Kindle owners, watch what you click on!
Cybercriminals are currently attempting to trick Kindle owners into thinking that they’ve received a receipt from an E-book purchase from Amazon.com. In reality, when users click on any of the links found in the malicious emails, they’re automatically exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details:
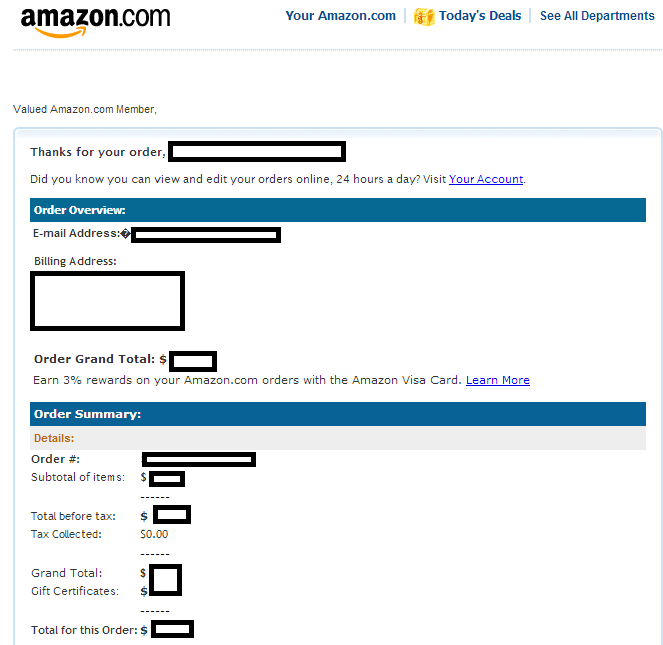
Sample screenshot of the spamvertised email:
Sample compromised URLs used in the campaign:
hxxp://fatlossfactorscams.com/wp-content/plugins/tell-a-friend/orderedlistamazon.html
hxxp://v-mishchenko.com/wp-content/plugins/tell-a-friend/orderedlistamazon.html
hxxp://pasadenacaregiver.com/wp-content/plugins/tell-a-friend/orderedlistamazon.html
Sample client-side exploits serving URL:
hxxp://starsoftgroup.net/detects/weeks_movie_whether.php
Sample malicious payload dropping URLs:
hxxp://starsoftgroup.net/detects/weeks_movie_whether.php?jf=31:2v:33:1o:1m&le=2w:2v:1o:1g:1m:31:1l:1k:30:1k&s=1f&tf=s&kv=r
hxxp://starsoftgroup.net/detects/weeks_movie_whether.php?uf=2v:1i:1h:31:1o&he=2w:2v:1o:1g:1m:31:1l:1k:30:1k&f=1f&kr=t&bp=y
Malicious domain name reconnaissance:
starsoftgroup.net – 175.121.229.209; 198.144.191.50 – Email: wondermitch@hotmail.com
Name Server: NS1.HTTP-PAGE.NET
Name Server: NS2.HTTP-PAGE.NET
We’ve already seen the same name servers used in the following previously profiled campaigns, indicating that they’ve been launched by the same cybercriminals:
- Fake ‘FedEx Online Billing – Invoice Prepared to be Paid’ themed emails lead to Black Hole Exploit Kit
- Fake LinkedIn ‘Invitation Notifications’ themed emails lead to client-side exploits and malware
- Bogus ‘Your Paypal Transaction Confirmation’ themed emails lead to Black Hole Exploit Kit
Upon successful client-side exploitation, the campaign drops MD5: 13d23f4c1eb1d4d3841e2de50b1948cc – detected by 7 out of 46 antivirus scanners as UDS:DangerousObject.Multi.Generic.
Once executed, the sample creates the following processes on the affected hosts:
C:WINDOWSsystem32cmd.exe” /c “C:DOCUME~1<USER>~1LOCALS~1Tempexp1.tmp.bat
C:Documents and Settings<USER>Application DataKB00927107.exe
The following Registry Keys:
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTS9CC20790
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTCBA6D3F36
As well as the following Mutexes:
LocalXMM000001C4
LocalXMI000001C4
LocalXMM00000380
LocalXMI00000380
Upon execution, the sample also phones back to the following C&C servers:
hxxp://195.191.22.90:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
hxxp://37.122.209.102:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
hxxp://217.65.100.41:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
hxxp://173.201.177.77/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://210.56.23.100/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://213.214.74.5/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://180.235.150.72/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
We’ve already seen the same pseudo-random C&C communication characters (DPNilBA) used in the following campaigns:
- Cybercriminals spamvertise millions of FDIC ‘Your activity is discontinued’ themed emails, serve client-side exploits and malware
- Malicious ‘Sendspace File Delivery Notifications’ lead to Black Hole Exploit Kit
- ‘Batch Payment File Declined’ EFTPS themed emails lead to Black Hole Exploit Kit
- ‘Please confirm your U.S Airways online registration’ themed emails lead to Black Hole Exploit Kit
- Cybercriminals resume spamvertising ‘Payroll Account Cancelled by Intuit’ themed emails, serve client-side exploits and malware
- Fake Intuit ‘Direct Deposit Service Informer’ themed emails lead to Black Hole Exploit Kit
- Spamvertised AICPA themed emails serve client-side exploits and malware
As well as the same C&C server IPs (173.201.177.77; 210.56.23.100; 180.235.150.72) in the following campaigns, indicating that they’ve been launched by the same malicious party:
- ‘Batch Payment File Declined’ EFTPS themed emails lead to Black Hole Exploit Kit
- Fake ‘ADP Speedy Notifications’ lead to client-side exploits and malware
- Spamvertised American Airlines themed emails lead to Black Hole exploit kit
- ‘American Express Alert: Your Transaction is Aborted’ themed emails serve client-side exploits and malware
- Bogus IRS ‘Your tax return appeal is declined’ themed emails lead to malware
- ‘Please confirm your U.S Airways online registration’ themed emails lead to Black Hole Exploit Kit
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.