The past couple of days have been very busy for a lot of people, following the announcement by Microsoft that they had discovered a new network worm called Morto. After reading the refreshingly thorough writeup about Morto from both Microsoft and our partner Sophos, we were surprised to find that a few of our customers had been infected — and cleaned up — beginning with some poor schlub in South Africa as early as July 23rd, but the worm kicked into high gear last Thursday and began to propagate rapidly.
The past couple of days have been very busy for a lot of people, following the announcement by Microsoft that they had discovered a new network worm called Morto. After reading the refreshingly thorough writeup about Morto from both Microsoft and our partner Sophos, we were surprised to find that a few of our customers had been infected — and cleaned up — beginning with some poor schlub in South Africa as early as July 23rd, but the worm kicked into high gear last Thursday and began to propagate rapidly.
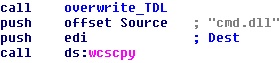
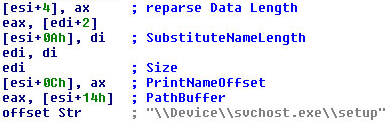
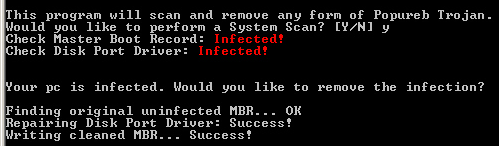
But, as much as the technical details in these posts are useful for researchers and analysts, they don’t really get to the heart of how a user of an infected computer would be affected by the worm. So, after spending a bit of time infecting some of my own machines these past couple days, I wanted to share my hands-on experience with you.
Bottom line, the worm was written to spread to (and infect) the computers run by people who don’t take security seriously: It copies itself to other computers by trying to Remote Desktop into those computers using a list of what can only be described as completely moronic passwords (the full list is on Microsoft’s technical writeup about the worm). The repurcussions are that people (or companies) who use poor quality, easily guessed passwords have been (or are going to get) spanked by Morto, and then they’ll be really irritated at the (reversible but obnoxious) changes the worm makes to the behavior of the infected computer.