Redirectors are a popular tactic used by cybercriminal on their way to trick Web filtering solutions. And just as we’ve seen in virtually ever segment of the underground marketplace, demand always meets supply.
A newly launched, DIY ‘redirectors’ generating service, aims to make it easier for cybercriminals to hide the true intentions of their campaign through the use of ‘bulletproof redirector domains’. Let’s take a peek inside the cybercriminal’s interface, list all the currently active redirectors, as well as the actual pseudo-randomly generated redirection URLs.
More details:










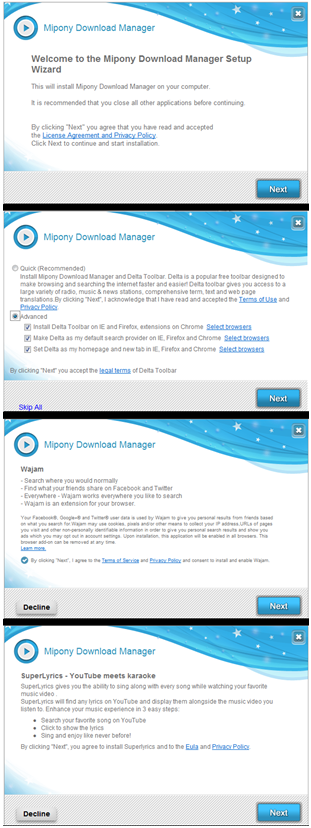
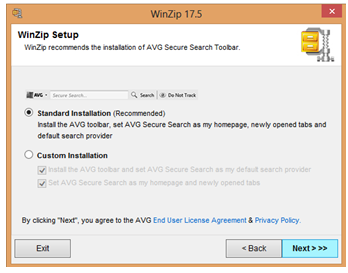
 PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily
PUA’s (Potentially Unwanted Applications) are often nuisance applications which serve little purpose other than using your computer as a gateway for online advertisements or as a catalyst to deliver annoying applications that may pester you to the point where you want to throw your computer out a window. Anti-Malware companies usually have pretty weak detection of these types of programs and have generally failed to protect their customers’ computers from this sort of bloatware. As a result, countless users have to suffer through agonizing pains of pop-up windows, webpage redirects, search redirects, and sometimes even bluescreens just to try and get their daily