Thanks to basic disruptive factors like standardization, DIY (do it yourself) underground market releases, Cybercrime-as-a-Service “value added” propositions, efficiency-centered client-side exploitation process, QA (Quality Assurance), and adaptation to the ubiquitous endpoint protection mechanisms, such as for instance, signatures-based antivirus scanning, the cybercrime ecosystem is currently enjoying the monetary joys of its mature state.
In this post, I’ll profile a recently advertised DIY IRC-based DDoS bot, with an emphasis on how market followers, like the author of the bot, attempt to steal market share from the competition. Successful or not, this trend has been taking place for years, and based on the positive type and number of “satisfied customer” comments for this bot, market followers can also secure a revenue stream thanks to the fact that the prospective buyers of such “me too” type of malicious software releases don’t know where to acquire the latest cutting-edge DIY DDoS bot technology from.
More details:
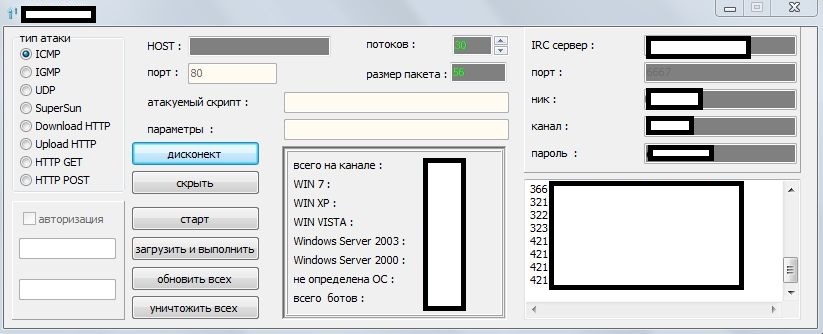
Sample screenshot of the DIY IRC-based DDoS bot in action:
What is the first thing that grabs your attention when you look at the administration application? It’s not the diversified set of DDoS attack types that the bot supports, but the fact that, in 2013, it’s still using the Internet Relay Chat (IRC) as a centralized command and control infrastructure. What’s also worth emphasizing is that the coder of the bot would not offer you access to a managed IRC server to be used as command and control server, even if you purchase the bot.
While the competition is working on pseudo-random domain name generation, limiting the levels of multi-casting, and is increasingly phoning back to legitimate domains in an attempt to trick network administrators into thinking that the malware-infected hosts are generating legitimate traffic, the author of this IRC-based bot appears to be using a largely outdated and easily detected C&C communication process.
The bot is written in C++ and the size of a sample malware — according to the bot’s coder — is 23kb. It has the standard anti-debugging mechanisms built-in, plus features allowing the botnet master to update the bot to a newer version, plus take advantage of a diversified set of DDoS attack types, which you can see in the attached screenshot. With or without these “innovations”, the bot’s future is (thankfully) at stake due to the use of an outdated command and control communication process.
We’ll continue monitoring the development of this bot, in particular whether or not the author will migrate to a modern command and control communication alternative, and post updates as soon as new developments emerge.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.