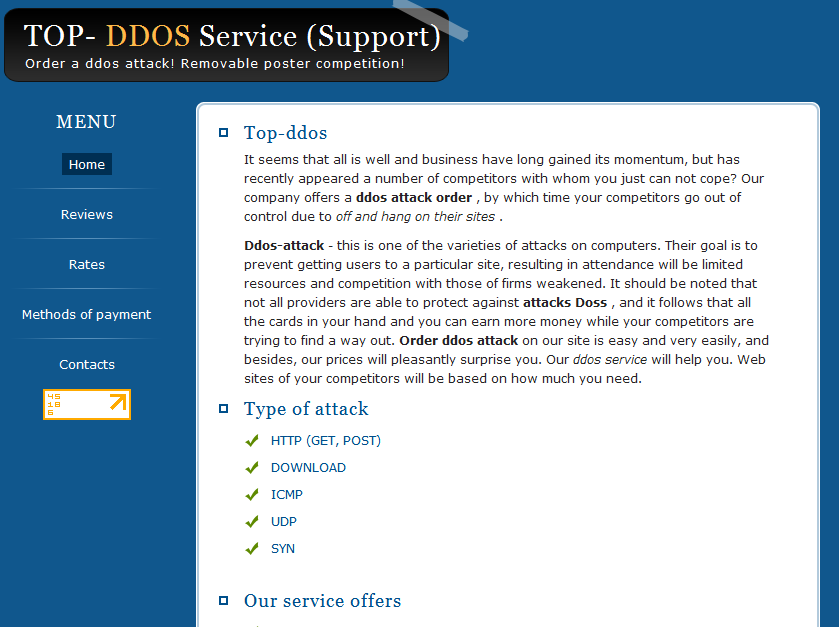
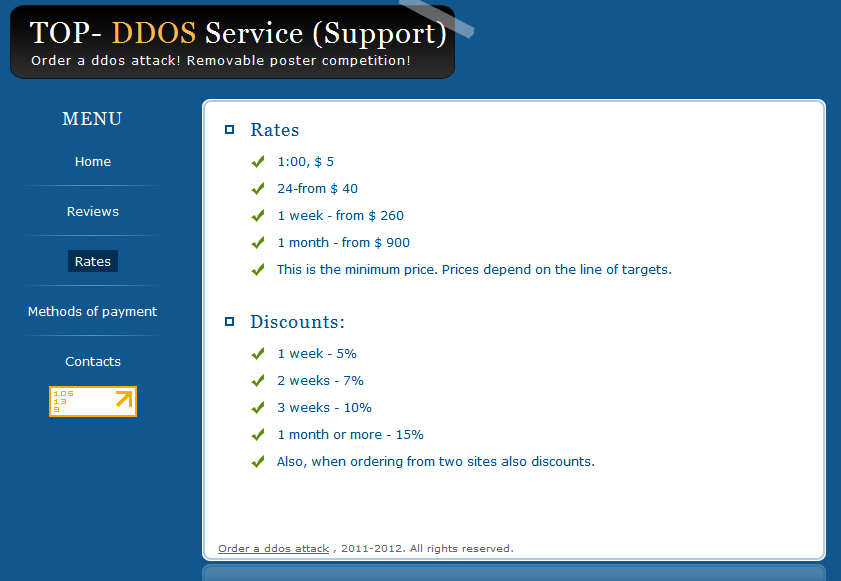
In a coordinated effort Oracle and Apple recently issued a critical security update for Java.
Next to Adobe Flash, and Acrobat Reader, client-side vulnerabilities found in insecure versions of Java are among the most popular entry points for malicious attackers on the hosts of users with outdated third-party software and browser plugins.
More details: