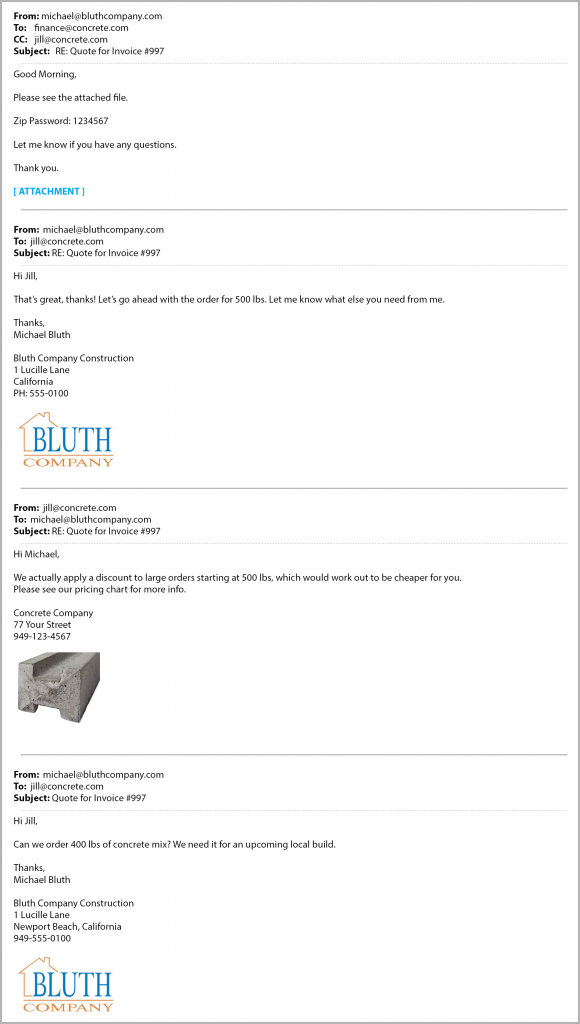
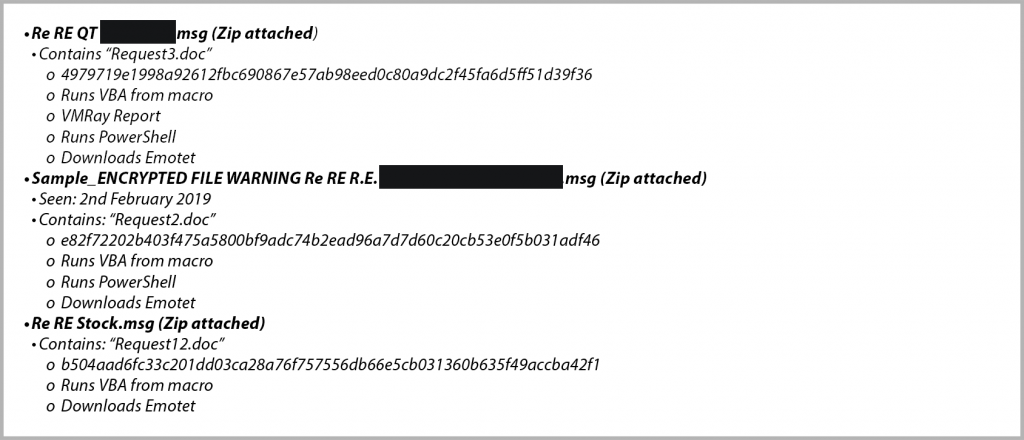
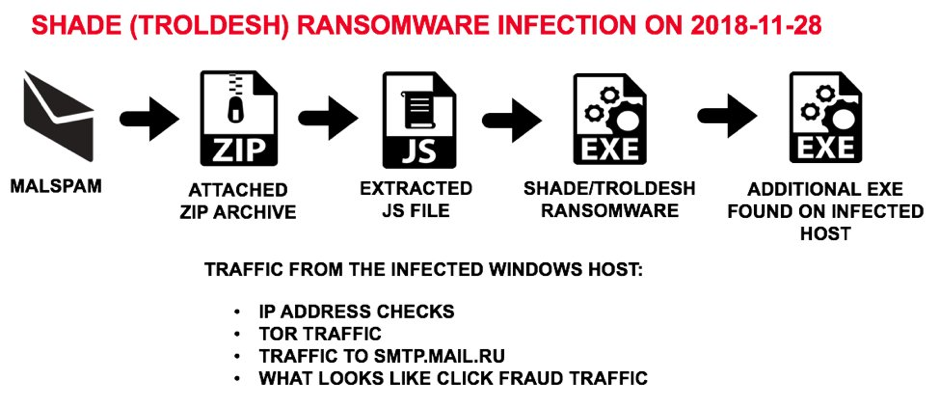
Tax Extortion Emails Bring Major Threats
A new email campaign has been spotted threatening ransomware and DDoS attacks over fake tax documents allegedly held by the attackers if a Bitcoin ransom isn’t paid. The campaign authors also threaten to send fake tax documents to the IRS through a poorly-worded ransom email that even provides Wikipedia excerpts for each threat put forward. Fortunately, as the campaign seems to be focused on corporations rather than individuals, no payments have been made to the attacker’s crypto coin wallet address.
