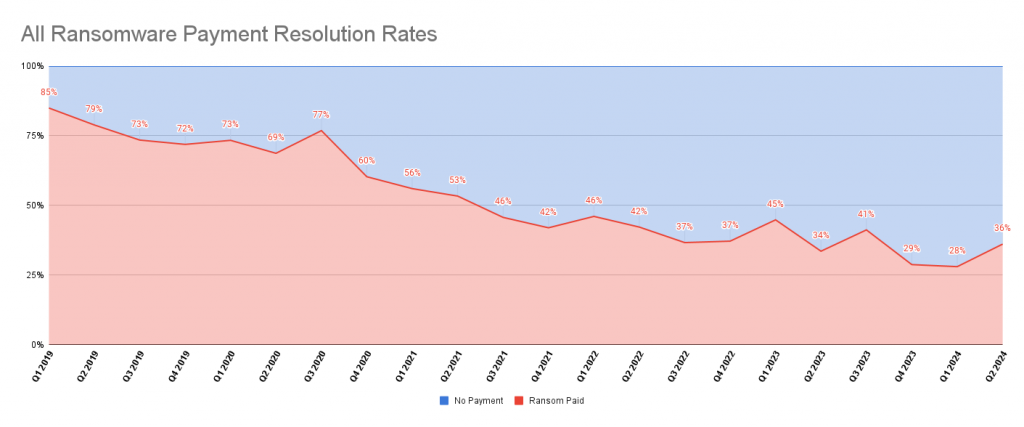
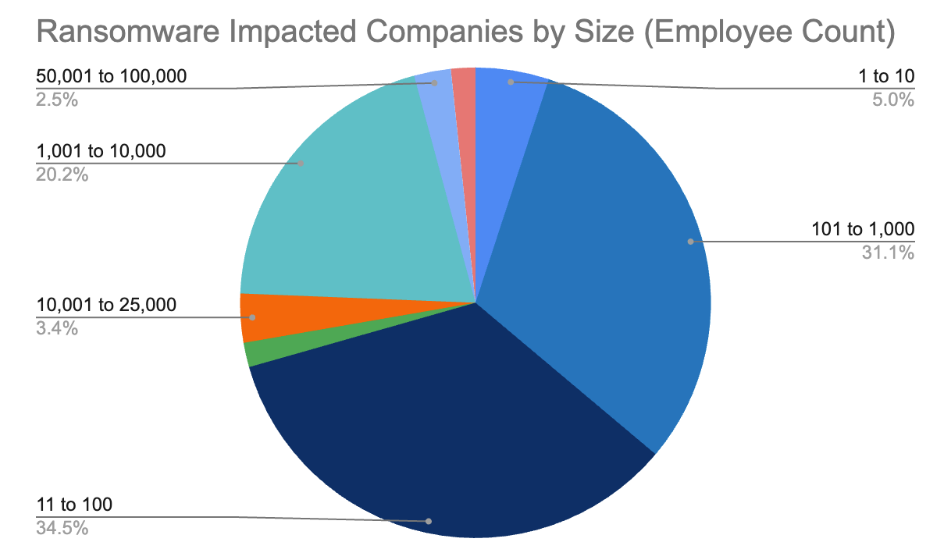
When it comes to endpoint detection and response (EDR) compatibility within an MDR offering, managed service providers (MSPs) are weighing two key priorities: native EDR integration or the flexibility to support multiple solutions. According to a recent OpenText survey, opinions are split almost evenly. While 52% of MSPs view native compatibility as moderately or very important, 48% place greater value on flexibility.
This divide reflects the unique demands MSPs face. On one hand, native compatibility ensures a tight integration. On the other, the ability to work seamlessly with various EDR tools is critical for MSPs managing diverse client environments. For MSPs managing a mix of EDR tools across their customer base, this adaptability can be the difference between a smooth operation and a logistical headache.
In this blog, we’ll explore why flexibility in EDR compatibility is becoming a critical advantage for MSPs, how it ties into SIEM analysis, and actionable steps MSPs can take when evaluating MDR providers.
The case for native EDR compatibility
For MSPs and their customers, native EDR compatibility can offer advantages, especially when targeting newer companies that have not yet established an EDR infrastructure.
Here’s why:
- Streamlined integration:
Native EDR solutions typically provide seamless integration with the MDR platform, simplifying deployment and reducing setup time. This can be particularly appealing for MSPs looking to quickly onboard new customers who do not yet have an EDR solution in place. - Ease of use:
A native EDR integrated into the MDR platform provides MSPs with a consistent toolset, simplifying training for security teams and boosting overall efficiency and productivity.
However, for MSPs serving established SMBs that already have an EDR solution, the dynamic changes. An MDR capable of working with any EDR solution often delivers greater flexibility and value by complementing the SMBs’ existing setups.
When flexible EDR support wins
For MSPs, flexibility in EDR support provides a more strategic advantage. Managing security for well-established SMBs often means working within complex, diverse environments where a rigid “one-size-fits-all” approach simply doesn’t work. Here’s why flexible EDR support matters:
- Avoiding “rip and replace:”
Many MSP prospects already have an EDR solution in place that they are comfortable with and that meets their needs. Moving to a new, native EDR can impose a “rip and replace” burden, leading to disruptions and additional costs that may not be acceptable to MSPs. - Supporting diverse client environments:
MSPs often manage a variety of EDR products across their customer base. The ability to support multiple EDRs means MSPs can tailor their MDR services to fit the unique needs of each client without forcing them to change their existing security infrastructure. - Future-proofing:
Flexibility allows MSPs to stay ahead of the curve by ensuring their MDR solution can integrate with emerging EDR tools. This adaptability is crucial in a rapidly evolving cybersecurity landscape.
The MDR advantage—unifying EDR telemetry through SIEM
In a modern MDR solution, the SIEM platform serves as the backbone, ingesting security telemetry from across the customer environment. This includes feeds from firewalls, cloud services, identity providers, and—crucially—EDR solutions. The ability to support multiple EDR tools isn’t just about flexibility; it’s about leveraging the full power of SIEM to deliver more effective and unified threat detection and response.
- Centralized visibility:
By aggregating telemetry from diverse EDRs and other security tools into a single SIEM platform, MSPs gain a holistic view of the customer’s security posture. This comprehensive perspective enables faster identification of threats and vulnerabilities across the environment. - Improved threat detection:
SIEM platforms excel at correlating data from multiple sources. By ingesting streams from EDRs alongside other security feeds, the MDR solution enhances its ability to detect sophisticated threats with greater accuracy and precision, reducing false positives and improving response times. - Enhanced reporting and insights:
Unified telemetry within the SIEM allows MSPs to generate detailed, actionable reports that highlight trends, identify gaps, and demonstrate the value of their security services. These insights help MSPs guide their clients in making smarter security investments.
Actionable advice for MSPs
When choosing an MDR provider, MSPs should keep a few key factors in mind:
- EDR compatibility:
Ensure the MDR solution can seamlessly integrate with multiple EDR tools to support your diverse client environments. - SIEM integration:
Look for MDR solutions that can unify EDR telemetry through a centralized SIEM platform. - Scalability:
Choose an MDR provider that can scale with your business and offers the flexibility to adapt to evolving client needs and emerging cybersecurity challenges.
By prioritizing these factors, MSPs can provide their customers with advanced, efficient, and flexible security solutions that meet their unique needs.