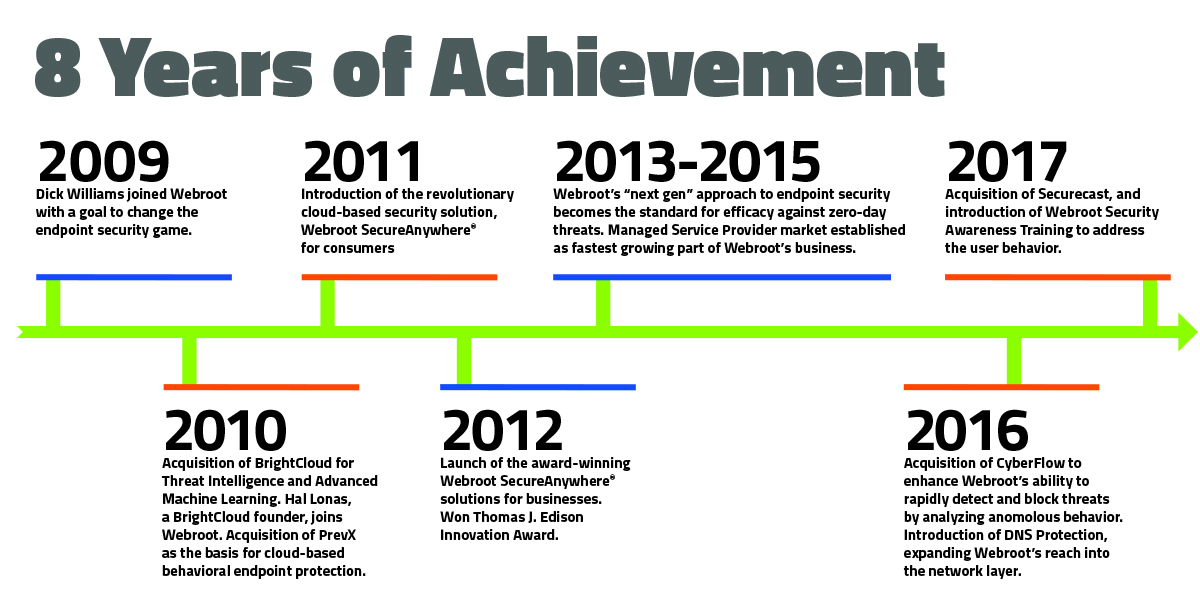
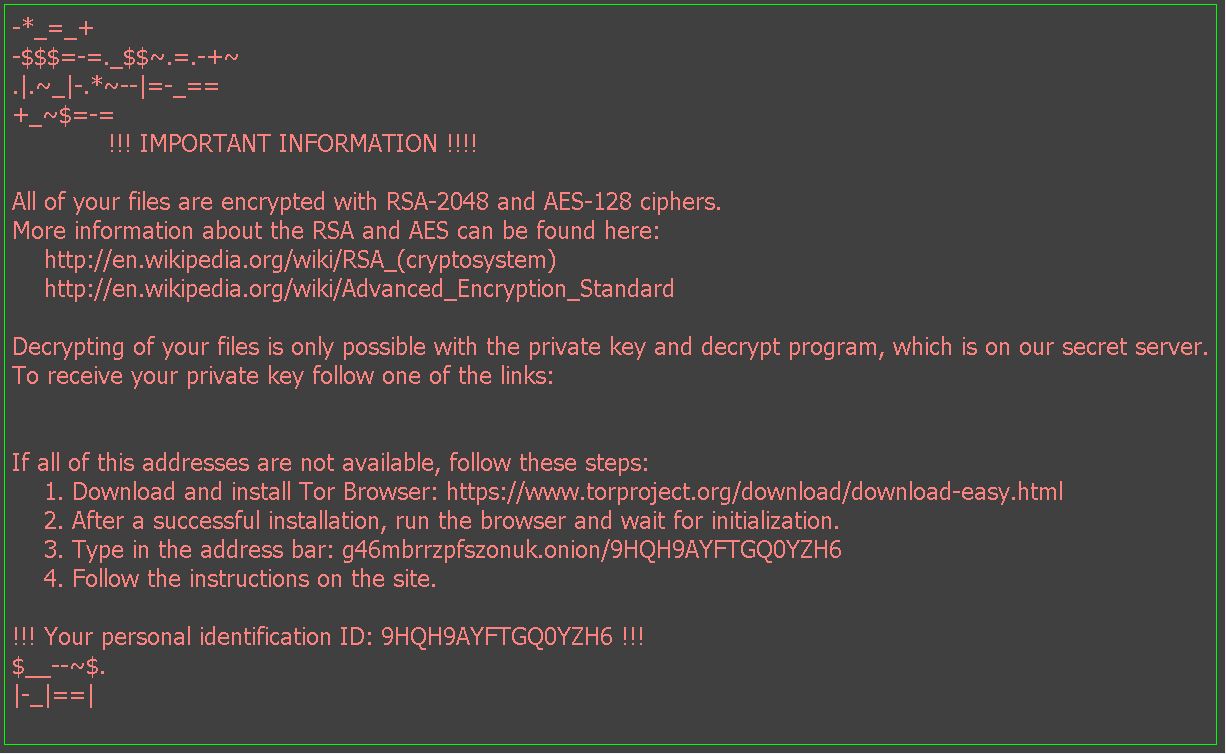
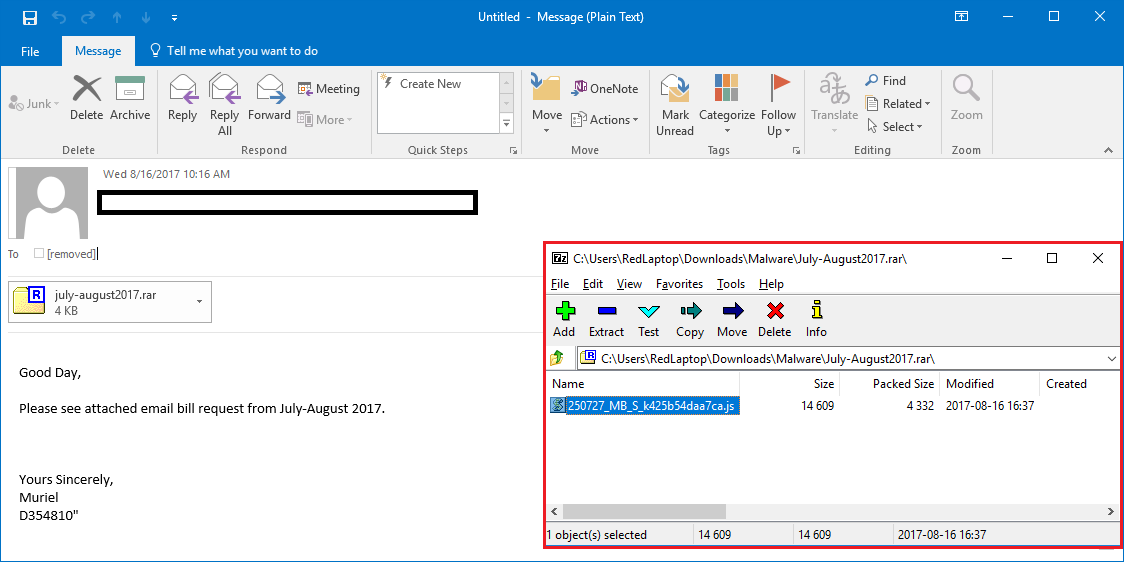
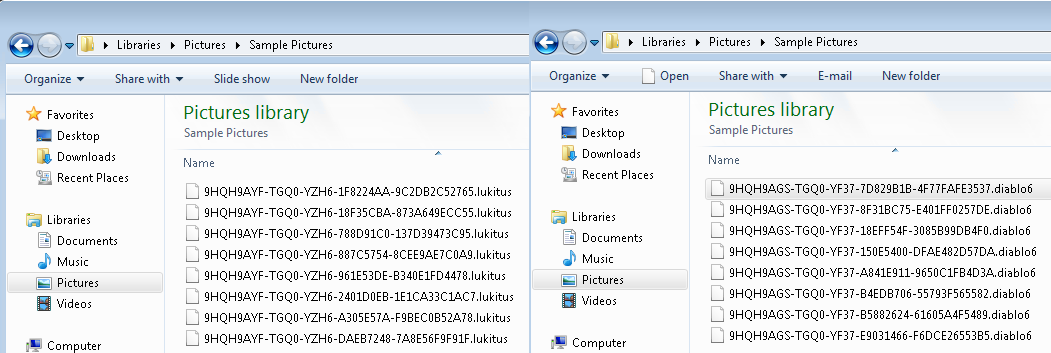
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
Yahoo Breach Expands to All 3 Billion Users
In a recent statement, Yahoo announced that its 2013 breach, which took nearly 4 years to investigate, has impacted all 3 billion of their site’s unique users. Along with this recent update, the company is still reeling from a separate 2014 breach, which holds the dubious title of 2nd largest data breach to date. This update to the total affected users isn’t surprising, given that the original breach left questions as to why some accounts were compromised, while others remained untouched and showed no signs of malicious activity.
Facebook Under Fire After Russia-Based Ads Overwhelm Users
Recently, Facebook founder Mark Zuckerberg issued an apology for the site’s lack of action in stopping Russian advertisements and fake news articles, which have been circulating heavily since the 2016 election season. His statement goes on to promise that additional safeguards will be implemented to ensure Facebook can continue to be a safe platform for users to voice their opinions.
Hackers Prove You Can Game the Gamers
In the past week, R6DB, an online stat tracking service for the popular game Rainbow Six Siege was shut down after several servers were wiped completely due to a cyber-attack. The attackers accessed the database remotely, as it was left unsecured during a recent data migration that hadn’t yet concluded. Unfortunately for many players, their information is completely gone, while company officials are still working to restore what information they can.
Apple’s About-Face
Face ID, the iPhone X’s highly-touted biometric device locking system, has been found to be less than secure in several scenarios. Some of the vulnerabilities relate to young users whose facial features may change as they age, and siblings with similar facial features being able to spoof the security measure. Fortunately, Face ID isn’t the only security precaution on the new device, as it will still require a passcode to be set.
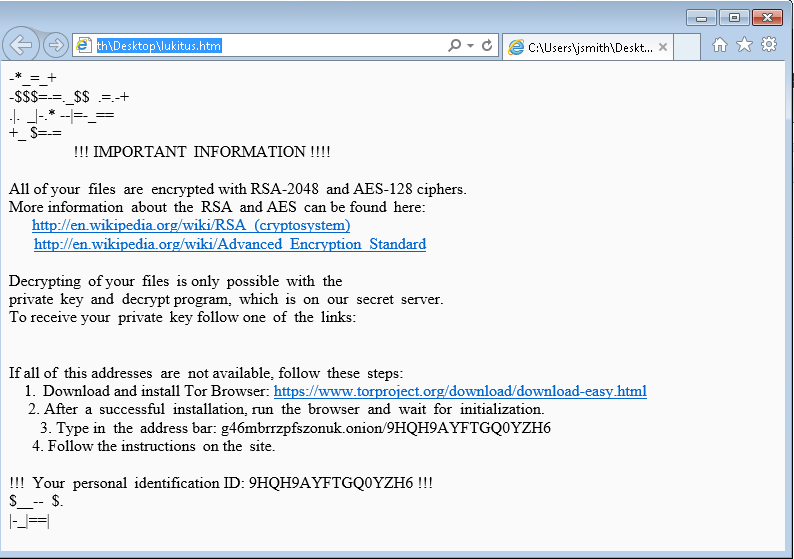
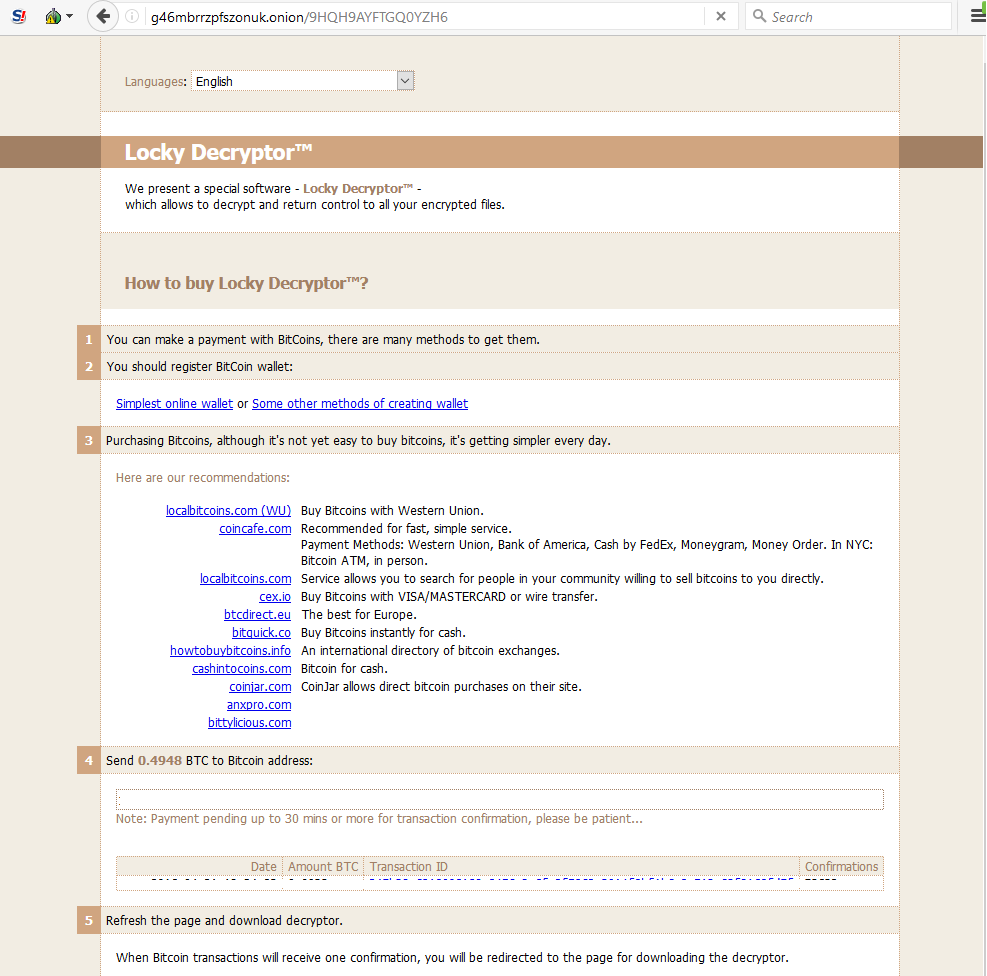
NFL Player Data Found on Unsecure Server
Recently, researchers discovered that an unsecured database belonging to the NFL Players Association contained records on over 1,100 individual players and agents. The compromised data included everything from players’ personal info to team contracts and payee information. Even more worrisome, a ransom note with a bitcoin address was found among the data, though it appears the data itself wasn’t leaked to Dark Web sellers. Fortunately, the database was secured shortly after researchers notified the NFLPA, though no response was received from the association regarding the incident.