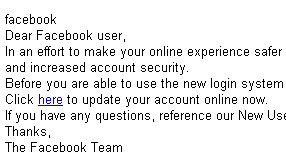
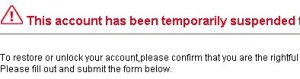
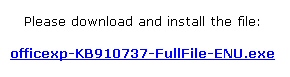
Over the past several months, we’ve seen Koobface steadily progress in its ability to infect systems with malware. In our latest tests, we’ve found that the most recent version of this social-networm has a few new holiday-themed tricks up its sleeve. Among those tricks are a new, improved “captcha breaker” utility; A tool to check whether you have a Google and/or a Blogspot account (and, if not, it creates a new Google account); And a tool designed to create Google Reader pages on the fly, which the worm then uses to post malicious code. Those Google Reader accounts then end up linked in private messages and wall-to-wall posts on a variety of social network sites.
Over the past several months, we’ve seen Koobface steadily progress in its ability to infect systems with malware. In our latest tests, we’ve found that the most recent version of this social-networm has a few new holiday-themed tricks up its sleeve. Among those tricks are a new, improved “captcha breaker” utility; A tool to check whether you have a Google and/or a Blogspot account (and, if not, it creates a new Google account); And a tool designed to create Google Reader pages on the fly, which the worm then uses to post malicious code. Those Google Reader accounts then end up linked in private messages and wall-to-wall posts on a variety of social network sites.
The Koobface-generated Google Reader pages have been floating around for a little while now, but I’d never seen the worm in action. What I found fascinating was that I could observe the process of the worm creating a new Google account on my testbed.
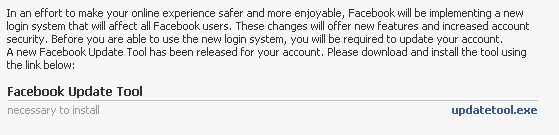
 In order to create the Google account, it downloaded and ran four new applications: “v2googlecheck” simply looks at your browser cookies to determine whether you already have a Google account; “v2newblogger” creates a new account if one doesn’t already exist; “v2captcha” prompts the user of the infected machine to enter a captcha into a dialog box that looks like a Windows login dialog (in order to complete the account creation); and “v2reader,” which creates the new page, and passes that information to the worm.
In order to create the Google account, it downloaded and ran four new applications: “v2googlecheck” simply looks at your browser cookies to determine whether you already have a Google account; “v2newblogger” creates a new account if one doesn’t already exist; “v2captcha” prompts the user of the infected machine to enter a captcha into a dialog box that looks like a Windows login dialog (in order to complete the account creation); and “v2reader,” which creates the new page, and passes that information to the worm.
Once the Google account is created, it then uses that account to generate a new, malicious Google Reader page.