[Updated June 29, 2017, 10:20 a.m. MDT]
A host of companies across industries have confirmed attacks today by a brutal wave of ransomware, including global law firm DLA Piper, U.S. pharmaceutical giant Merck, and the Danish shipping company Maersk. Although targets originally appeared in Ukraine—shutting down power plants, banking services and supermarkets—this latest cyberattack has quickly spanned critical economic sectors around the globe.
Webroot customers are protected against this variant. This cyberattack was first seen by our threat research team at roughly 10:00 a.m. UTC on June 27, 2017.
What we know
Webroot’s threat researchers have confirmed that this ransomware is a variant of an older attack dubbed Petya, except this time the attack uses EternalBlue to target Windows systems—the same exploit behind the infamous WannaCry attack. While this variant appears to be an upgraded version of Petya, there is no confirmation that this attack is from the same author.
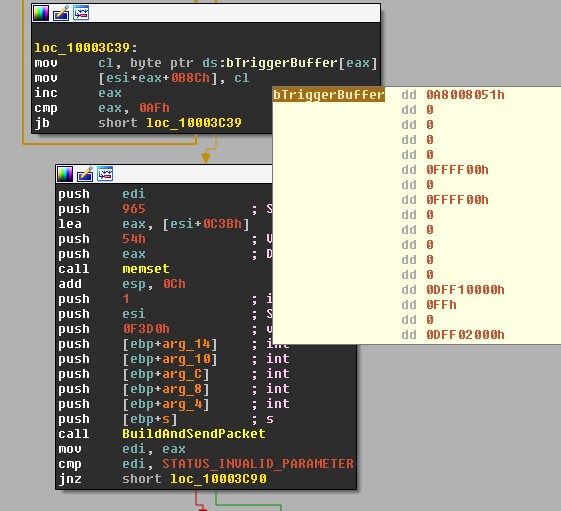
This variant mirrors Petya in that it encrypts the Master File Table (MFT) by overwriting the bootloader code, though unlike previous versions, it encrypts files based on file extension. The system fails to boot as usual and the end user instead sees a screen that appears similar to DOS and demands payment. The shot below depicts the preparation of the EternalBlue triggering packet.
