As workforces migrate from offices, workflows migrate to the cloud
In March of 2020 schools throughout the United Kingdom closed their doors to try to stem the spread of the coronavirus. In addition to disruptions to the lives of students and their families, the pandemic put unprecedented pressure on IT departments across the UK and wider world.
Notoriously strapped for resources, many schools’ IT departments found themselves without access to server rooms and no way to troubleshoot for students and staff when grading, learning and teleconferencing applications encountered problems.
In 2020 this situation was unfolding around the UK, and why CloudHappi began searching for a solution for their clients. CloudHappi is a London-based provider of IT solutions tailored for the education sector. Determined to provide the best learning experience possible for remote students, the company began exploring opportunities for shifting the IT burden from on-premise servers to the cloud.
Unfortunately, many of the earlier solutions CloudHappi explored took up to 15 days to perform a complete migration, an unacceptable timeline for schools looking to establish some sense of normalcy as soon as possible. After finding Carbonite and its server migration solution, however, it was able to perform a complete migration for its first school within a single day.
As a result, IT operations for the school experienced fewer disruptions, applications were easy to access and unfortunate circumstances for students were made a little easier to handle.
Many reasons to migrate
Schools across the UK and United States are planning to open in the fall, notwithstanding uncertainty caused by the spread of the virus’s Delta variant. Vaccinations in much of the world are prompting workers to return to offices and life to start to resemble its pre-pandemic state in many ways.
But in other ways, it may never again. By some estimates, less than 35% of workers have returned to office spaces. Many companies don’t plan on requiring their workforces to come back at all. Some business leaders see remote work as a net positive, giving them access to larger talent pools, reducing pollution, freeing up time spent commuting for more productive tasks and cutting facilities costs.
Whether inspired by downsizing and office space or not renewing leases at all, there’s a good chance this shift in the workforce will require many more migrations from on-premise servers to the cloud. Not unlike in the case of UK schools, IT admins will require greater access to productivity solutions without the need for physical space in which to operate.
Aside from the flexibility of being able to access systems from anywhere, migrating to the cloud entails several knock-on benefits for businesses, whether MSPs or their clients.
- Streamlined management – By offloading server management to a public cloud like Microsoft Azure or Amazon Web Services, businesses capitalize on all the economies of scale these companies have built over years of innovation and investment. Given the resources at their disposal, most cloud companies dwarf the capabilities of small IT teams
- Enhanced security – With well-developed security policies covering things like firewalls, open ports and security teams dedicated to uncovering and patching vulnerabilities, public cloud companies often offer better security coverage than small IT teams. Even as bigger targets compared to a self-managed small business, available again give these companies the edge in terms of data security.
- High-availability – Migrating data to the cloud also puts high-availability data replication possible for businesses. While large public cloud operations are highly reliable, outages do happen. When they do, high availability cloud architecture can quickly search to an unaffected server containing byte-by-byte replication if an original happens to go down. Without a high-availability solution, to use our example of schoolchildren in the UK, video conferencing software may become inoperable and students unable to learn together. For a business, losing access to certain applications because of a cloud outage can spell disaster. If email systems or customer account portals become inaccessible the costs can mount quickly.
In a sense, COVID-19 accelerated trends in computing trends by years. While much work had been moving to the cloud for some time before the pandemic hit, the sudden need for a distributed workforce heightened its importance overnight. Luckily, migrating offers significant benefits for all types of organizations and looks to be well suited for the workforce of the future.
To learn more about the benefits of migrating to the cloud, visit the Carbonite Migrate page here.
How Ransomware Sneaks In
Ransomware has officially made the mainstream. Dramatic headlines announce the latest attacks and news outlets highlight the staggeringly high ransoms businesses pay to retrieve their stolen data. And it’s no wonder why – ransomware attacks are on the rise and the average ransom payment has ballooned to over $200,000.
But the true cost of ransomware can go beyond the headline-grabbing payments. The hit to a business’s reputation can be long lasting, as can the effect of protracted downtime. And over 15% of businesses never retrieve their data. Even more, some companies lose their data even though they pay a ransom.
That’s the bad news. The good news is that were gaining a better understanding of how ransomware attacks happen. Learning how ransomware sneaks into our personal and business lives is the key to protecting ourselves.
Risks to Small and Medium Businesses
In episode 1 of Carbonite + Webroot’s new series on ransomware, security experts, futurists and business leaders discuss the risks faced by small and medium businesses.
Before the latest surge of ransomware, some small and medium businesses could get away with thinking they weren’t a target. After all, the largest companies are the ones that can afford to pay the largest ransom payments. But the truth is there are only so many Fortune 500 companies to prey on.
Now with so many new victims of ransomware, businesses are turning to cyber security experts and asking why they’re a target. The short answer is … they aren’t. Small businesses fall victim to ransomware because of misconfigured systems, lack of proper security and human error. In other words, attackers sneak in by focusing their attention on vulnerable systems. They look for things like outdated firewalls and outdated servers because those gaps in security make for easy targets.
Protecting Your Data
Jon Murchison, CEO of Blackpoint Cyber, succinctly sums up why attacks happen, “It’s bad IT hygiene.” He’s seen municipalities attacked repeatedly because of holes in their network. He once fought off six waves of attacks, crediting Webroot’s capacity to hunt down malware and his ability to respond in real time. Without that, he guarantees there would have been a mass ransom event.
That’s why investing in cyber security is so important. With the explosion of ransomware, businesses that don’t protect themselves can fall victim to a ransomware. By establishing strong security measures, you can keep your company out of the next ransomware headline.
Acknowledging the Threat
Dr. Kelley Misata, CEO & founder of Sightline Security, says it’s an exciting time for technology, with the proliferation of IoT and mobile devices. But she adds, “people aren’t realizing that by interacting with that technology, they are putting themselves at risk for a cyber security event to happen.”
Dr. Misata has dedicated her career to helping others understand cyber security and teaching them how to adopt best practices in their own lives. Because ransomware attackers look for the easiest target, she tells her clients that “it’s not just how they protect their businesses, it’s how they protect their lives, how they protect their customers, and how they protect those around them.” Ransomware doesn’t just sneak in through our work computers and business servers. If our mobile devices are vulnerable, attackers will break in that way.
First Step in Preventing Ransomware
The first step in preventing ransomware is knowing who it targets and how it sneaks in. Big businesses make headlines, but small and medium businesses are increasingly falling victim to ransomware. And more and more often, ransomware piggy backs on our personal devices to sneak into our business lives.
Taking all this together will help you to focus your efforts when you invest in cyber security. Dive into expert analysis on 2021’s ransomware surge in our YouTube series: Ransomware 2021.
Webroot top performer among security products in PassMark® Software testing
Webroot put forward another strong performance in its latest round of independent third-party testing, besting all competitors and taking home the highest overall score. In taking the highest score in the category for 2021, Webroot beat out competitors including BitDefender™, McAfee® and ESET® endpoint security solutions.
In the report, the company conducted objective testing of nine endpoint security products, including Webroot® Business Endpoint Security. Tests measured performance in 15 categories including:
- Installation size
- Boot time
- CPU usage during idle and scan
- Memory usage during idle and initial scan
- Memory usage during scheduled scan
Webroot stood out in several categories in addition achieving the best overall score. Some categories were won by a wide margin.
Consider installation time for instance. Webroot completed installation in just over four seconds, while the next fastest installation time was more than 17 seconds and the average for the category was over 162 seconds.
According to PassMark, this metric is important because “the speed and ease of the installation process will strongly influence the user’s first impression of the security software.”
Installation size was a similar case. It is an important metric because as PassMark puts it, “In offering new features and functionality to users, security software products tend to increase in size with each new release.”
Webroot also took home top honors when it comes to memory usage. In both memory used while idle and during scan, Webroot was the least impactful to system resources.
The reason Webroot performed so well in this test is not by accident. By design, much of the “heavy lifting” of endpoint security is done in the cloud. This ensures the highest level of efficacy while also reducing the performance impact at the endpoint. Businesses should not need to sacrifice performance for efficacy.
Additionally, Webroot took the top spot in the categories of memory usage during memory usage during initial scan, memory usage during scheduled scan, scheduled scan time and file compression and decompression.
