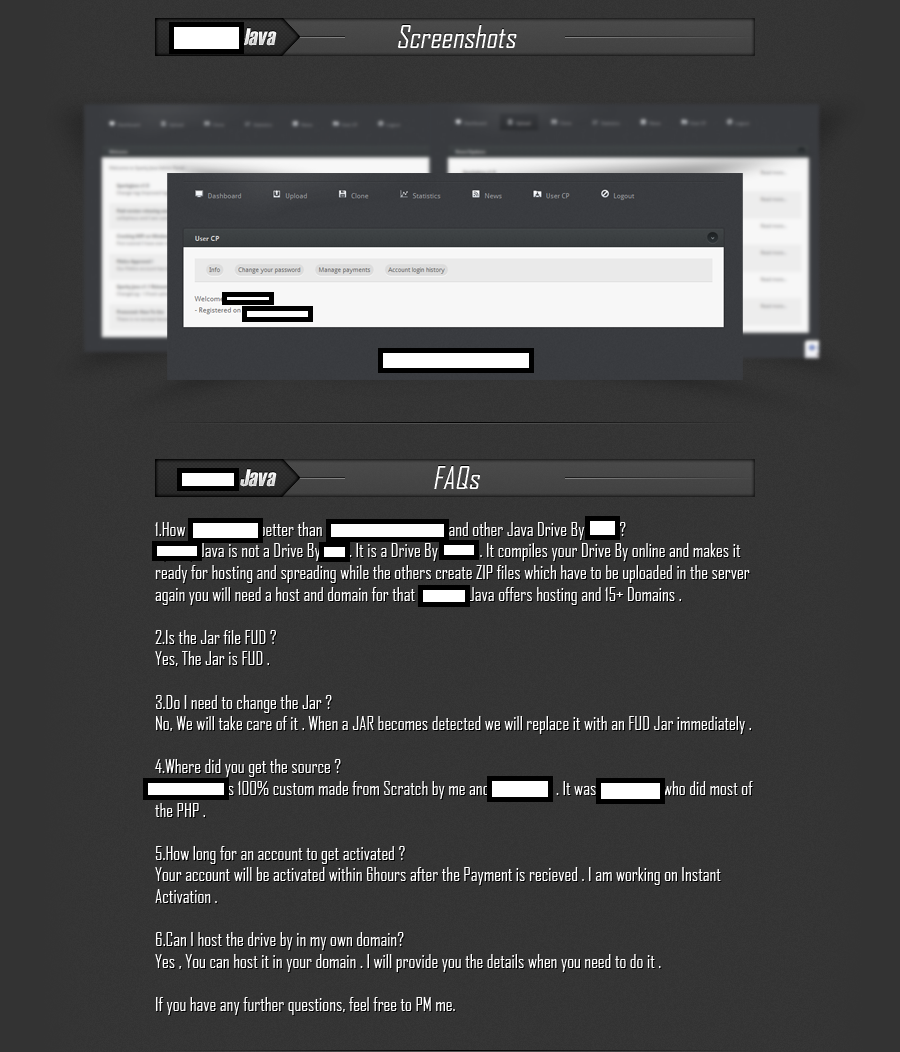
Sample description of the platform:
The command and control interface of version 1.0:
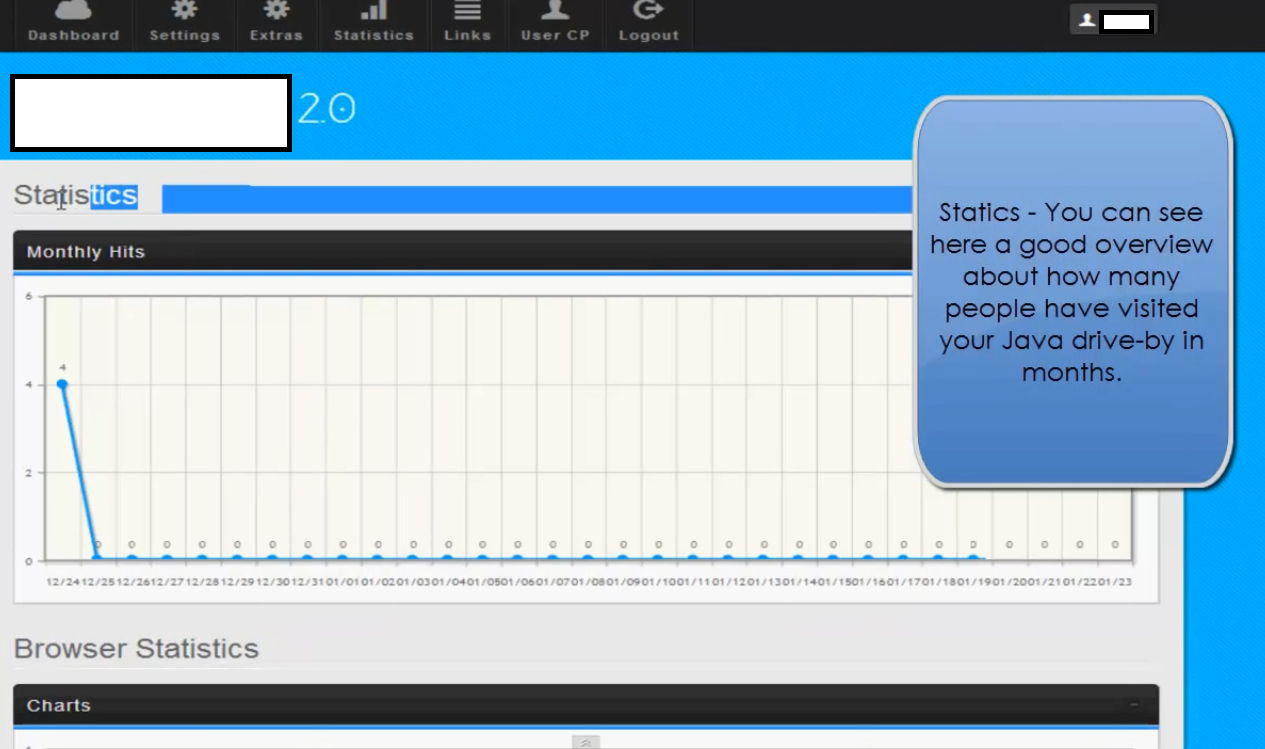
The statistics page of version 1.0:
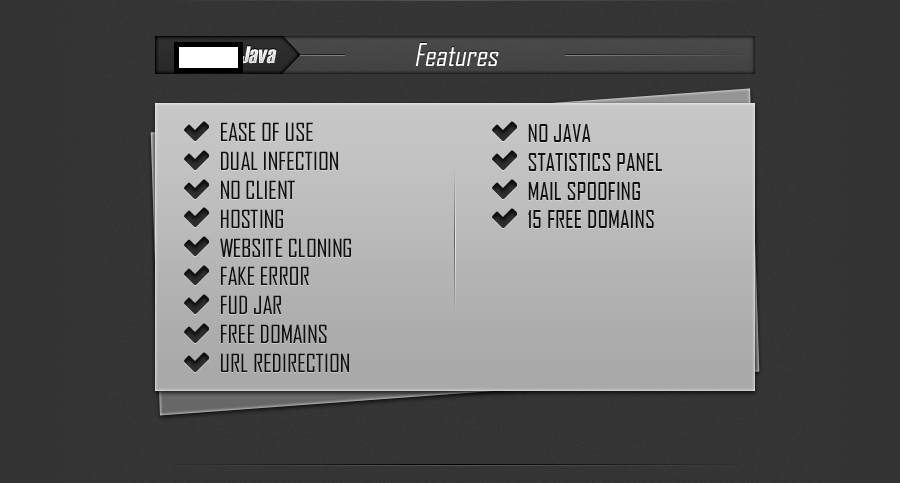
Version 1.0 is offered as a fully managed cybercrime-friendly service, including monitoring of the detection rate for the static JAR applet, and the introduction of a new, undetected JAR applet within the managed service. It also offers the feature to create a clone of any given URL, for the purpose of brandjacking any company or web site, in an attempt to trick the potential victims into thinking that the Java applet is served from a legitimate web site. The package, offered for sale at $30 for a lifetime license, also offers 15 pre-registered domains which the customers can use when launching their attacks. Naturally, they can also use their own domains/servers.