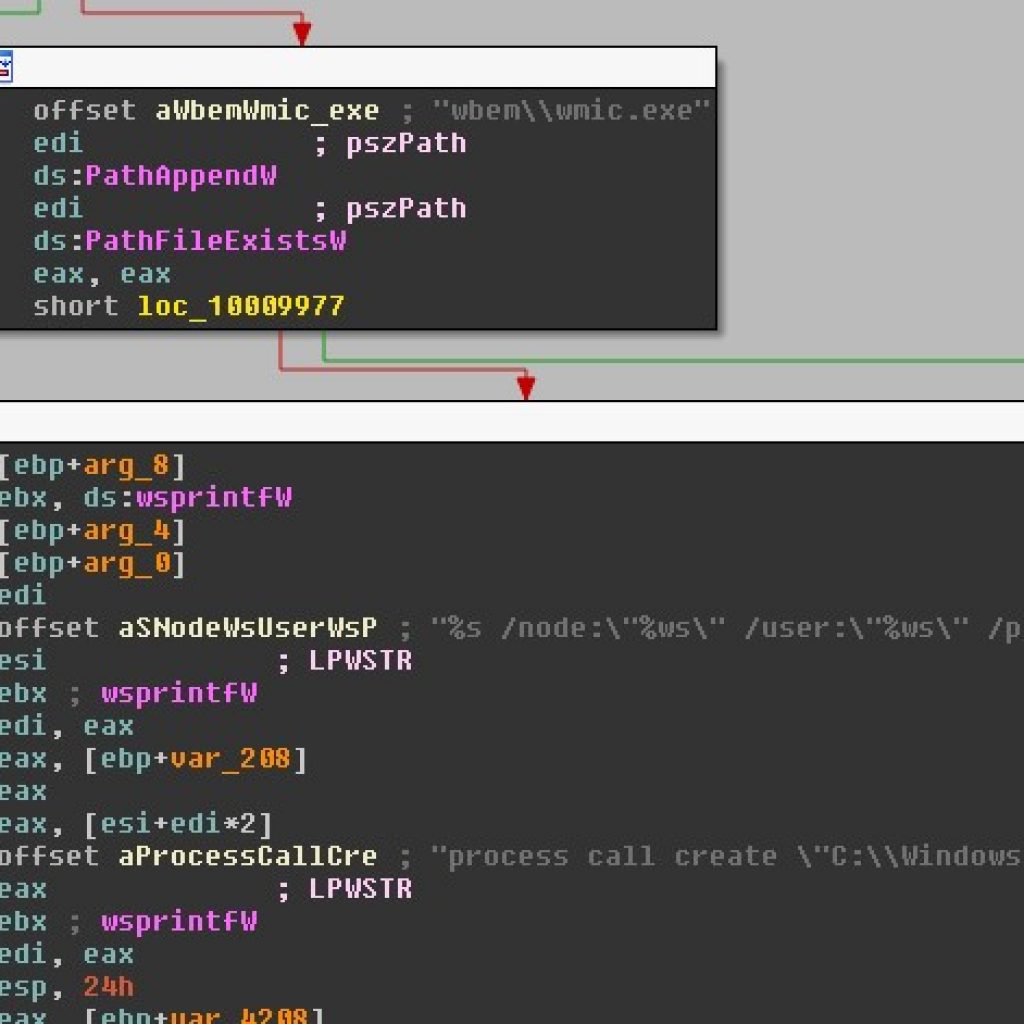
This is the same attack vector that made WannaCry so effective, but we have also observed additional techniques used to infect more machines.
Here we can see that the worm is also utilizing WMI (Windows Management Instrumentation) in a technique to further reach through the network using credentials siphoned from the local machine.
Once the machine is infected, the computer will immediately restart to what looks like a ‘chkdsk,’ but isn’t. Below is an image from Ukrainian Prime Minister Pavlo Rozenko’s Facebook showing the world what the ransomware looks like while it encrypted his computer during this fake chkdsk stage.
Vice Prime Minister of Ukraine, Павло Розенко (Pavlo Rozenko) on Facebook. This is what Petya looks like when it’s encrypting your drive. pic.twitter.com/RgPtfuWK7p
— Mikko Hypponen (@mikko) June 27, 2017
This stage is the ransomware encrypting files on your hard drive. We found that the ransomware doesn’t encrypt the entirety of your files with matching extensions, but instead encrypts up to the first mebibyte of data. This is done presumably to save time during the encryption process, but also ensures that enough of the file is encrypted to be unlikely to restore without paying the ransom.