PassMark® Software Party, Ltd. specializes in “the development of high-quality performance benchmarking solutions as well as providing expert independent IT consultancy services to clients ranging from government organizations to major IT heavyweights.”
Redundancy for resilience: The importance of layered protection in the cloud
At Carbonite + Webroot, we’re always preaching about the importance of layering security solutions. Because here’s the truth: data’s always at risk. Whether from cybercriminals, everyday mishaps or mother nature, businesses can put up all the defenses they want but disaster only has to successfully strike once.
The global pandemic means more work is being conducted in the cloud, so this is no time to be lax with the security of cloud backups. Unless protection is redundant, organizations risk of losing mission-critical data – for minutes, days or permanently depending on the disaster – and putting their survival at risk.
That’s why layered protection in the cloud is so critical to cyber resilience. Without it, any one failure can be catastrophic.
So, how’s it done?
Let’s start with endpoints
For organizations managing hundreds or thousands of endpoints, backing each up to the cloud is important for keeping employees productive in the case of hardware failure, device theft, damage or malicious insiders. It’s easy to see how a laptop can be damaged, so it’s obvious for most that files stored locally should be backed up to the cloud.
But it’s also important to recognize that work done in the cloud should also be backed up. For example, one of the world’s most popular productivity tools for office workers, Microsoft 365, increasingly carries out its core functions in the cloud. But it has some serious gaps in terms of backup capabilities.
The average endpoint user may not know or care which important work files are stored, so long as they’re there when needed. This makes it important that Microsoft 365 data is backed up to the cloud – regardless of whether the user is aware if updates are being made locally or if the location is using its cloud capabilities.
Finally, but in the other direction, cloud-based cybersecurity offers another form of data security from the cloud. This method avoids the risk of endpoints relying on out-of-date file definitions of known-bad files, instead relying on near real-time threat telemetry from the cloud. This allows for the near real-time protection of all endpoints using the solution once a threat is identified.
But must also include servers
It’s less obvious to many of us that servers are at risk of becoming ground zero for data loss as well. Hardware sometimes fails, power cords can be tripped over, or worse…natural disasters can strike data centers, wiping out servers through fires, floods or other types of damage.
What good are endpoints without the servers that feed them information? Cloud computing technology offers a handful of flexible opportunities for backing up data housed on servers.
On-premise servers – used to store data locally based a business’s preference, regulatory needs or other reasons – can and should still be backed up to the cloud in case of a localized outage. Usually this entails concentrating data within a single point of storage (a “vault”) that’s then bulk uploaded. This duplicated data can then be accessed in the event a physical location loses power or a fiber optic cable is severed by construction work, for example.
Off-premise server banks also can and should be protected by cloud backups. Many of these servers may store their data in public clouds, which are normally but not always highly reliable. Public cloud outages do happen. When they do, it pays to have another cloud backup solution to failover to so the business can continue to run.
Whether or not this data is stored in the cloud permanently or migrated there when needed, redundancy is established when on and off-premise server banks are backed up to the cloud.
Rounding out the redundancy is a disaster recovery as a service (DRaaS) solution. This form of high-availability replication anticipates a worst-case scenario for server data loss. With DRaaS, byte-level replication of changes on an organization’s systems are sent to the cloud. In the event of a disaster, you
Note that DRaaS is not to be confused with being a replacement for backup. These are two different solutions that can work perfectly well alongside each other. Backup should apply to every server in an environment and offers long term retention with flexible restore options. DRaaS typically would be layered on top of backup, for the most mission critical servers, resulting in options to either restore from backup, or failover directly and rapidly to another cloud depending on the event that has rendered the production server or data inaccessible.
Maintain uptime, all the time
Threats to business data are all around us. Rates of ransomware are rising and remote workforces have ballooned since the outbreak of COVID-19. This is no time to trust in a single cloud as an organizational backup strategy. No single point of failure should keep users from accessing business-critical data. Luckily, there are many options for designed layered backup across clouds.
What’s the difference between high availability and backup again?
It’s not just that they’re making headlines more often. Ransomware rates really are rising. Given the recent spate of high-profile attacks, it’s worth remembering the difference between standard backup and high-availability replication.
Our research suggests that the costs of ransomware for businesses can amount to much more than an extortion payment. They include lost hours of productivity, reputational damage, compliance fines and more. But maintaining access to critical data at all times can undermine ransomware actors’ leverage over an organization, reduce recovery time and earn the good graces of regulators and the public.
Ultimately, doing so comes down to answering the question: what data does my business simply need to back up, and what data can my business simply not do without? Knowing the difference helps to determine the Recovery Time Objective (RTO) for a given type of data or application.
A 24-hour recovery time may fall within the RTO for non-essential data and applications. For mission-critical data, on the other hand, a 24-hour recovery period may exceed the acceptable amount of time to be without access to data. It could drive up the cost of data breach significantly, perhaps even higher than a ransomware payment.
Also, it may come down to the amount of change-rate data that can be acceptability lost. Knowing the acceptable Recovery Point Objectives (RPO) can be as important as knowing the required RTOs. For instance, a highly transactional system performing critical Online Transaction Processing (OLTP) could not afford the loss of data that occurred between backup cycles.
Well-designed data backup plans tend to be a blend of both standard backup and high availability, so it helps to know the difference when determining which is the better fit for a given system, application or set of data.
Data backup
There are all sorts of good reasons to keep regular, reliable backups of business systems. These may concern the normal conveniences of document retention – not having to begin a project from scratch in the case of accidental deletion, for instance – or to satisfy industry or legal compliance regulations.
These backups are taken at pre-determined time intervals, typically once a day during non-working hours, and stored on a backup server. Often backups will be given an associated value called a retention. A retention allows organization to keep certain backups for a longer period of time. For instance, a business may decide it’s necessary to keep daily backups for a total of 30 days. But due to storage concerns, they will drop off the server on day 31. However, regulations or corporate policies may require keeping certain backups longer, so often they will designate a monthly of a yearly backup that has an extended retention for one or even up to seven years.
Recently, backup servers have been targeted by ransomware actors. Criminals will study an organization’s environment and specifically backup services. Therefore, it’s extremely important to have a backup for the backup. One of the preferred methods is a secondary cloud copy of the backup server. Since the cloud copy sits on a separate network, it provides a layer of security making it more difficult to span the separate cloud network and target the secondary backup copy.
In most cases, backups like those discussed above have recovery times of hours for a localized power outage or even days for a flooded server room, for example. For an HR system, this RTO may be acceptable. For a point-of-sale system, this could mean significant lost revenue.
High availability
When a backup’s RTO and RPO time values do not meet the needs for recovering a company’s critical systems (OLTP servers, for instance), high-availability replication is an effective alternative for ensuring required operational performance levels are met. High-availability replication accomplishes this by keeping an exact copy of critical servers, maintained by real-time, byte-level replication, which remain powered off until needed.
When that time comes, a failover procedure is initiated, and the copy assumes the role of the production system. The failover process typically occurs within a matter of a second or minutes, depending upon the server configuration or network latency. In cases of hardware failure or data center disasters, high-availability replication can stave off a data loss disaster.
However, since replication is real-time, an offline copy can be corrupted if the primary is attacked by ransomware. Therefore, system snapshots may be required to maintain clean point in time copies of the system. Snapshots are typically non-intrusive, do not noticeably delay replication and provide a failover with a better RPO than backup.
Like with backup, an off-site cloud solution can step in if on-site servers are out of commission. Latency can slightly lengthen recovery a small amount as the off-site cloud boots up, but the time to recovery still feels like a blip to users or customers.
For some organizations there may be no data critical enough to warrant implementing this high-availability architecture. For others, all data may be considered essential. For most, the reality will be fall somewhere in the middle. If companies are highly regulated or mandated by specific corporate retention requirements, a combination of high-availability replication and backup will likely exist for the same server.
Ensuring resilience against ransomware
In a blended backup/high-availability strategy, what matters most is deciding which systems are backed up by which before the worst happens. Whether handling backup for your own organization or for clients’, it’s important to have a well-tested backup plan in place that takes in RTOs based on acceptable amounts of downtime for data and applications.
