Banking Trojan Shuts Down Ohio School District
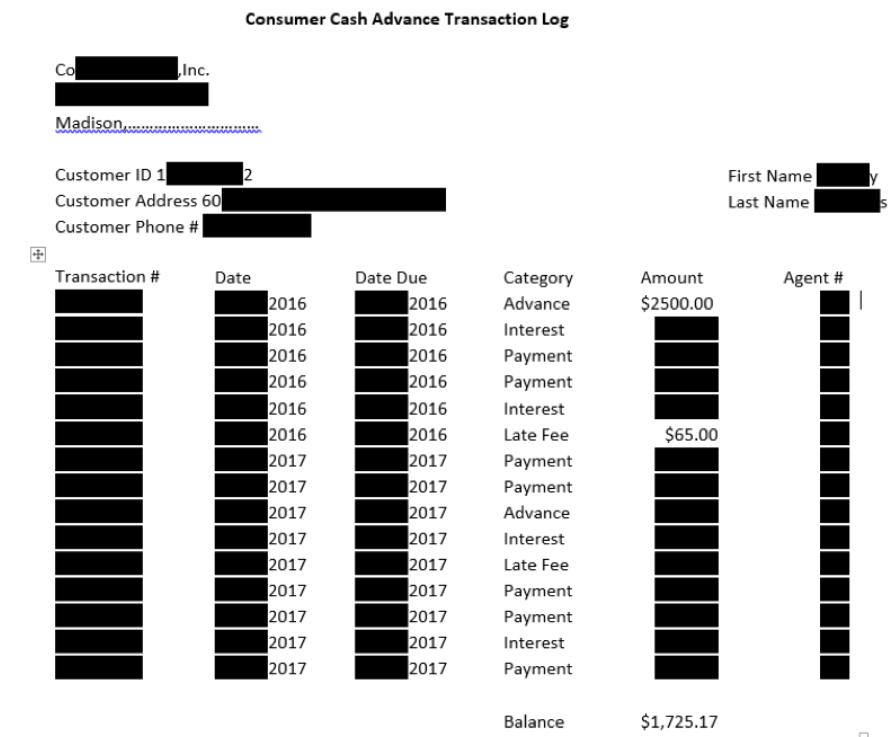
After the discovery of the banking Trojan known as Trickbot, an Ohio school district was forced to cancel school since they were unable to fully disinfect the networks before classes resumed the following Monday. Preliminary reports have concluded that no students were responsible for the attack, as it appears to have started its data-gathering on a computer belonging to the district treasurer’s office. In order for classes to resume normally, the IT staff for the district had to re-format nearly 1,000 affected computers.
GetCrypt Spreading Through RIG Exploit Kits
Another ransomware variant, GetCrypt, has been spotted in the wild that spreads itself across systems by redirecting visitors to a compromised website to a separate page hosting an exploit kit. After checking for several Eastern European languages, the ransomware begins encrypting all files on the system and displays a standard ransom note. In addition to removing all available shadow copies from the computer, GetCrypt also appends all encrypted files with a randomized, four-character string based on the CPUID of the device itself.
Google Assistant Logs All Online Purchases
It was recently discovered that Google’s Assistant, released last year, keeps a log of all online purchases for which a receipt was sent to the user’s Gmail account. The “Payments” page on a user’s Google account shows transactions, flight and hotel reservations, and other purchases made up to several years prior, even showing the cost, date, and time of the purchase.
Forbes Joins List of Magecart Victims
It was revealed late last week that Forbes had fallen victim to a Magecart attack possibly affecting anyone who made a purchase on the site during that time. Fortunately, the researcher who discovered the attack quickly notified both Forbes and the domain owner, resulting in a swift removal of the malicious payment card skimmer from the highly-trafficked site. It’s likely that Forbes became a victim after another vendor in their supply chain was compromised.
Australian IT Contractor Arrested for Cryptomining
An IT contractor working in Australia was arrested after being caught running cryptomining software on government-owned computers, which netted him over $9,000 in cryptocurrency. The charges encompass misuse of government systems by making modifications to critical functions and security measures for personal gain while in a position of trust. By making these changes, this contractor could have exposed a much larger portion of the network to malicious actors who take advantage of misconfigured settings to access company data.