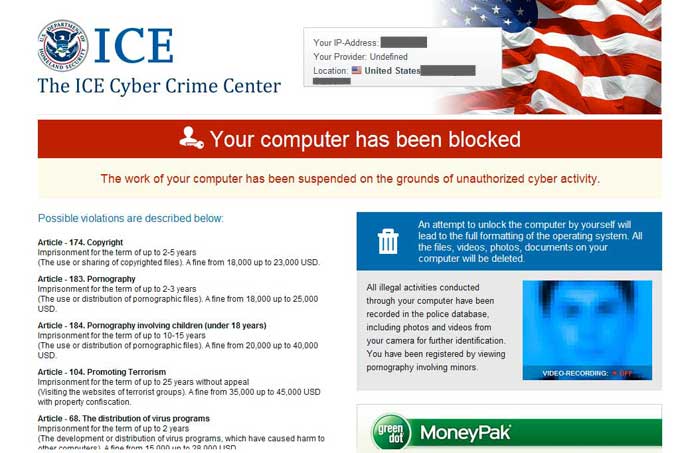
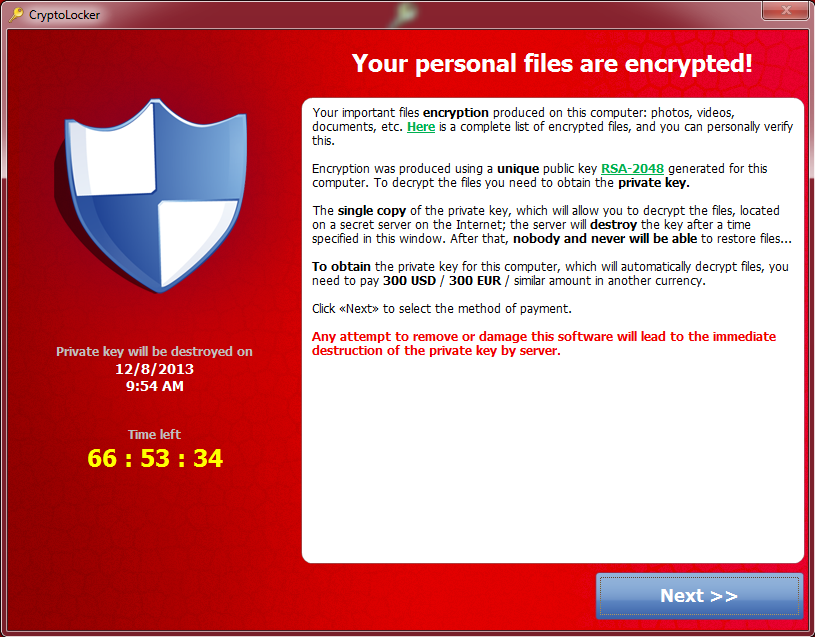
Happy New Year, everyone! Despite the lack of blog updates over the Holidays, we continued to intercept malicious campaigns over the same period of time, proving that the bad guys never take holidays. In this post, I’ll profile two prolific, social engineering driven type of malicious spam campaigns that we intercepted over the Holiday season, and naturally (proactively) protected you from.
More details: