By Dancho Danchev
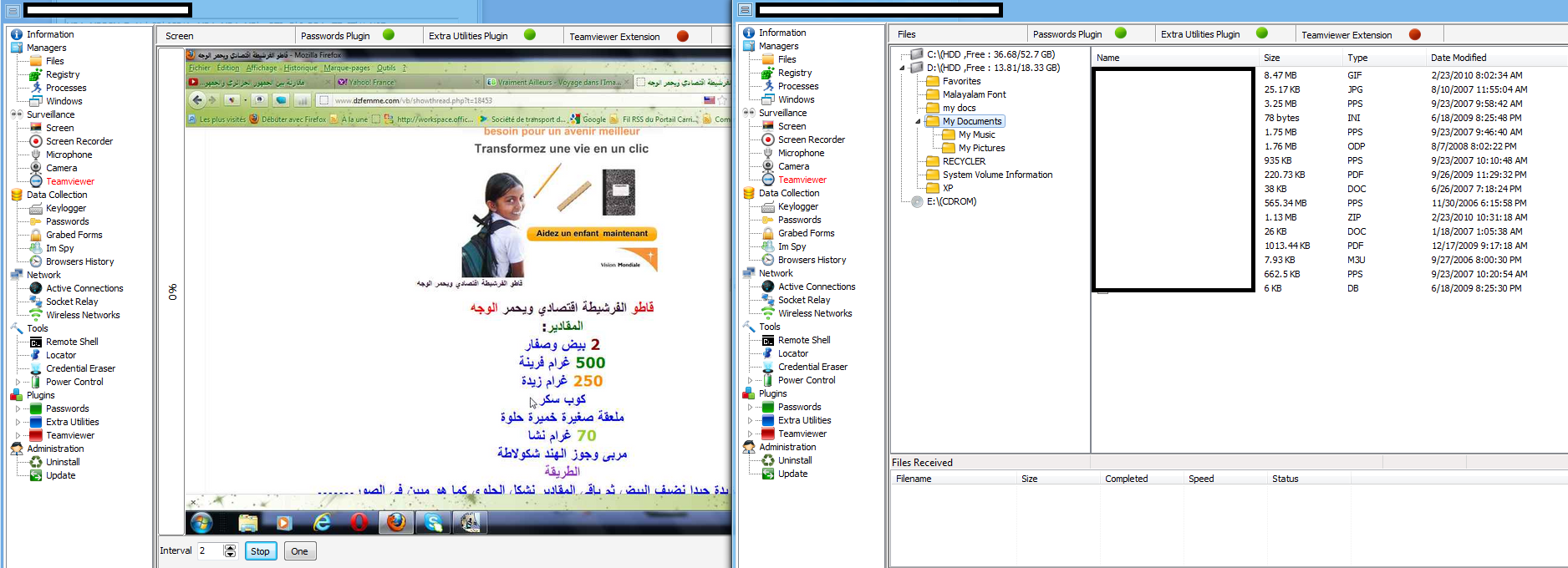
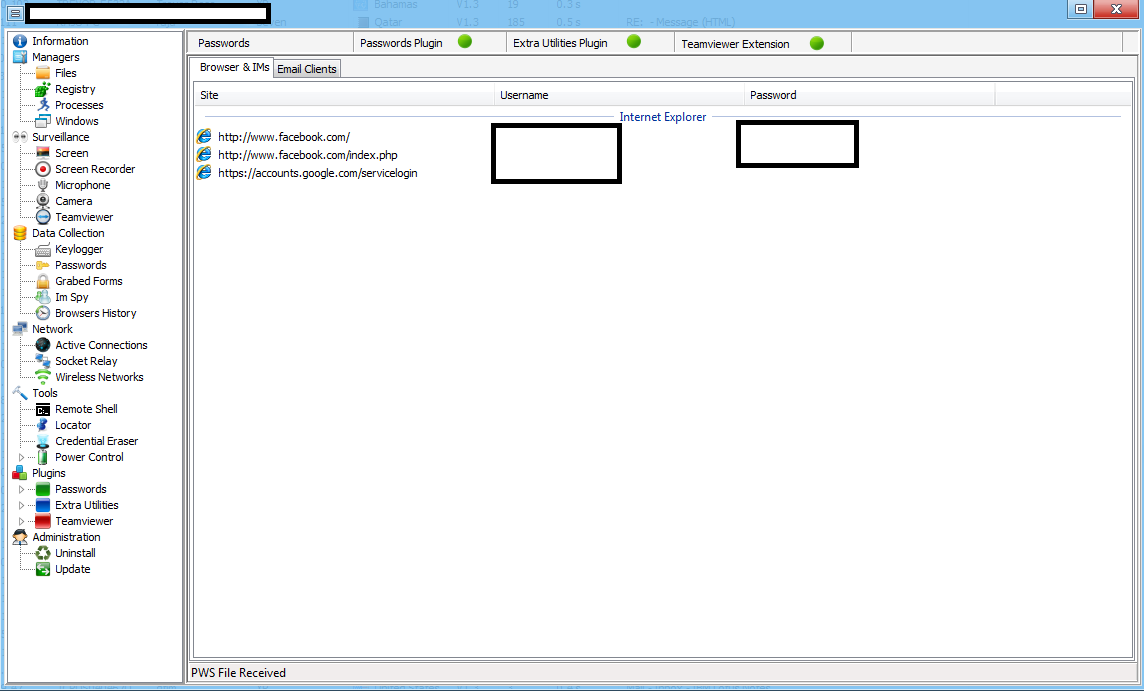
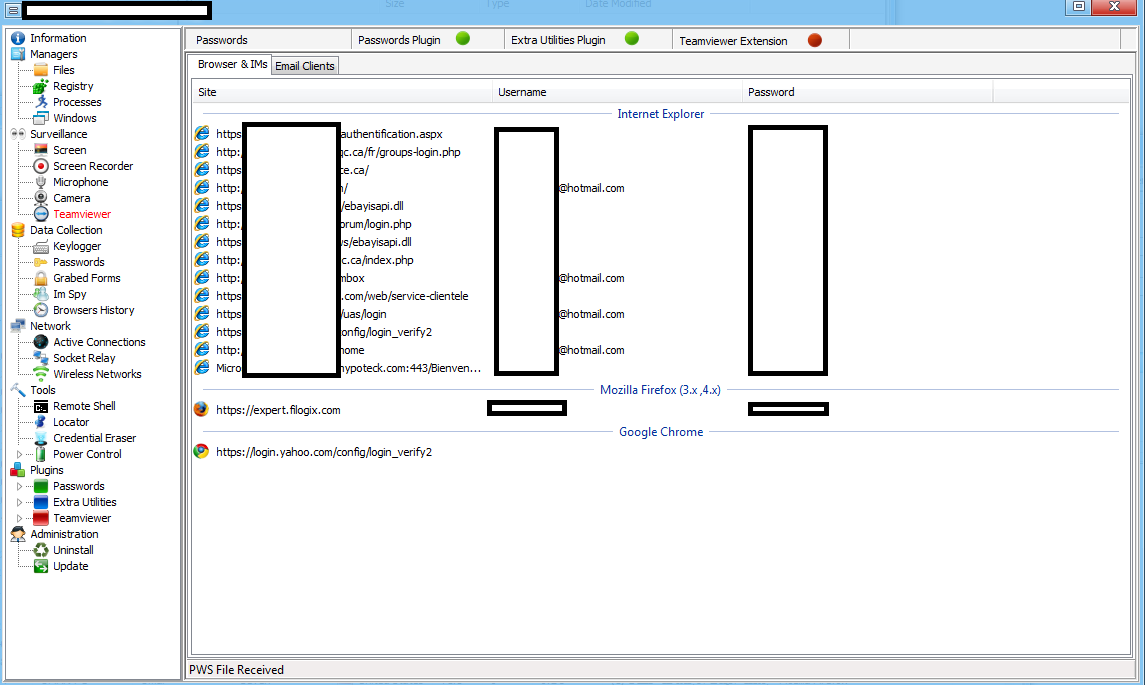
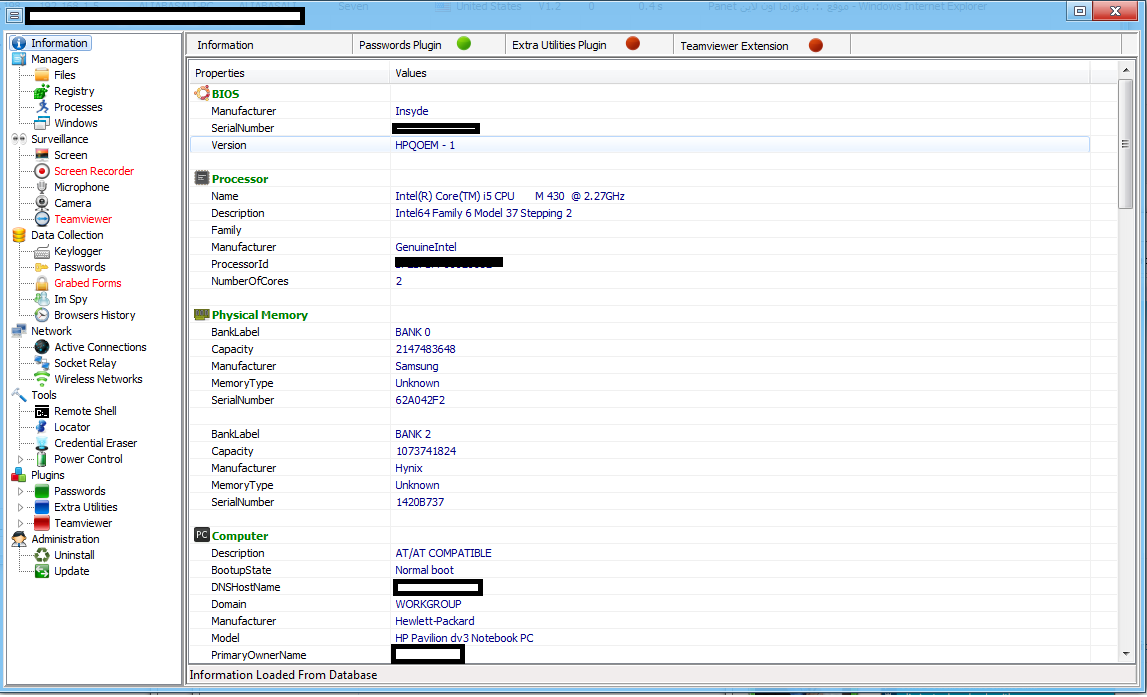
Over the past year, we observed an increase in publicly available managed TDoS (Telephony Denial of Service) services. We attribute this increase to the achieved ‘malicious economies of scale’ on behalf of the cybercriminals operating them, as well as the overall availability of proprietary/public DIY phone ring/SMS-based TDoS tools.
What are cybercriminals up to in terms of TDoS attack tools? Let’s take a peek inside a recently released DIY SIP-based (Session Initiation Protocol) flood tool, which also has the capacity to validate any given set of phone numbers.
More details: read more…