On a daily basis, we continue to observe the emergence of the DIY (do-it-yourself) trend within the entire cybercrime ecosystem. And although the DIY activity cannot be compared to the malicious impact caused by “cybercrime-as-a-service” managed underground market propositions, it allows virtually anyone to enter the profitable world of cybercrime, thanks to the ongoing leaks of proprietary malware generating tools and freely available alternatives.
In this post, I’ll profile the latest version of a Russian DIY password stealing malware that’s targeting multiple browers, Email, IM, FTP clients, as well as online poker clients.
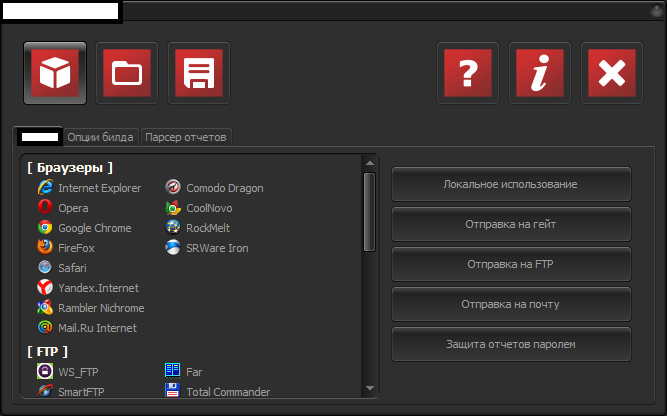
Sample screenshot of the DIY password stealing malware:
As you can see in the attached screenshot, the malware has support for all the major Web browsers, including several highly popular Russian browsers.
Second screenshot of the DIY password stealing malware:
In addition to Web browsers, the malware also supports multiple IM clients, Email clients, FTP clients, and several other applications like Windows RAS, RDP, World ofTanks, Full Tilt Poker and PokerStars.
Third screenshot of the DIY password stealing malware:
The DIY interface allows full customization of the malware that’s about to be generated, including the appearance of the file, downloader functionality, and naturally, anti-reverse engineering capabilities.
Fourth screenshot of the DIY password stealing malware:
What’s particularly interesting about this DIY tool is the fact that it encrypts the stolen data using a public and private key, allowing the cybercriminal behind the campaign to securely store the compromised data on any public service such as a (compromised) FTP server, or an email account.
Fifth screenshot of the DIY password stealing malware:
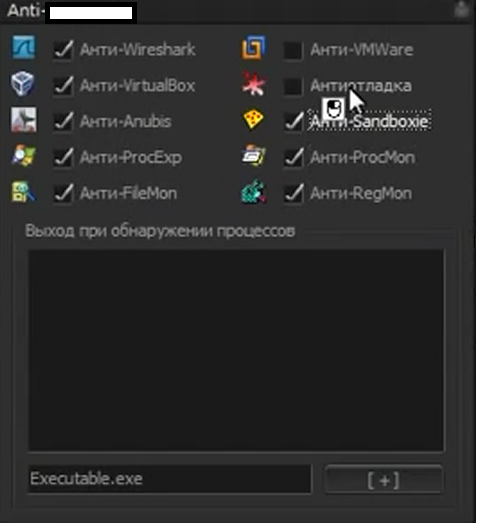
To make it harder to analyze, the DIY password stealing malware generator has built-in fuctions enabling its user to choose which “Anti” modules will be enabled in the malware variant about to be generated. It currently covers:
- Anti-Wireshark
- Anti-VirtualBox
- Anti-Anubis
- Anti-ProcExp
- Anti-FileMon
- Anti-VMWare
- Anti-Sandboxie
- Anti-ProcMon
- Anti-RegMon
Sixth screenshot of the DIY password stealing malware:
Once the cybercriminal enters the correct pseudo-randomly generated unlock code, he gains immediate access to the compromised data.
A logical question emerges in the minds of Webroot SecureAnywhere users – what happens if we fail to detect a malware sample generated by this tool? Watch this informative video, and find out more.
We’ll continue monitoring the emergence of the DIY trend, and post updates as soon as we discover more tools used to facilitate cybercrime, and lower the entry barriers into the world of cybercrime.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.