Recently I was asked to give my thoughts on mobile malware. I was asked this in relation to a number of reports released earlier in the year that were in my view misinterpreted. At the time many experts claimed mobile malware had been a much-exaggerated threat, based on such a large proportion of unwanted mobile apps/programs were seen to be adware.
Personally, I think it’s better to discuss mobile threats, mobile threats are more than just mobile malware. Many legitimate Apps have been seen over the last few years to be open to serious data leakage and only recently we have seen the discovery of Android’s “Stagefright” vulnerability – pegged as the “worst Android bug to date”. Receiving a simple MMS message with crafted exploit code, and without any interact from the victim, a hacker is able to do anything from stealing private communications to possible taking control of the device itself.
Read more: https://goo.gl/xCvGa6
In September, we saw “XcodeGhost”, this highlights the Apple App Store isn’t immune to serving up compromised apps. The Xcode development tools are used by iOS app makers. The original package was copied, modified, and then re-distributed for download. Apps built using the modified version were injected with malicious code, then published to the App Store.
Read more: http://goo.gl/VYEBgk
Mobile malware is a problem and is getting bigger with the ever increasing growth of the mobile market. There is concern that enterprise decision makers may misinterpret such reports and may not take mobile security as seriously as they should. Enterprises should be very concerned about mobile threats, this includes, mobile malware, mobile vulnerabilities and mobile data loss.
Mobile adware itself is a huge problem and needs to be addressed. Adware can collect personal information from the device it’s installed on, often without consent, including many pieces of PPI. Enterprises allowing such devices to connect to the private network should be seriously concerned, information is power, and company secrets are a secret for a reason.
The recent case of “Gunpoder” also highlights a new strategy malware writers are using. The game emulator app looks and behaves like adware, all while stealing PPI from the infected Android device. Many AV companies classified this malicious app as adware and many users thinking that adware was ‘more annoying than dangerous’ allowed the app to run.
Read more: http://goo.gl/Wm6Oyz
Cyberattacks are more prolific than ever, and businesses are clearly struggling in the battle of keeping their employee and customer data safe. Cybercriminals look for the simplest method to achieve their objective, if that’s through a mobile device and an uneducated user, then so be it. Mobile infiltration is often a precursor to further attacks.
Ignoring mobile malware and security, at any level, could have huge repercussions on a business’ reputation and customer loyalty as well as financially – it’s important not to leave the front door open.
So what can we do?
With all security implementations, striking the balance between mobile security and productivity is an on-going challenge. At present I would suggest it’s weighted towards productivity. Productive employees are great, but at the same time the company’s assets have to be properly secured. Therefore the fight against mobile malware needs to be appropriately evaluated in terms of personnel and monetary resources.
Mobile security is just another problem that arrived on the doorstep of the security and/or IT team, and on many occasions without any extra budget allocation. Like with many facets of cybersecurity it only becomes a priority after the inadequate defences are breached and company stakeholders want answers.
Companies need a mobile security strategy. They also need to follow best practices and keep abreast of industry information and security bulletins. Any strategy must consider corporate devices and BYODs. Organisations need to keep on top of patch management and understand what technologies best address their security needs, these may include centralised app management and app reputation technologies and in case of device loss – consider encryption and remote wiping.
Like with any device on a network, threat protection should be installed and kept up to date. Webroot offers mobile security apps for both Android and iPhone. The corporate network can be protected further by directing mobile traffic through special gateways with customised firewalls and security controls. Mobile devices should be configured to avoid unsecured wireless networks.
It goes without saying that devices need strong authentication and password controls.
Remember, mobile security and security in general is a continuous practice. It’s essential to implement a comprehensive mobile security strategy, then check how well training and policies are being interpreted and implemented with regular mobile security audits and tests. Communication between the organisation and its employees is vital – the risks and potential consequences need to be understood by employees through continued user education. At the same time organisations need to understand and respect the now slightly blurred boundary between business and personal.
Cybercriminals only need to find one hole in the defence, whereas security professionals have to secure all possible points of entry. It’s a battle we may lose from time to time, but we have a responsibility to make it as hard as possible for our adversaries.
















