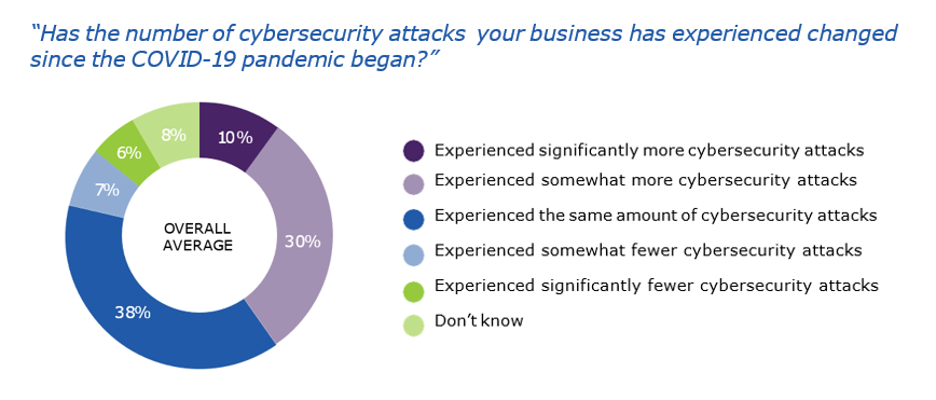
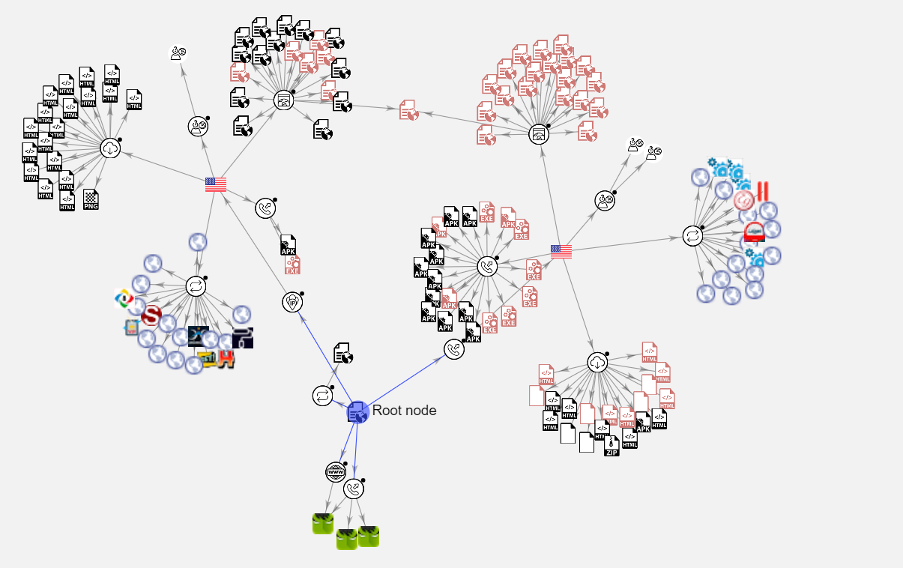
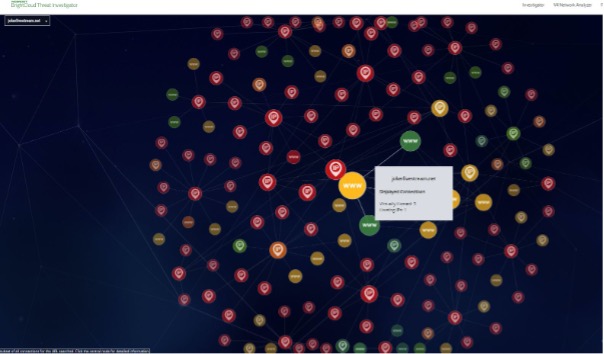
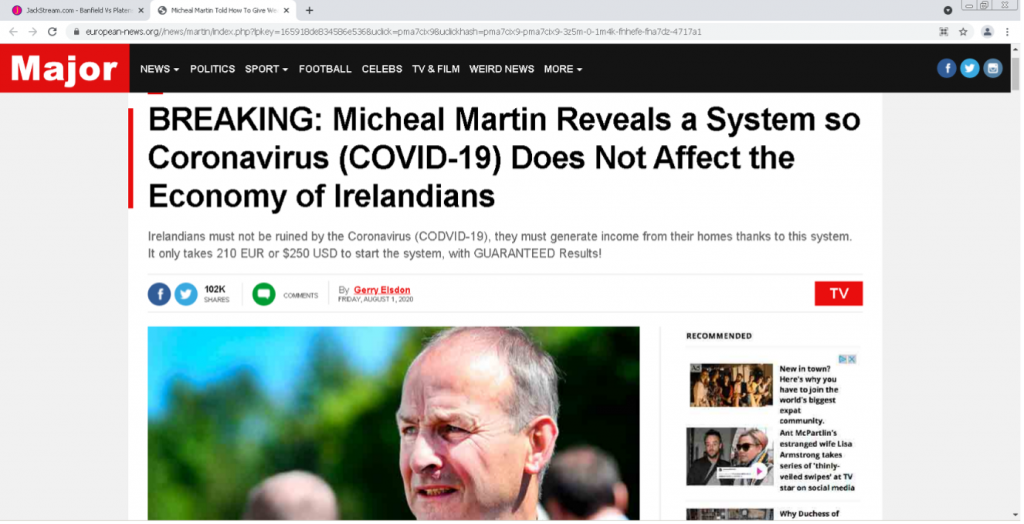
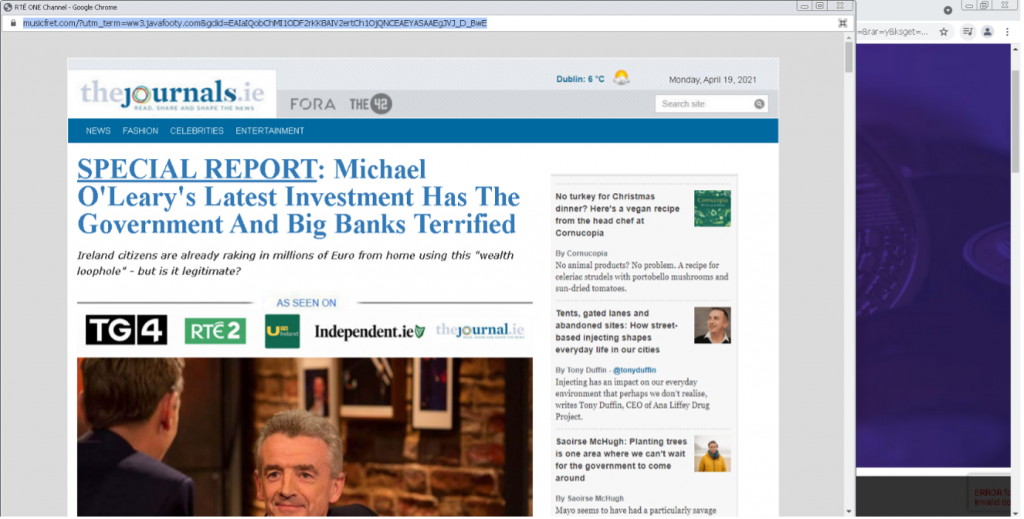
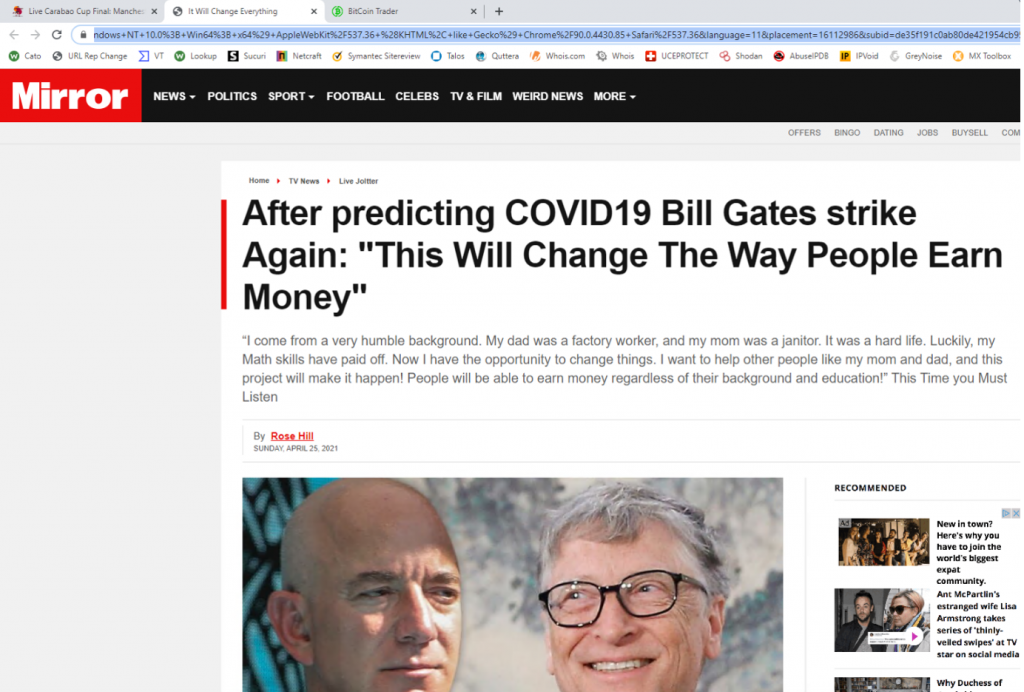
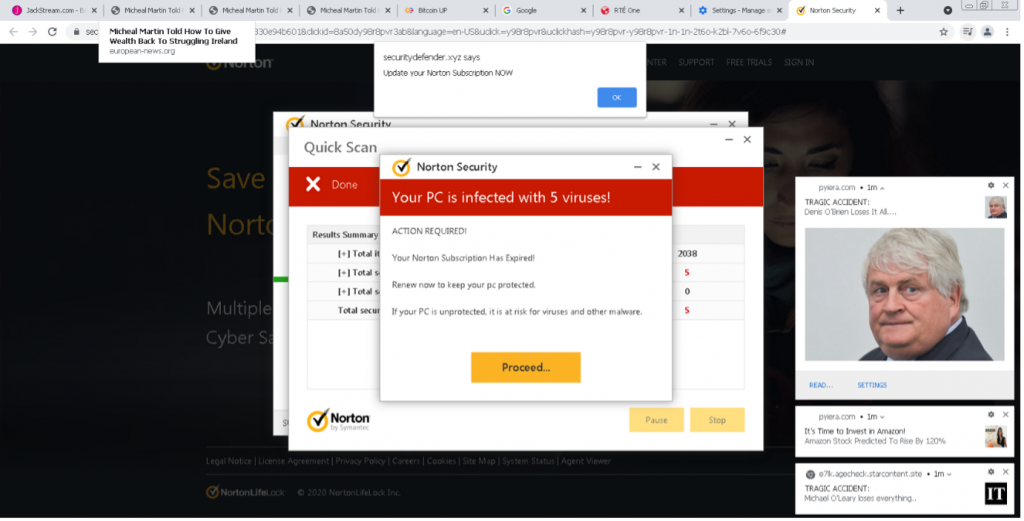
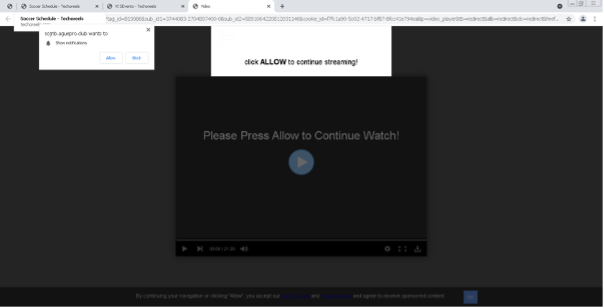
Threat actors are becoming more sophisticated, agile and relentless in their pursuit of stealing personal information for financial gain. Rapid and evolving shifts in the threat landscape require the knowledge and solutions to prepare and prevent threats that could spell disaster for organizations’ reputations and operations.
Organizations of all sizes remain at risk. Small to medium-sized businesses (SMBs) and managed service providers (MSPs) are especially vulnerable to the stealth efforts of bad actors. With fewer financial resources, a ransomware payment demand could mean the difference between staying in business and closing up shop.
Government entities are also prone to attack. In December 2021, Belgium’s Ministry of Defence experienced a cyberattack exploiting the Log4j vulnerability that paralyzed the ministry’s computer network. Within the same month, Australia’s utility company, CS Energy, experienced a ransomware attack involving the well-known ransomware Conti.