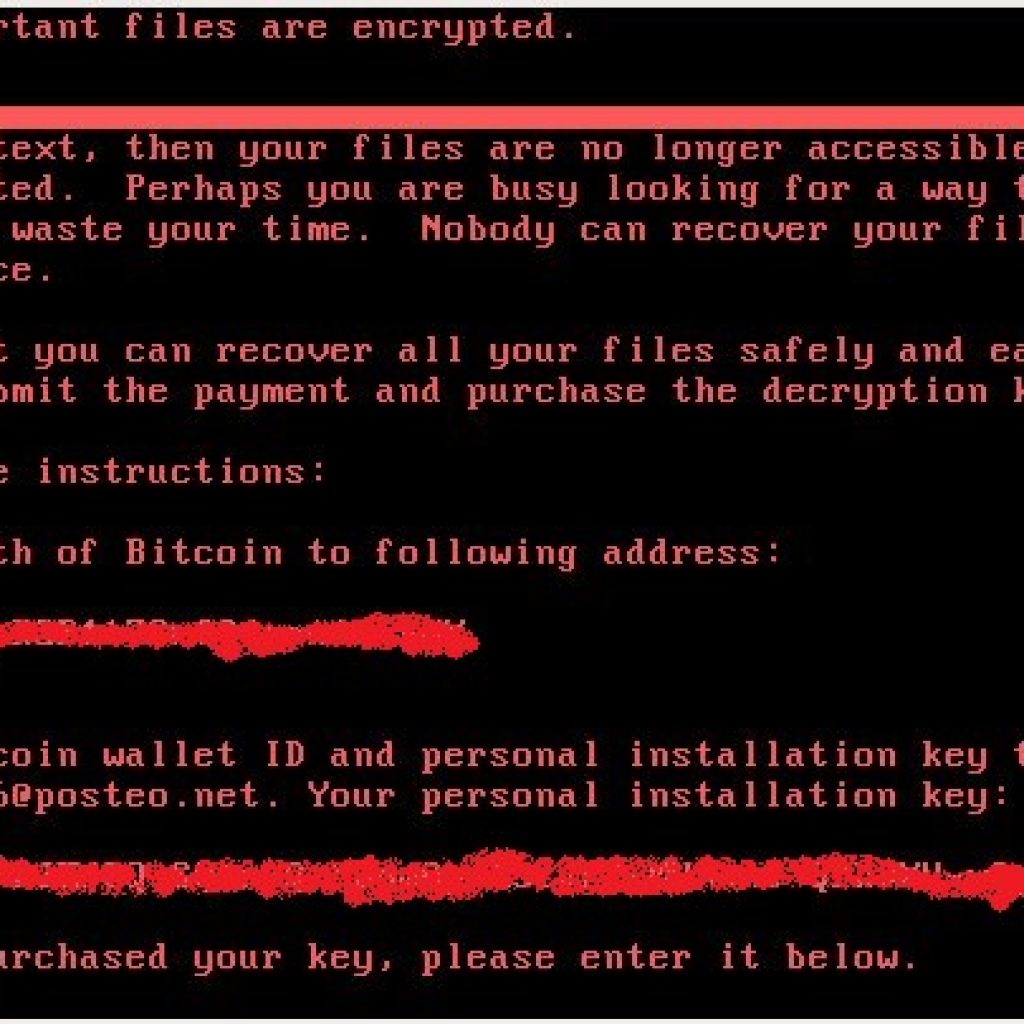
Once the fake chkdsk is complete (or all the files on the computer are encrypted) the infection will reboot the computer once more to this screen:
There is no way for a victim to retrieve their files other than to email the cybercriminal after paying the bitcoin address listed in the ransom. In fact, the email address listed in the ransom has, as of now, been shut down by the email provider. Essentially, this means victims are unable to get their files back, even after paying the ransom, as the payload author is now prevented from checking this email.
It now seems the attack’s intended effect was not to generate ransom payments at all. In a detailed post on the Microsoft Malware Protection Center blog, the initial route of infection was revealed to be a malicious update to tax accounting software deployed by the Ukrainian company M.E.Doc.
Given the initial attack vector and level of sophistication, the underlying motive appears to be aimed at wreaking the maximum amount of disruption in Ukrainian infrastructure, while merely operating under the guise of ransomware. This suspicion is supported by the absence of a payment portal or functional email address to deliver the ransom payment.
Why it matters
The bottom line is that companies are still failing to adequately secure their IT systems from the EternalBlue vulnerability in the Windows Server Message Block (SMB) server.
Microsoft issued critical security updates to patch this vulnerability on March 14, 2017. To verify that the MS17-010 patch is installed, follow the directions in this Microsoft support article.
If you’d like to learn more about this Petya-based attack, catch the replay of my webinar: Deep Dive into Petya-based & WannaCry Ransomware Attacks.
An interesting tidbit
Our threat researchers have determined that this infection includes a check to see if a file named “perfc” or “perfc.dat” exists in the Windows root directory before executing (a kill switch of sorts). Of course, the best “kill switch” is to perform updates that patch known vulnerabilities such as EternalBlue.