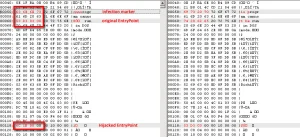
As a follow-up to the Blackhole Exploit posting, I thought I would share one aspect of my job that I truely enjoy: Discovery.
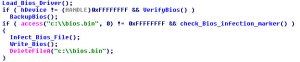
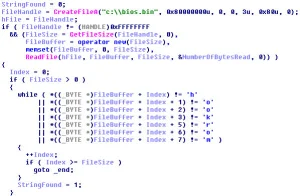
While investigating some active urls being served up via a blackhole kit, I noticed something quite odd, as I would end up on sites that had malicious code injected into their webpages.
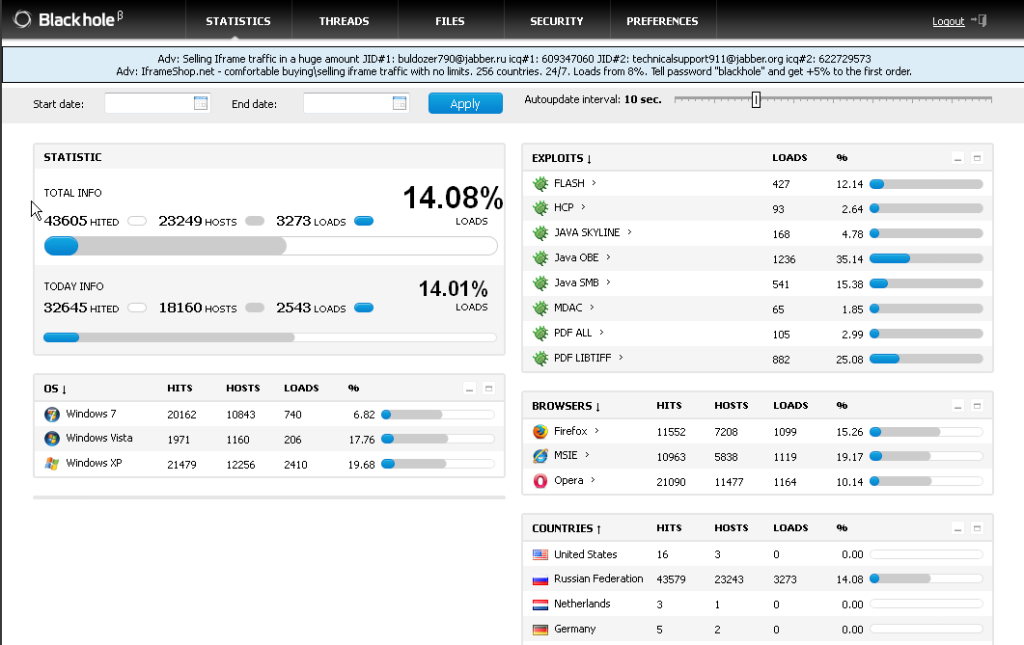
Once the redirection to the blackhole kit was initiated, I saw the usual exploits taking place, first being Internet Explorer and Adobe Flash, then onto Adobe Reader and Java.
This time, the kit didn’t stop there. Internet Explorer proceeded to launch Windows Media Player. Since I had never used it on this test machine, the Windows Media Player install sequence initiated, causing the windows media player setup screen to appear in order to finalize its installation.
I became curious as to what Windows Media Player is being used for. Unfortunately in this case, I couldn’t see where any files were called down to the machine and did not have any type of network analyzer running.