Evolving cyber threats can be unpredictable, but that doesn’t mean businesses have to tackle them alone. A robust security stack can help businesses stay protected and prepared. Establishing this level of resilience involves partnering with a provider that has human-powered threat hunting resources.
What is threat hunting?
Threat hunting involves actively searching for adversaries before an attack is carried out. Threat hunting involves the use of tools, intelligence and analytics combined with human intervention. Threat hunting centers around the proactive containment and identification of potentially damaging files before malicious vectors can cause severe damage to an organization’s operations.
What does a threat research analyst do?
“At Webroot, we focus our efforts on analyzing customer data. Our threat research analysts examine this data to determine if malicious files are present. Our analysts are constantly looking for files that possess certain characteristics that make up various types of malware. If we identify and determine that critical elements of a suspicious file are present, we classify and block them. Making determinations can be approached in different ways. One avenue of determination is carried out by creating isolated conditions to run the suspicious file to see what results it presents,” says Marcus Moreno, manager, threat research at Carbonite + Webroot, OpenText companies.
“Since our database is comprised of mass quantities of SMB and MSP data, we can continue to make determinations from a large and evolving data set. This is why SMBs and MSPs can derive value from partnering with Webroot,” adds Moreno.
Take your security stack to the next level
Cyberattacks will continue to be a concern for businesses, governments and individuals. Combatting cyber threats means adopting a cyber resilience approach. Cyber resilience is the ability to remain operational in the face of threats – whether human or maliciously-based. One important element of a solid cyber resilience strategy is to remain in a pre-emptive and proactive stance. Avoid costly ransomware payment demands, bolster customer confidence and minimize downtime for business operations by investing in a solutions provider backed by threat hunting capabilities.
Discover how Webroot’s solutions can protect your business.