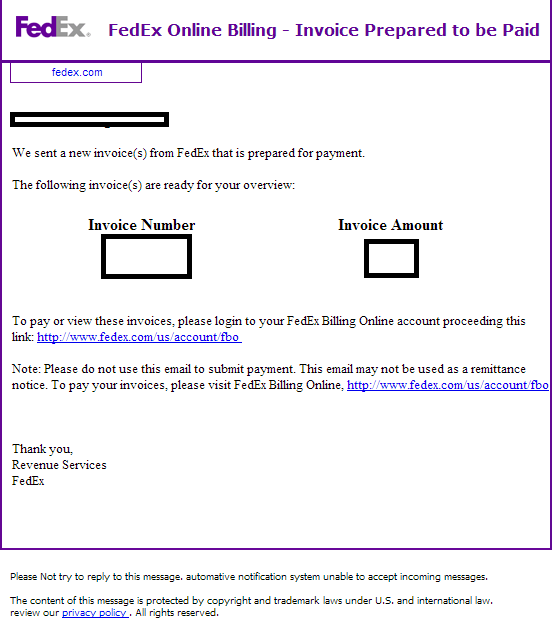
Users of FedEx’s Online Billing service, watch out!
Cybercriminals are currently mass mailing tens of thousands of emails impersonating the company, in an attempt to trick its customers into clicking on exploits and malware dropping links found in the legitimate-looking emails.
More details:
Sample screenshot of the spamvertised email:
Sample client-side exploits serving URL: hxxp://vespaboise.net/detects/invoice_overview.php
Sample malicious payload dropping URL: hxxp://vespaboise.net/detects/invoice_overview.php?
yhrknjt=30:33:1n:1o:33&fjjme=32:30:1j:32:32:33:1h:1g:31:1n&bdadxnvt=1i&jvz=lwcss&ymg=nbvjlip
Malicious domain name reconnaissance:
vespaboise.net – 222.238.109.66 – Email: blackchromedesign2@ymail.com
Name Server: NS1.HTTP-PAGE.NET
Name Server: NS2.HTTP-PAGE.NET
Responding to the same IP (222.238.109.66) are the following malicious domains:
morepowetradersta.com
kendallvile.com
alphabeticalwin.com
ehadnedrlop.com
postofficenewsas.com
paralertamastaercet.com
prepadav.com
masterseoprodnew.com
asmncm.co
lo4inee.asmncm.co
reta4ilse.asmncm.co
gonita.net
able-stock.net
duriginal.net
euronotedetector.net
fx-points.net
africanbeat.net
ensconcedattractively.biz
We’ve already seen the same IP (222.238.109.66) and name servers used in the following previously profiled malicious campaigns, indicating that they’ve been launched by the same party:
- Fake ‘ADP Speedy Notifications’ lead to client-side exploits and malware
- Bogus ‘Your Paypal Transaction Confirmation’ themed emails lead to Black Hole Exploit Kit
- Fake LinkedIn ‘Invitation Notifications’ themed emails lead to client-side exploits and malware
Upon successful client-side exploitation, the FedEx themed campaign drops MD5: c2f72ff5b0cf4dec4ce33e4cc65796b1 – detected by 22 out of 46 antivirus scanners as PWS:Win32/Zbot.gen!AM.
Once executed, the sample creates the following files on the affected hosts:
C:Documents and Settings<USER>Application DataAlyszkiotp.exe
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Temptmp5600c543.bat
It also creates the following mutexes:
Global{5B039399-8854-D5EB-89D3-085A9A492B48}
Global{DE680959-1294-5080-7788-B06D6412937F}
Global{A45A65F1-7E3C-2AB2-89D3-085A9A492B48}
The following Registry Keys:
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftYnumav
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWABWAB4Wab File Name
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoft
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWAB
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWABWAB4
REGISTRYMACHINESYSTEMCurrentControlSetServicesSharedAccessParametersFirewallPolicyStandardProfileGloballyOpenPortsList
REGISTRYMACHINESYSTEMControlSet001ServicesSharedAccessParametersFirewallPolicyStandardProfile
REGISTRYMACHINESYSTEMControlSet001ServicesSharedAccessParametersFirewallPolicyStandardProfileGloballyOpenPorts
It also attempts to connect to the following IPs:
14.96.171.173
64.219.114.114
68.49.120.165
70.50.58.41
70.136.9.2
71.42.56.253
71.43.217.3
72.218.14.223
76.219.198.177
80.252.59.142
83.111.92.83
87.5.135.46
87.203.87.232
98.71.136.168
98.245.242.245
108.83.233.190
115.133.156.53
151.66.19.166
194.94.127.98
206.45.59.85
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.