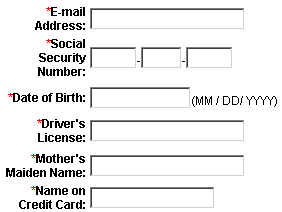
By Ian Moyse, EMEA Channel Director
 The cloud delivery model gives vendors a great amount of power. It is easier to create, deploy, maintain and enhance a service than it has been at any other point in computing history. Just look at Facebook, which grew to 500 million members in a very short period of time. People readily share within it, many with a limited understanding of the potential risks to their private information.
The cloud delivery model gives vendors a great amount of power. It is easier to create, deploy, maintain and enhance a service than it has been at any other point in computing history. Just look at Facebook, which grew to 500 million members in a very short period of time. People readily share within it, many with a limited understanding of the potential risks to their private information.
The ability to make an enhancement and almost instantly put it into the customer’s hands is immensely powerful – and immensely dangerous. If you’re a software vendor and distribute software with a bug, the effect propagates slowly as people install the update. And often, you’ll hear about the problem and get a chance to fix it before many customers even become aware. With cloud technology, however, such mistakes instantly propagate to all users. Because of this ability to quickly affect a wide range of customers, the responsibility for a cloud vendor is greater than we have seen before.
As the industry rushes to capitalize on the cloud delivery model, users are faced with more and more choices, making it harder to distinguish between a robust, reputable vendor and a small, possibly risky, player. Selecting a safe bet vendor is critical. Many are software vendors that are just dipping their toes into cloud technology. But the cloud is a very different world, and there is a different approach and mindset to deliver upon.
It is up to customers and resellers to perform due diligence on cloud vendors so they can deliver success stories to their customers and business associates. As in any market, there are pros and cons and good and bad providers. Customers and resellers need to take the time to make educated decisions to discern the good from the bad, the safe from the risky. And cloud vendors need to invest in the expertise and solutions required to deliver the high quality of service customers expect.
The benefits of cloud technology far outweigh the potential risks, both in terms of power and quality of service. Smaller businesses and individual consumers can now access robust applications that were previously affordable only by larger firms. The risks can be mitigated by performing educated decisions and being diligent in your choices. There are plenty of options, and it is up to you to select a vendor who can responsibly manage the power of the cloud.