Throughout the last couple of years, the persistent demand for geolocated traffic coming from both legitimate traffic exchanges or purely malicious ones — think traffic acquisition through illegally embedded iFrames — has been contributing to the growing market segment where traffic is bought, sold and re-sold, for the sole purpose of monetizing it through illegal means.
The ultimately objective? Expose users visiting compromised, or blackhat SEO-friendly automatically generated sites with bogus content, to fraudulent or malicious content in the form of impersonations of legitimate Web sites seeking accounting data, or client-side exploits silently served in an attempt to have an undetected piece of malware dropped on their hosts.
A recently spotted cybercrime-friendly underground traffic exchange service empowers cybercriminals with advanced targeting capabilities on per browser version basis, applies QA (Quality Assurance) to check their fraudulent/malicious domains against the most popular community/commercial based URL black lists, and ‘naturally’ we found evidence that it’s already been used to serve client-side exploits to unsuspecting users.
More details:










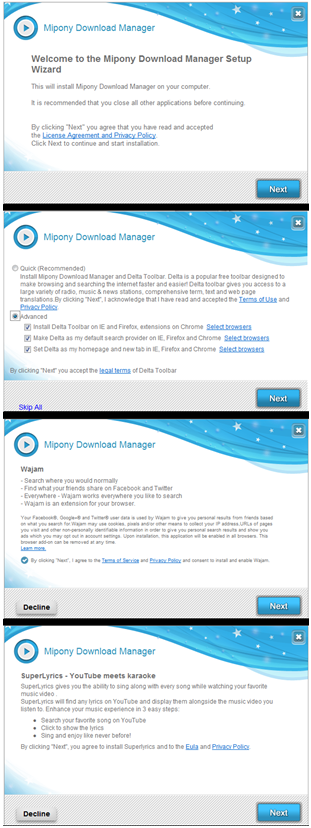
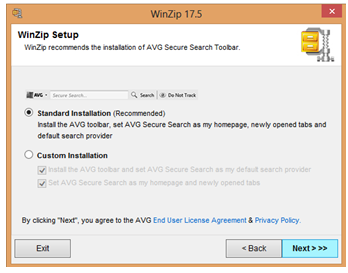
 PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily
PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily