

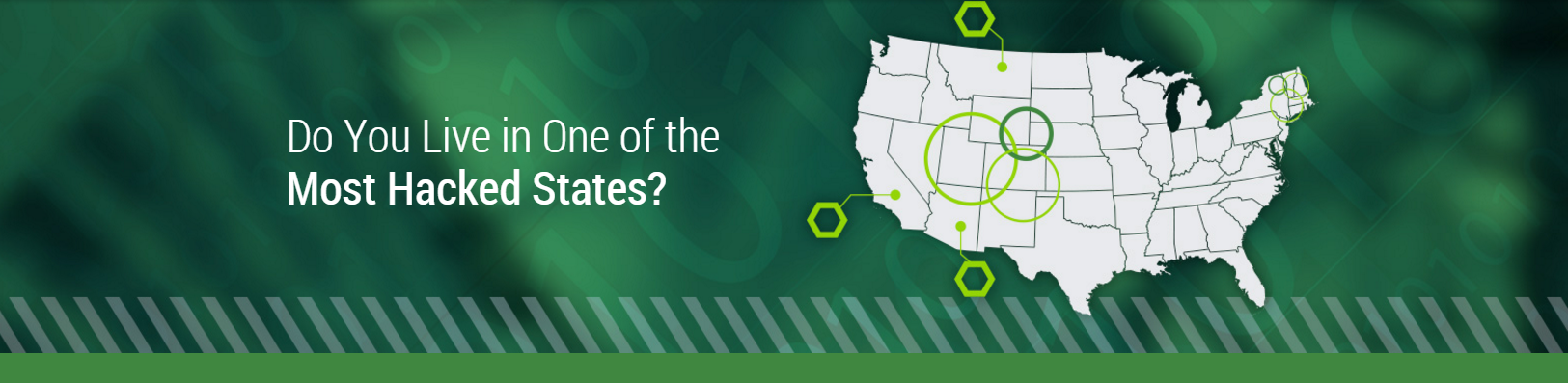
Love the City You Live In? So do Cybercriminals!
Reading Time: ~ < 1 min.
What you need to know about the new KeRanger Ransomware.
Reading Time: ~ 3 min.
Cyber Threat Actors
Reading Time: ~ 2 min.
Female PC gamers and Online Security
Reading Time: ~ < 1 min.
Webroot’s Acceleration with Advancement of IoT
Reading Time: ~ 3 min.
Cleaning up your Mac
Reading Time: ~ 3 min.
Quick Tips to Protect Your New (and old) Apple Devices
Reading Time: ~ 3 min.
What are the security risks with using a router provided by your ISP?
Reading Time: ~ 2 min.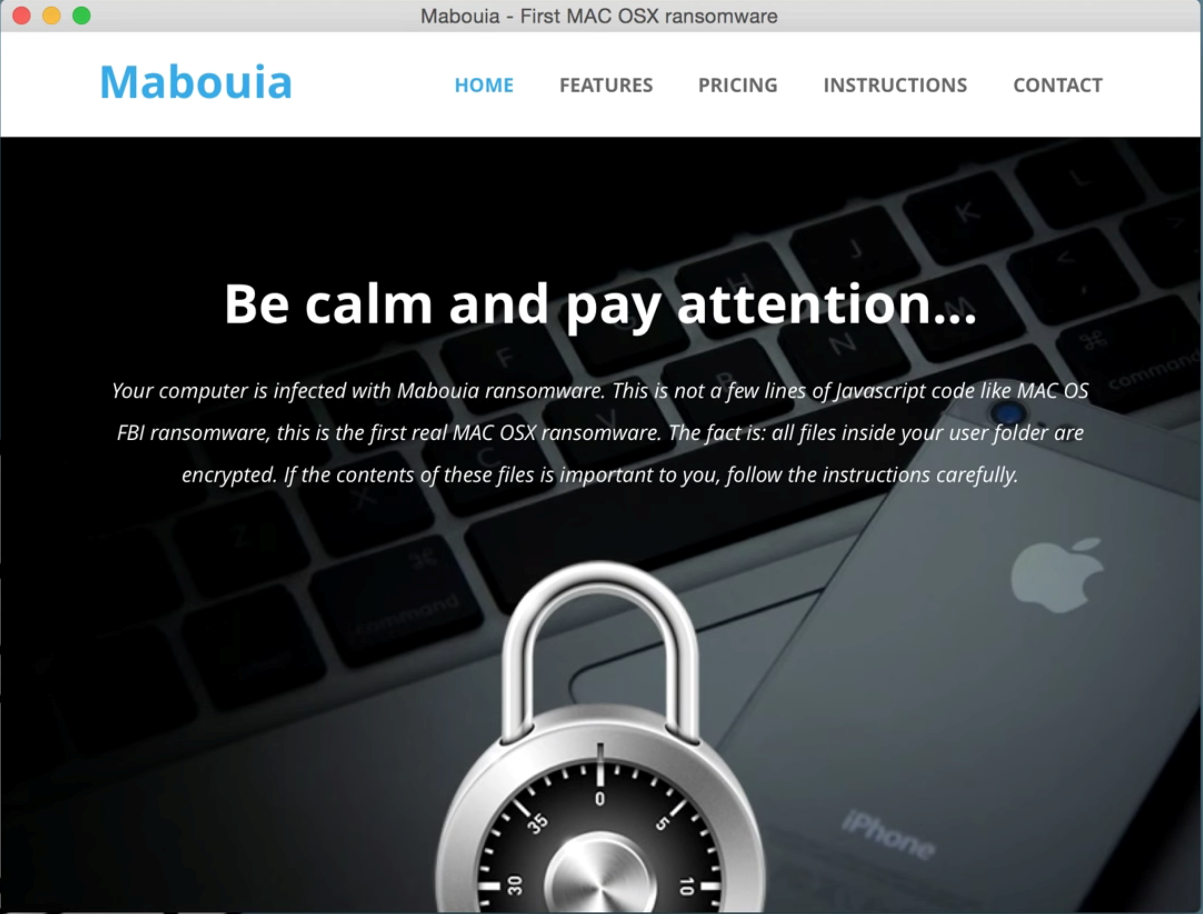
Is 2015 the Year of Mac Malware?
Reading Time: ~ 2 min.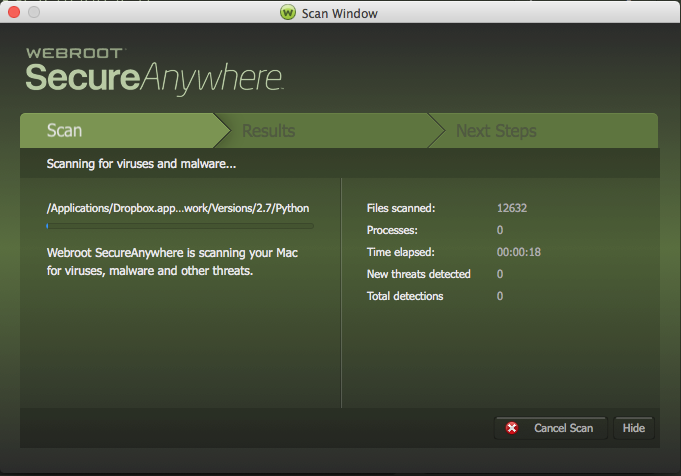
Are antivirus testing scores a true reflection of our Mac product efficacy? You decide…
Reading Time: ~ 3 min.





