 An insidious new Trojan that finds its way onto Windows PCs in the course of a drive-by infection employs a novel method to propagate: It connects to Web servers using stolen FTP credentials, and if successful, modifies any HTML and PHP files with extra code. The code opens an iFrame pointing to a page that loads browser exploits. The exploit pushes down the infection, which then perpetuates the process. The initial infection vector in this case was a spam message supposedly from Amazon.com containing a link to the page which performs the drive-by attacks.
An insidious new Trojan that finds its way onto Windows PCs in the course of a drive-by infection employs a novel method to propagate: It connects to Web servers using stolen FTP credentials, and if successful, modifies any HTML and PHP files with extra code. The code opens an iFrame pointing to a page that loads browser exploits. The exploit pushes down the infection, which then perpetuates the process. The initial infection vector in this case was a spam message supposedly from Amazon.com containing a link to the page which performs the drive-by attacks.
The malware, which we’re calling Trojan-Backdoor-Protard, appears to seek out Web servers for which the FTP credentials may have been previously stolen in an earlier attack. Those servers all contain a pair of benign HTML tags that appears to be long strings of gibberish characters.
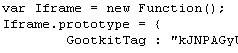
Code within the scripts this spy uses indicate the malware’s creators are calling the server modifications a Gootkit, and the gibberish embedded in the files Gootkit Tags. The Trojan also loads itself on an infected machine using a registry key, naming the service that loads either “kgootkit” or “gootkitsso.” During the course of researching the malware, we observed the Trojan modify these pages such that the Trojan inserted the malicious code between the two Gootkit Tags.
It stands to reason that, if you find these so-called Gootkit Tags embedded within files on your own Web server, you can be fairly confident that an FTP password has been compromised, and all your FTP passwords should be changed immediately.