The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
Panera Ignores Security Flaw for Months
This week it was revealed that Panera failed to disclose or resolve a data breach affecting nearly 37 million customers for more than eight months. When researchers initially reached out to the company in August of last year, Panera officials believed the e-mail to be spam and ignored it until the researcher followed up about the leak. While a resolution has finally been put forth by Panera, their attempts to downplay the leak to the media and extreme delay in taking action are unacceptable for an organization of that size.
Indian Utility Company Facing Ransom
A regional power utilities system in India was recently breached and now finds their billing data held hostage for nearly 20 Bitcoins. While officials are the cause of the attack, the billing systems are already back to normal, as there were several methods for backing up the data. The affected site was one of two that monitor many districts’ electricity billing throughout the region.
Under Armour Fitness Tracking App Breached
Under Armour announced this past week that their MyFitnessPal app had been subject to a data breach potentially affecting nearly 150 million users. Fortunately, the breach seems to contain only usernames, email addresses, and passwords for the app. Customers’ more sensitive information is stored beneath another layer of encryption. Under Armour has since released a full FAQ site along with a public statement in less than a week from the initial discovery.
Employee Info Leaking from Live Chat Widgets
Several live chat widgets have been found to expose a considerable number of personal details for employee conducting the chats. What’s more worrisome, the offending widgets can be found on hundreds of the largest websites, though the data being leaked varies based on company data policies. At least one of the notified widget creators has acknowledged the issue and will hopefully resolve it quickly.
High-end Retailers Have Payment Data Stolen
At least three separate high-end retailers recently disclosed a payment system breach that could impact millions of recent customers. A few hundred thousand cards have already been released, with the hacker group known as JokerStash promising to release more than 5 million in total, likely split amongst the stored data of the three retailers.











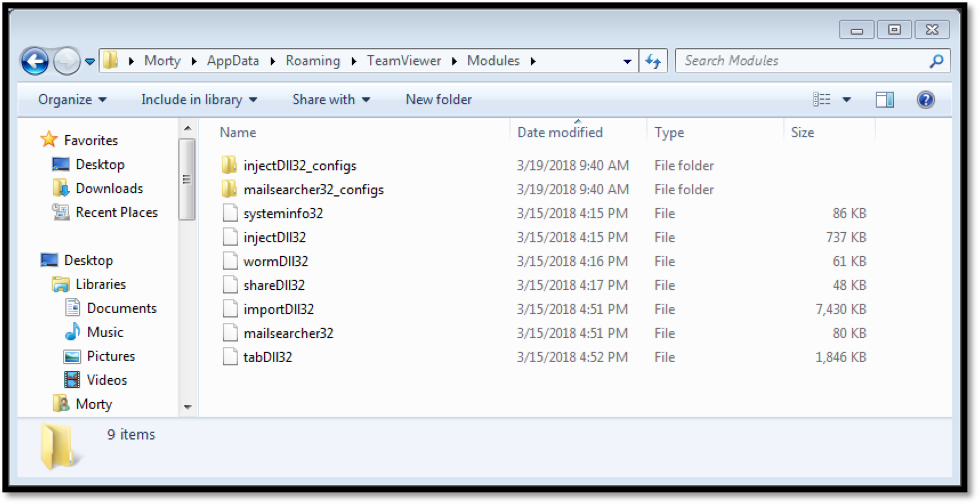
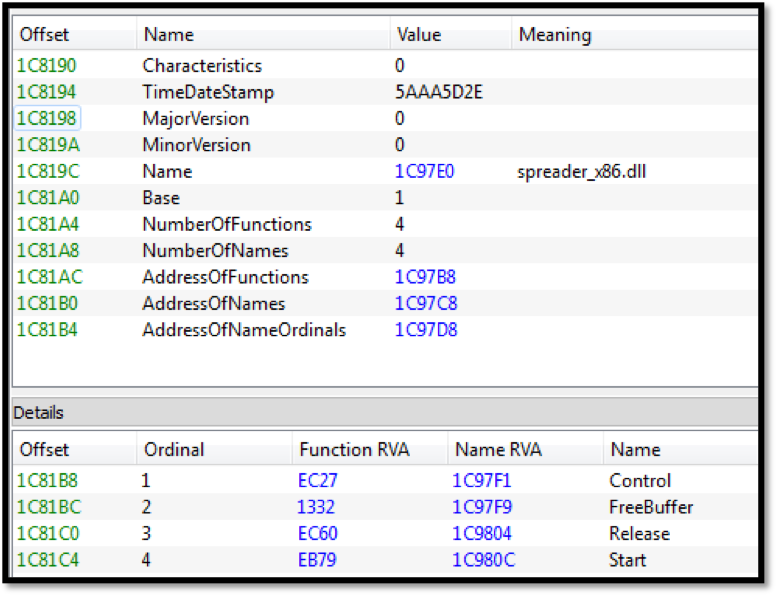
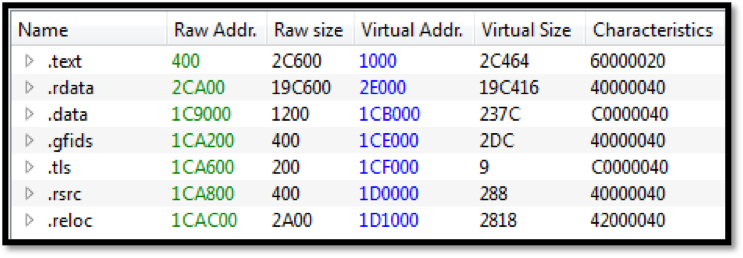
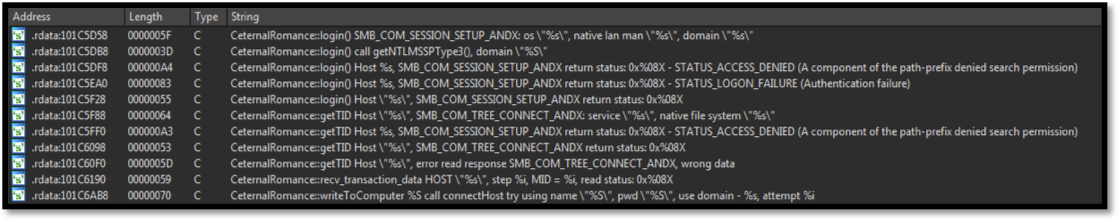 Image 4: String references to EternalRomance exploit used for lateral movement
Image 4: String references to EternalRomance exploit used for lateral movement
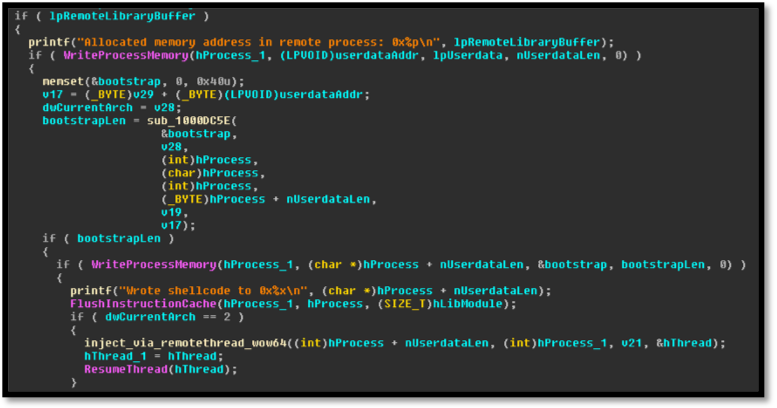
 Image 8: Iterate over user profiles and create
Image 8: Iterate over user profiles and create