(Update, July 11, 2011: On May 25, 2011, we were contacted by representatives of Future Ads, LLC, the parent company of both Playsushi and Gamevance. Future Ads informed us that they, too, had been victims of a scam perpetrated by rogue affiliates who seemed to be involved with the malicious campaigns we described in this post. Future Ads claims that it has taken action to prevent this type of abuse from happening in the future.)
By Curtis Fechner and Andrew Brandt
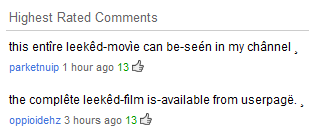 I was poking around at the end of the work day last week, checking out the newly-released trailer for X-Men: First Class. But something in the comments caught my eye: The two highest-rated commenters don’t appear to be human. Their messages invite readers (using some goofily accented characters) to visit a profile and see the whole movie.
I was poking around at the end of the work day last week, checking out the newly-released trailer for X-Men: First Class. But something in the comments caught my eye: The two highest-rated commenters don’t appear to be human. Their messages invite readers (using some goofily accented characters) to visit a profile and see the whole movie.
I’m sure the film’s director, Matthew Vaughn, would also love to see that, especially because he may not have finished shooting the movie yet. And, of course I wanted to see just how they’d manage to get “this entîre leekêd-movìe” or “the complête leekêd-film” in their user channel, given the absence of a completed film, let alone YouTube’s limits on video length.
When I click through to the profile, it suddenly makes sense. The profile links to an outside site where (the profile’s owner claims) you can watch the full movie. It only took 13 thumbs-up clicks on those comments to make those comments the most popular, but a real user isn’t going to ‘like’ glaringly obvious comment spam. The comments are probably being boosted by the spammers themselves. With just under 7 million page views, this is apparently an effective scam. Not good!