Only a month has gone by since the last RaaS (Ransomware as a Service) came to light. It looks this new business model that was first introduced by TOX a few months ago is spreading fairly rapidly. The idea is that now ALL malware authors of ranging skill can now create encrypting ransomware on a easy to use platform. This latest variant called ORX Locker is no different.

Simply enter in the desired info (price, identifiers, time limit, ect.) and the site will generate a new binary tailored to your specifications. The hackers are still responsible for distributing the malware, but renting time on many operational botnets and email phishing campaigns is also fairly easy to do in the underground darknet marketplace.
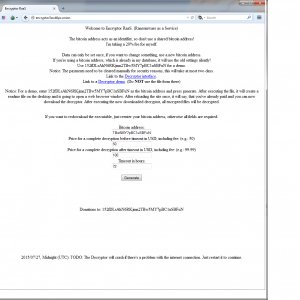
Once a victim is infected there is no GUI popup once all files are encrypted. It just changes the extension of all encrypted files to “.LOCKED” so you have a nice surprise when you try open one of your compromised files. Instructions on how to get your files back are left on your desktop as locally stored web page.

Special instructions are given to show a novice user how to connect to onion links and pay the ransom. Once you successfully connect to the darknet then the payment page is presented.

The instructions are clear on what you need to do to get your files back. Bitcoin is the criminal industry standard now and you’ll have a hard time paying for any ransom without it. While some ransoms will also accept the legacy money mules like ukash and moneypak, that is quickly dying out in favor of a better fee structure bitcoin launderers offer. Once you’ve paid you just download their tools and it will unlock all of your files using the AES 256 key that was generating during encryption.
This variant does not delete the VSS so as long as you have system restore enabled you can get your files back without paying the ransom. Just download a shadow copy tool like shadow explorer and you can restore files from a previous restore point. While the variant we analyzed showed no advanced techniques and is relatively simple in design, it remains a threat to unprotected systems and should be taken seriously. Improvement tweaks in the future are always possible and may “patch” the back doors it left open to your files.
- MD5 Analyzed:89E1EFDC766E9C7D41305566993BA800
- Additional MD5: D6ED4D4E8B1A95A224EBDD54529B3751
- Additional MD5: 1914724AEEA3CA954322053DD883B14A
Webroot will catch this specific variant in real time before any encryption takes place. We’re always on the lookout for more, but just in case of new zero day variants, remember that with encrypting ransomware the best protection is going to be a good backup solution. This can be either through the cloud or offline external storage. Keeping it up to date is key so as not to lose productivity. Webroot has backup features built into our consumer product that allow you to have directories constantly synced to the cloud. If you were to get infected by a zero day variant of encrypting ransomware you can just restore your files back as we save a snapshot history for each of your files up to ten previous copies. Please see our community post on best practices for securing your environment against encrypting ransomware.















 It just doesn’t seem to end with all the exploits being revealed by the Hacking Team dump earlier this month. This vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains embedded OpenType fonts. The Adobe Type Manager module contains a memory corruption vulnerability, which can allow an attacker to obtain system privileges on an affected Windows system.
It just doesn’t seem to end with all the exploits being revealed by the Hacking Team dump earlier this month. This vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains embedded OpenType fonts. The Adobe Type Manager module contains a memory corruption vulnerability, which can allow an attacker to obtain system privileges on an affected Windows system.