Domains known to have participated in campaigns used by this DIY platform:
facebookpassgen.info – Email: kvyn.14@gmail.com
freejavagaming.info – Email: kvyn.14@gmail.com
javawebcamchat.info – Email: kvyn.14@gmail.com
minecraftpassgen.info – Email: kvyn.14@gmail.com
serialsforyou.info – Email: kvyn.14@gmail.com
teengirlslive.info – Email: kvyn.14@gmail.com
runescapeclient.info – Email: kvyn.14@gmail.com
ffxivideos.in – Email: superhero619@gmail.com
javagamesonline.in – Email: superhero619@gmail.com
javavideochat.in – Email: superhero619@gmail.com
freejargames.in – Email: superhero619@gmail.com
javawebchat.in – Email: superhero619@gmail.com
Now let’s take a peek at version 2.0, the most recent version of the platform.
Sample command and control interface for version 2.0:
Sample Java Applet served to potential victims:
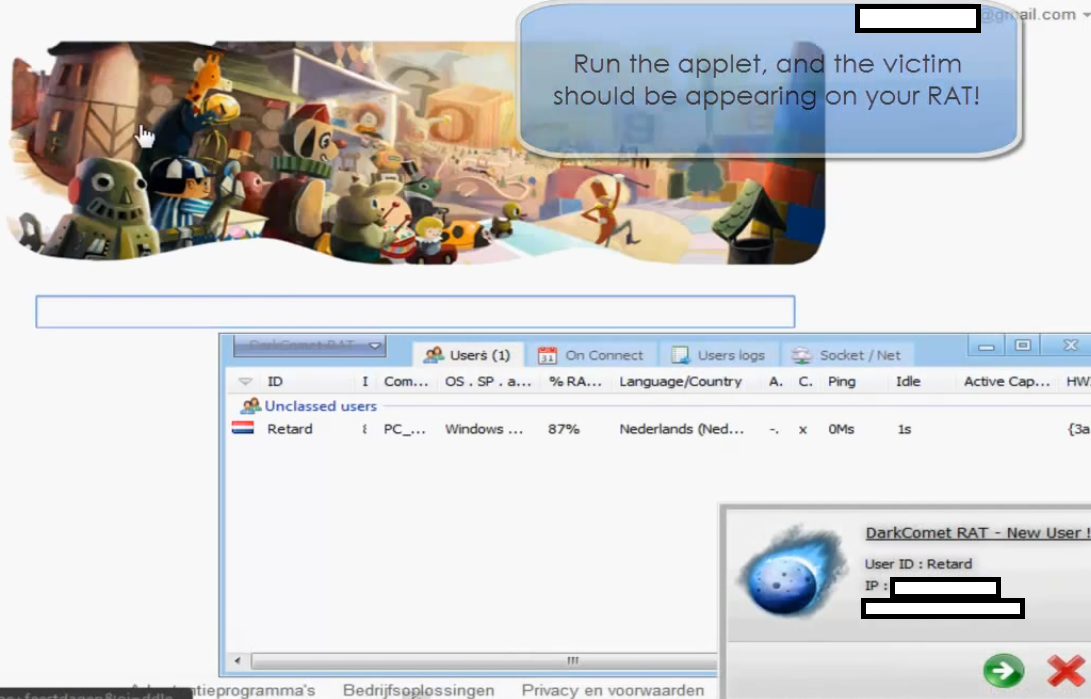
Running it automatically results in a successful infection, like the following courtesy of a sample tutorial explaining the features of the platform:
As you can see in the attached screenshots, version 2.0 offers two extra features – a Skype IP resolver and a stress tester for a particular web site. The cybercriminals using it have full control over the description of the malicious applet. Thanks to the visually appealing domain names offered by the service, it shouldn’t be surprising that a lot of users will fall victims to this one.
We’ll continue monitoring the development of this trend, and post updates as soon as new developments emerge.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.