4 ways ransomware can cost your business (in addition to extortion)
Cybersecurity analysts are charting both a rise in ransomware incidents and in amounts cybercriminals are demanding from businesses to restore their data. That’s bad news in itself, but what’s often overlooked are the additional ways – beyond payments victims may or may not choose to make– victims pay for these attacks.
Our latest threat report found the average ransomware payment peaked in September 2020 at more than $230 thousand. But the ransom alone doesn’t tell the whole story. To do that, we conducted another study to tally and quantify the collateral damage from surging ransomware incidents and rising extortion amounts.
These are some of those affects inflating the price tag of an attack, which we call The Hidden Costs of Ransomware.
1. Lost productivity
Our survey data found that hours of lost productivity from a ransomware incident were closely related to the length of time to discovery of the attack. Generally, faster detection meant limiting the spread of the infection and less time spent on remediation. In other words, the further ransomware spreads the longer it takes to eradicate. Unfortunately, almost half (49%) of respondents to our survey reported being unaware of the infection for more than 24 hours.
A third of incidents were reportedly remediated in 1-3 hours, while 17 percent required 3-5 days of effort. We attempted to quantify these lost hours based on hours spent on remediation (easily measurable) and the opportunity costs from diverting resources from IT teams’ “blue sky” responsibilities (tougher to measure).
Factoring in varying costs of IT resources, we determined low/high cost estimates for hours of remediation reported by survey respondents. These ran from $300/$750 for three hours or remediation to $4,000/$10,000 for five workdays of remediation. (A full breakdown is available in the report.)
2. Downtime costs
Regardless of whether an organization decides to pay a ransom, how long does it take to return to normal operations?
In our study, businesses that didn’t pay ransoms had recovered their data quicker than those that didn’t pay. Specifically, 70 percent of companies that didn’t pay a ransom were able to recover their data within a business day, compared to 46 percent that did.
Presumably this has to do with whether a target had readily available backups, and lost time due to back and forth with extortionists or time spent making a payment.
One of the most important factors in determining downtime costs is specifying the value of the data that’s become unavailable. Is it critical to conducting business operations? Or is it nice to have but not essential like marketing or prospecting data?
Determining data’s value helps businesses formulate their recovery time objectives (RTOs). For non-critical data and applications, a 24-hour recovery time may fall within the RTO. For mission-critical data, a 24-hour recovery may exceed the tolerable limit and help drive the cost of downtime higher than the ransom itself.
3. Impact on client operations
Nearly half (46%) of the businesses in our survey reported client operations being adversely affected by a ransomware incident at their own company. This could quickly sever business relationships that take a long time to build and result in the loss of anticipated revenue. But that’s not even be the riskiest aspect of client operations being affected.
The implications of supply chain attacks, especially for MSPs, came into sharper focus last year following the SolarWinds attack. Were a cybercriminal to compromise a trusted supplier to distribute ransomware, rather than for surveillance as in that attack, the costs could be enormous.
MSPs should seriously consider the possibility of becoming the source for such a supply chain attack, especially those with clients in critical industries like energy, public utilities, defense and healthcare.
4. Brand and reputational damage
Consider the headlines and airtime generated by ransomware attacks against high-profile targets. A Google search of “Garmin ransomware,” for instance, returns more than 1 million results. While your organization may not be a global tech giant, it also likely doesn’t have the staying power of one.
In our study, 38 percent of businesses admitted their brand was harmed by a run-in with ransomware. Beyond lost customers, publicity issues could force businesses to enlist the services of expensive PR or communications firms to repair the damage.
Businesses with the resources to do so should consider themselves lucky, because the alternative is worse. Silence or an uncoordinated response to a ransomware attack – especially one that affects customers – can come of as unserious, callous or ineffective.
Reputational damage in an age of heightened sensitivity to cybersecurity incidents can have significant consequences. Our data shows that 61 percent of consumers switched some or all their business to a competing brand in the last year, and 77 percent admit they retract their loyalty now quicker than they once did.
The list goes on…
By no means is this an exhaustive list of the hidden costs of ransomware. They extend to fines for breaches of compliance regulation, the rising costs of cybersecurity insurance and a host of other unforeseen consequences.
