Music fans may already be aware that next Tuesday the British music industry will honor the top acts of the year at a ceremony known simply as The BRITs. What they may not know is that common Internet criminals have begun to target people searching for information about the artists and the music connected with the awards for attack.
Music fans may already be aware that next Tuesday the British music industry will honor the top acts of the year at a ceremony known simply as The BRITs. What they may not know is that common Internet criminals have begun to target people searching for information about the artists and the music connected with the awards for attack.
This will be the 30th ceremony held in the 33 year history of the awards. As in previous years, the BRIT Trust (a charity run by BPI, the UK’s recording industry trade association) will donate profits from the ceremony, including the sale of a three-CD compilation, to various charities that benefit young people in the UK.
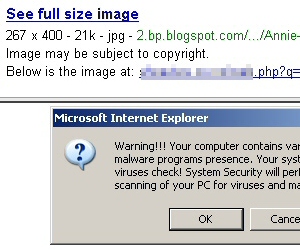
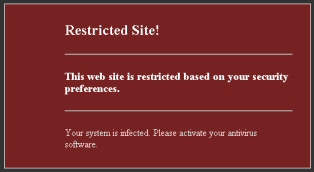
Unfortunately, at least two distinct threats face Web surfing Anglo-musicophiles: Bogus music download sites, which tease users with offers of “free downloads” of the compilation set, but then require users to register and pay a fee — none of which ends up in the hands of the BRIT Trust charity; And the purveyors of irritating fake alert messages, which invariably lead to rogue antivirus downloads, are also heavily pushing themselves to near the top rankings in some search results.