Hotel Reservation Data Leaking Through Third-Party Services
As major data breaches continue to flood headlines, a recent study has revealed that nearly two of every three hotels exposes information about its guests to third-parties. Excerpts of the data show names, social security numbers, and payment card details that could give unauthorized users the ability to compromise identities or make changes to current reservations. Most of the exposed data involves comping through third-party services run on hotel websites offering customers additional packages.
Ransomware Conspirator Jailed in the UK
Police in the UK have officially charged and jailed a man for his part in the operation of a global ransomware campaign with ties to a Russian criminal organization. Charges range from fraud and blackmail to computer misuse relating to DDoS attacks and the Essex man is set to face at least six years. By masquerading as an advertising agent looking to purchase ad space on high-traffic sites, he was able to infect ad links with malware and other exploits to spread his campaign.
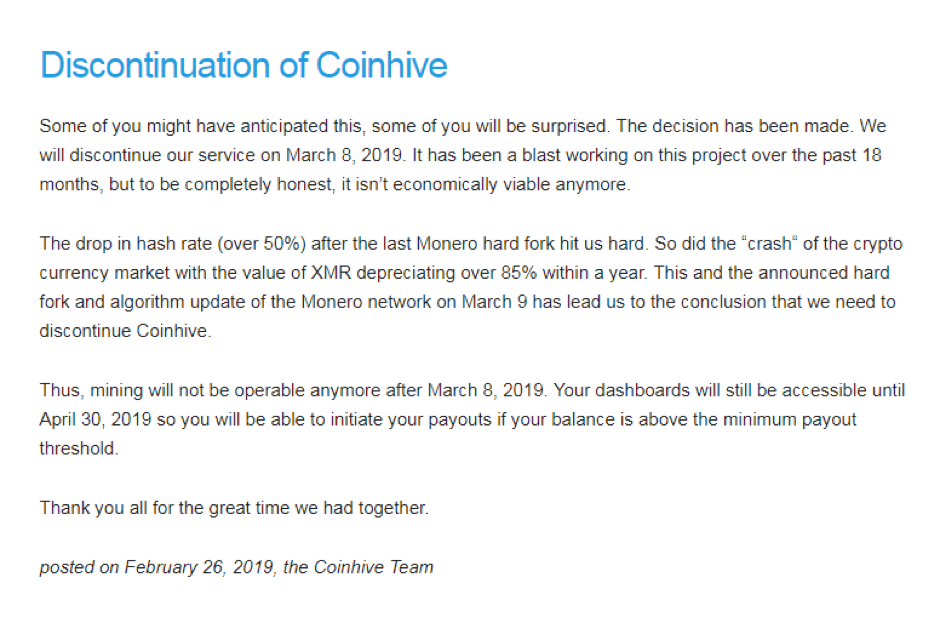
Firefox Begins Blocking Cryptomining Scripts
Even after the demise of CoinHive, cryptomining scripts are still being secretly deployed on thousands of websites without the knowledge of their owners and visitors. With the release of Firefox 67 beta, Mozilla is hoping to completely protect their users from malicious scripts that download and run cryptominers and other unwanted tracking software by using a blacklist created by Disconnect, a VPN developer with a reputation for privacy protection. Additionally, the new Firefox version will block fingerprinting scripts commonly used to invade a user’s browsing privacy.
MyCar App Uses Hardcoded Credentials
Thousands of cars were left vulnerable after a widely used vehicle telematics systems was found to be using hardcoded credentials in their mobile apps. Used in dozens of different car models to enable remote control functions, the hardcoded credentials leave these vehicles accessible to anyone with the app’s source code and the plaintext credentials within. Fortunately for users, the latest iOS and Android versions of the MyCar app have been updated to resolve this vulnerability.