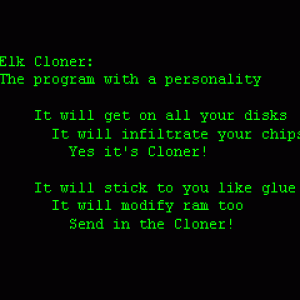 1982 – The first threat that occurred was the Elk Cloner (this however did not actually affect the Mac) which would cause the Apple II to boot up with a poem:
1982 – The first threat that occurred was the Elk Cloner (this however did not actually affect the Mac) which would cause the Apple II to boot up with a poem: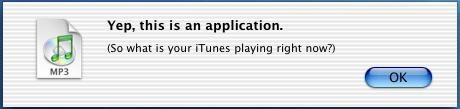 2004– Amphimix a program which is also a MP3 file. When launched it displays a dialog box which reads “Yep, this is an application. (So what is your iTunes playing now?)” It then loads itself into iTunes as an MP3 file called “Wild Laugh”, playing four seconds laughter.
2004– Amphimix a program which is also a MP3 file. When launched it displays a dialog box which reads “Yep, this is an application. (So what is your iTunes playing now?)” It then loads itself into iTunes as an MP3 file called “Wild Laugh”, playing four seconds laughter.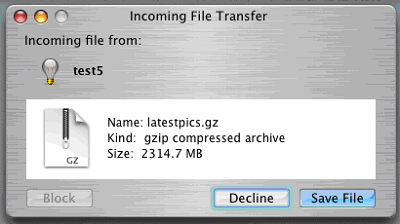 2006 – Leap is widely considered to be the original Mac Trojan. Leap used iChat to spread itself; forwarding itself as a latestpics.tgz file to the contacts on the machine. Inside the Gzipped Tar File (.tgz) was an executable file masked as a JPEG. When executed, it infected all Cocoa applications.
2006 – Leap is widely considered to be the original Mac Trojan. Leap used iChat to spread itself; forwarding itself as a latestpics.tgz file to the contacts on the machine. Inside the Gzipped Tar File (.tgz) was an executable file masked as a JPEG. When executed, it infected all Cocoa applications.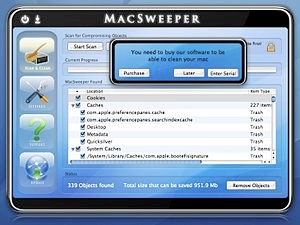 2008 – MacSweeper, Mac’s first ‘rogue’ application (a fake antivirus misleading users by reporting infections that doesn’t exists). When the infected user tried to remove the “infections”, MacSweeper asked to provide credit card details and pay $39.99 for a “lifetime subscription serial key.”
2008 – MacSweeper, Mac’s first ‘rogue’ application (a fake antivirus misleading users by reporting infections that doesn’t exists). When the infected user tried to remove the “infections”, MacSweeper asked to provide credit card details and pay $39.99 for a “lifetime subscription serial key.”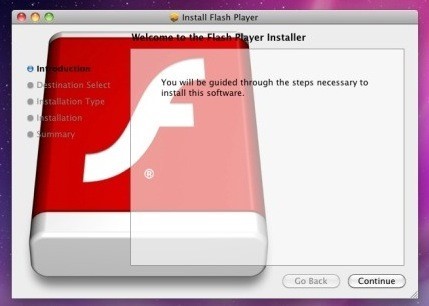 2011/2012 – Flashback was disguised as a Flash player download and targets a Java vulnerability on Mac OS X. The system is infected after the user is redirected to a compromised bogus site, where JavaScript code causes an applet containing an exploit to load. The Flashback malware was the largest attack to date, hitting more than 600,000 Mac computers.
2011/2012 – Flashback was disguised as a Flash player download and targets a Java vulnerability on Mac OS X. The system is infected after the user is redirected to a compromised bogus site, where JavaScript code causes an applet containing an exploit to load. The Flashback malware was the largest attack to date, hitting more than 600,000 Mac computers.