Chatting with David Dufour, senior director of engineering, Webroot, is always interesting. Quite frankly, so is pinning him down for a short Q+A about his experience at RSA 2017. One thing I could be sure of, though, was David having an opinion and being a straight shooter. As a first time attendee, I was curious to know what trends a veteran like David noticed and what were some highlights for him.
Webroot: You’ve been attending RSA for a number of years now. What were your expectations going into RSA 2017?
David Dufour: In my experience, RSA would never be confused with a pure play security conference like Black Hat simply because of all the hype and marketing spin, and this year did not disappoint. Going into the conference, it was apparent that Artificial Intelligence was going to be the big buzzword, with all exhibitors talking about how advanced their AI implementations were. The fun always starts when you pin many of these vendors down on exactly what AI means in their environment- how they’ve implemented it and what struggles they’ve had going to market with AI based solutions. This typically results in a glazed stares that leads to an eye twitch indicating they are finding a way to get rid of me.
“There continues to be significant advances in technology that help prevent malware both at the endpoint and in the network.”
What did you experience on the show floor?
Webroot had a prominent spot in the South Hall this year where the atmosphere seems more cutting edge than the North hall that usually hosts traditional security providers. I prefer to cut through the buzzwords and noise to get to the significant trends in the industry. Malware prevention, detection and remediation continues to be the least sexy, yet most critical tool in a security team’s bag. Although many companies purport its demise, there continues to be significant advances in technology that help prevent malware both at the endpoint and in the network. Many organizations still seem to be struggling with automation, knowing that they need to strike a more automated posture, but not yet comfortable allowing automation to run independent of human review.
What was the best part of RSA 2017?
For me, the best part of any event is typically the meetings I’m able to have with new vendors who can dive deep into the theories and implementations behind their solutions. I had several great meetings, both scheduled and impromptu, that showed promise in terms of new ideas for isolating and preventing threats. I’m hopeful some of these new companies will partner with Webroot in the near future to deliver some truly innovative ways of protecting our customers.













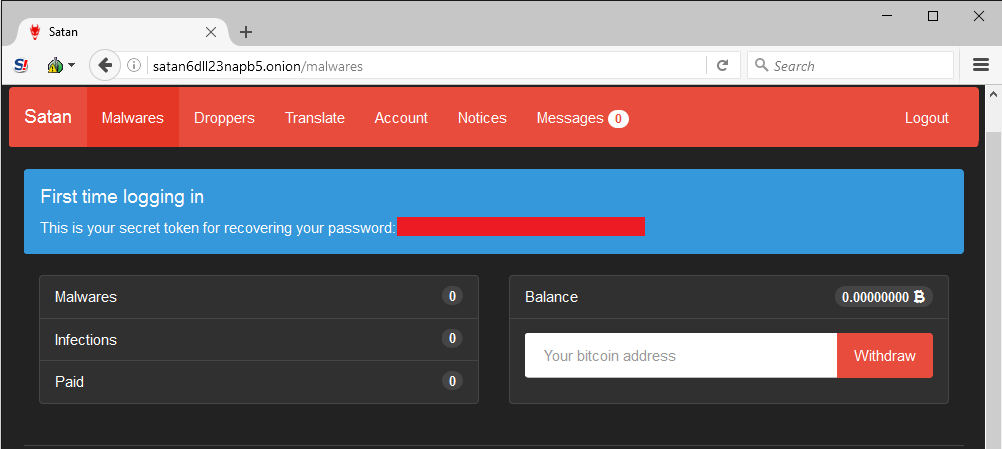
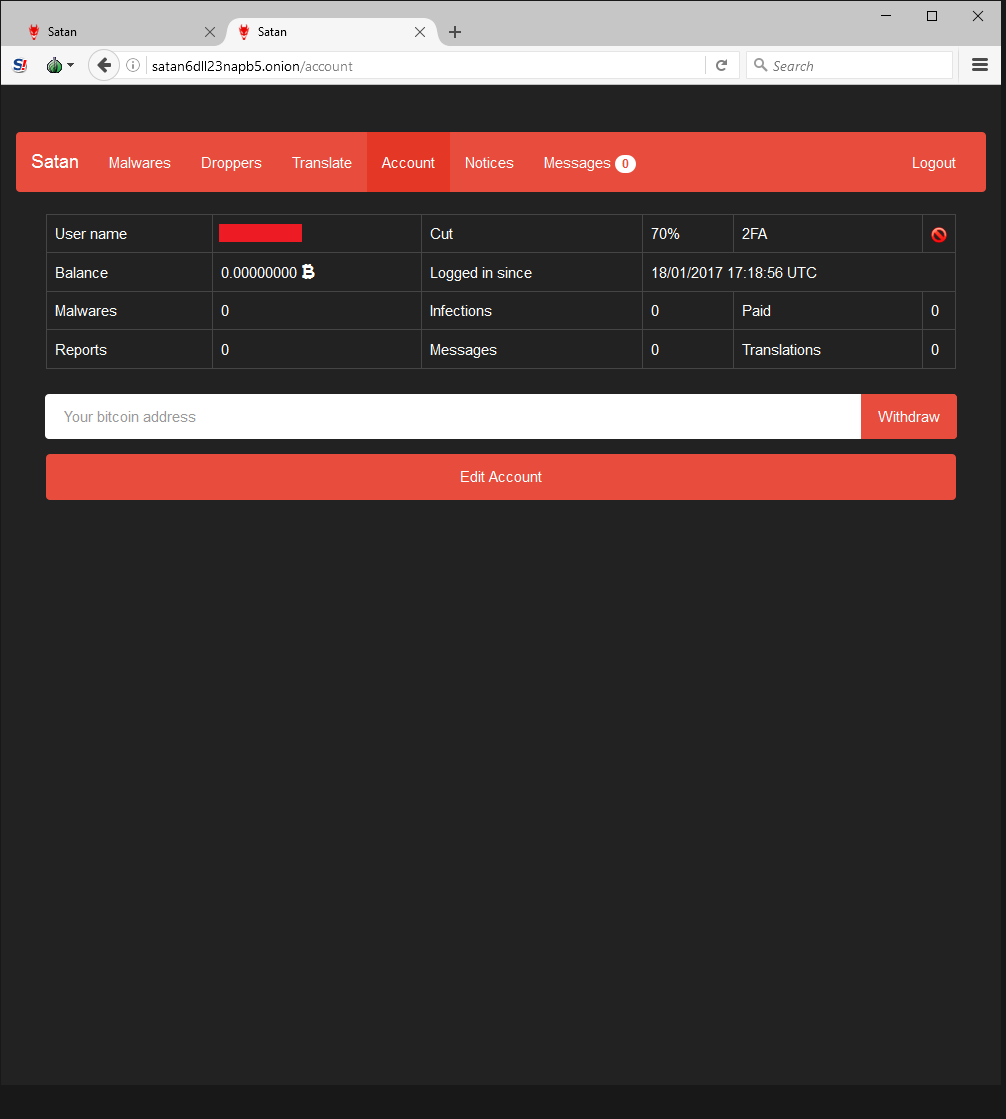
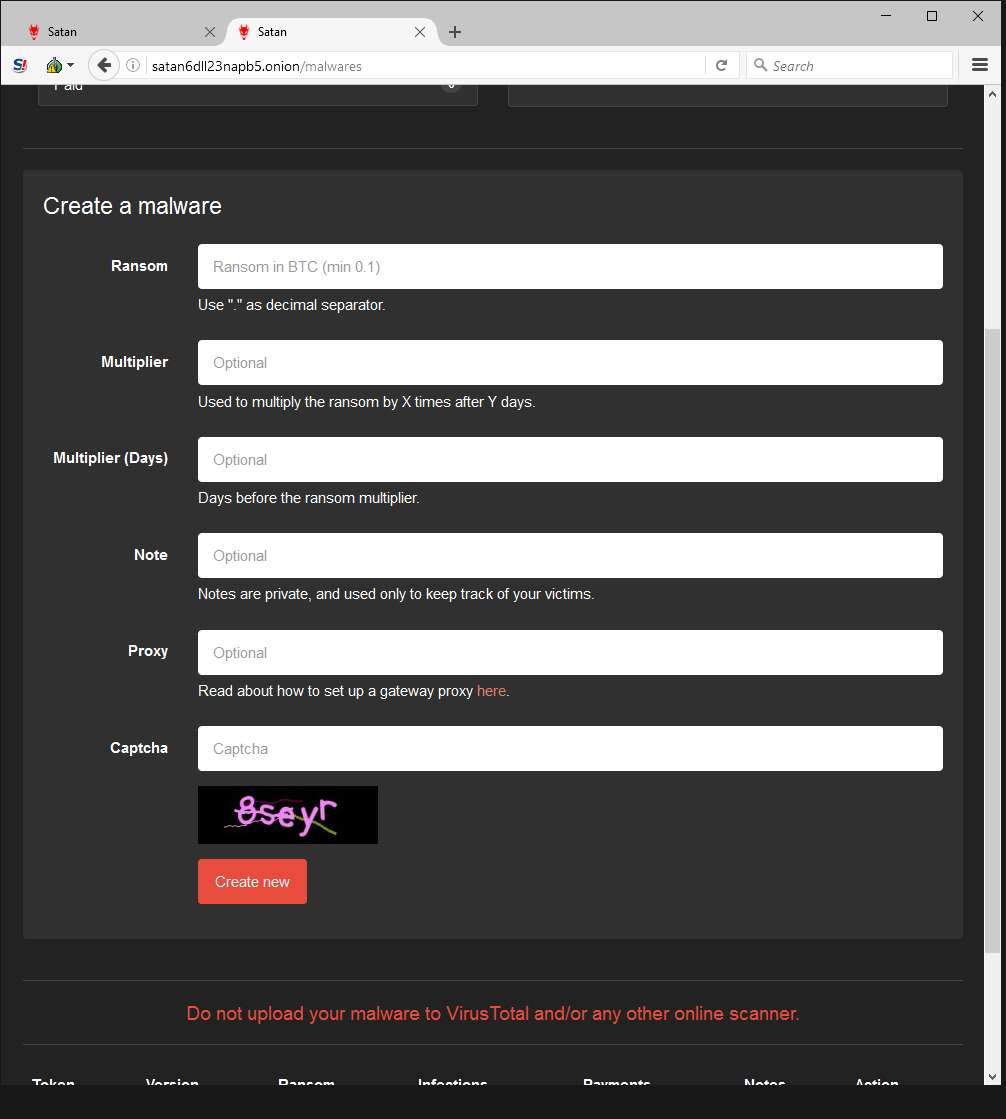
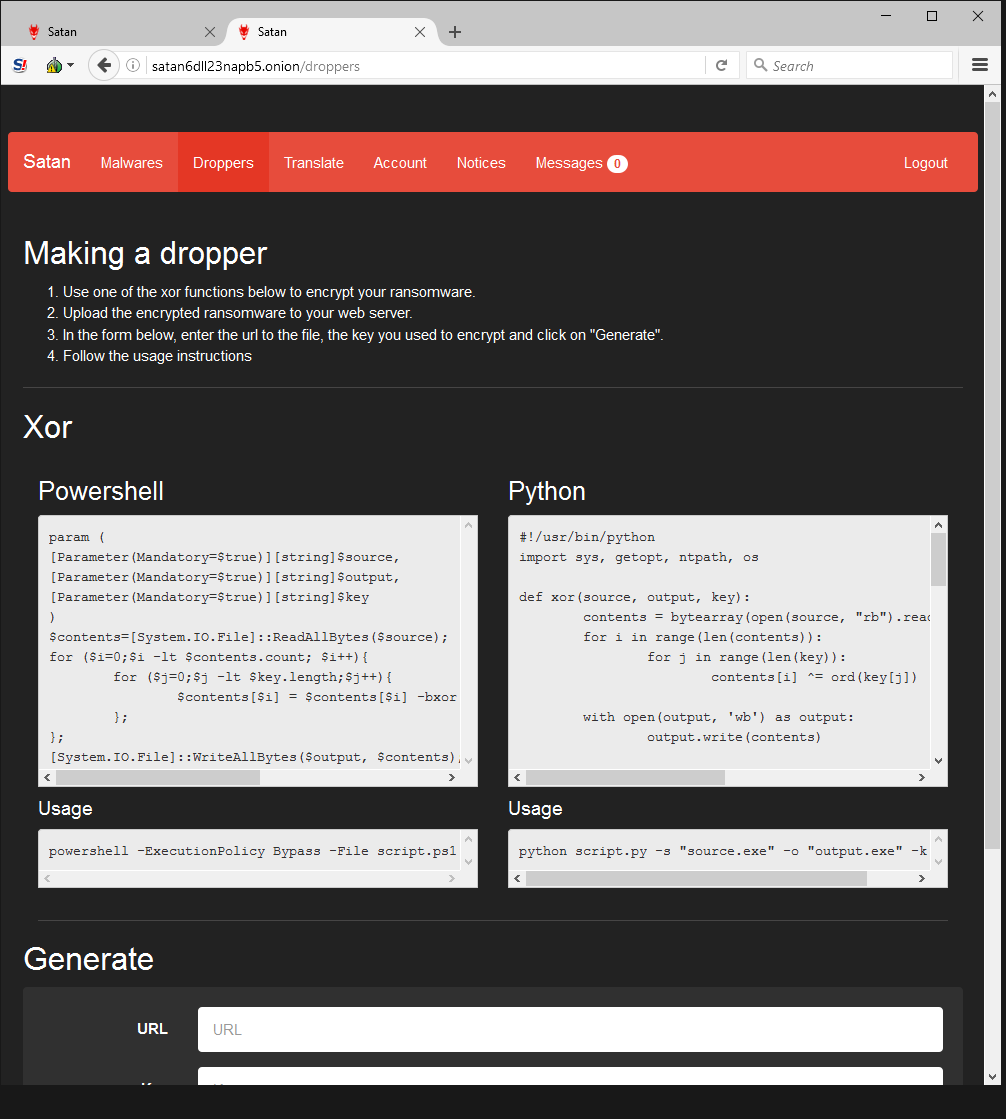
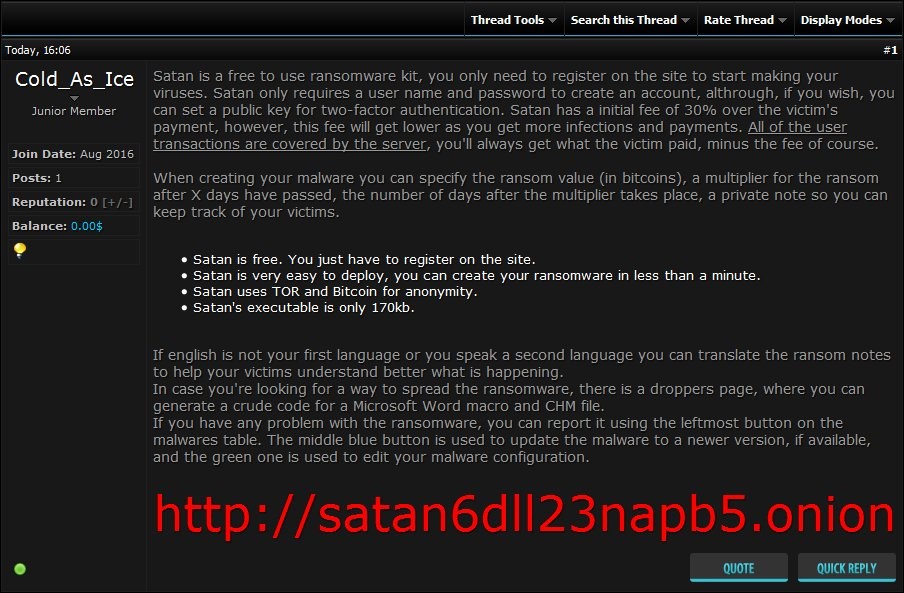 Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.