For the complete findings from our survey and our recommendations for not encountering these hidden costs, download the full report.
Podcast: How to build a cyber resilient business
Cyber resilience refers to a business’s ability to mitigate damage to its systems, processes and even its reputation. It’s based on the principle that, in the real (and really connected) world, adverse events occur. This could be in the form of a user enabling a breach by providing sensitive information during a phishing attack, through a new threat known as a “zero day” being weaponized against a business, or an event of any complexity in between.
When it comes to building a cyber resilient business, technology is an important piece. But it’s not the only one. A well-rounded security strategy is also essential. People and processes are key ingredients when it comes to that.
Audit checklists are a great place to start when ensuring your business is taking a holistic approach to data security, and so is this revealing conversation with Channel E2E and MSP Alert editor Joe Panettieri and a product marketing expert at OpenText.
The two discuss how there’s no silver bullet to all the potential threats to your data security, but how adapting the right mindset can help organizations begin to think about security differently. Our experts cover the “train, block, protect, backup and recover” model and what solutions for each can look like as a part of a real-life security stack.
The two touch on the importance of user security training, variables introduced by widespread remote workforces and how backup can undermine ransomware actors. Whether you’re designing a cybersecurity framework for your own business or putting one in place for clients, you won’t want to miss this conversation.
Podcast: Can we fix IoT security?
For many U.S. workers the switch to remote work is a permanent one. That means more high-stakes work is being conducted on self-configured home networks. For others, home networks are simply hosting more devices as smart doorbells, thermostats and refrigerators now connect to the internet.
Security experts warn that while the internet of things (IoT) isn’t inherently a bad thing, it does present concerns that must be considered. Many devices come pre-configured with inherently poor security. They often have weak or non-existent passwords set as the default.
As our guest and host Joe Panettieri discuss, these are issues that would be addressed on corporate networks by a professional IT administrator. The conversation covers the issues of IoT and home network security both from the perspective of the average family household and what the age of remote work means for employees working on their own networks.
Security intelligence director Grayson Milbourne brings a unique perspective to the podcast. Having held senior roles in both threat intelligence and product management, Milbourne is acutely aware of what the threats security products come up against. He knows both the cyber threat landscape and the consumer internet security market, so he’s able to provide insightful advice for how tech-loving homeowners can keep personal networks powerful and protected.
Milbourne suggests problems of IoT and home network security could be addressed with a cybersecurity version of ENERGY STAR ratings. A program could formalize current IoT security best practices and incorporate them into a standard consumers recognize.
During this informative podcast, Panettieri and Milbourne discuss that idea and more cybersecurity topics related to IoT devices. They cover:
- The difference between device security and the security of the app used to control it
- How to leverage user reviews while researching IoT devices and what security concerns to check on before buying
- Privacy and data collection issues, including why one of the most common IoT devices may be among the most intrusive
- Configuring IoT devices to prevent them from joining rogue IoT zombie networks
Your password is too predictable
Password predictability is one of the most significant challenges to overall online security. Well aware of this trend, hackers often seek to exploit what they assume are the weak passwords of the average computer user. With a little bit of background information, “brute forcing” a simple password is a straightforward undertaking.
How are passwords cracked?
Cybercriminals use computing power to crack passwords with a method known as a brute force attack. With this method, an attacker guesses at the password repeatedly with the help of computer software/scripts. This makes the process automated and essentially effortless for the attacker.
The weaker the password (meaning the easier it is to guess), the quicker an attacker can crack with computing power.
So, how do we combat this?
The problem is password predictability
Passwords can be very easy to guess. Ironically, one factor that contributes to this is one that’s supposed to make passwords safer; the uniform standard most websites impose on users when creating a new password. Typically, sites require a single capital letter, at least 6 charters, numbers and one special character.
Attackers can use this information to guess when and where each character may be using only the predictable tendencies of human users. And because many users create a single password that meets these requirements and use them on multiple sites like Netflix, Facebook and Instagram, getting lucky once can lead to a bonanza for cybercriminals.
Here is an example of a password that would meets the requirements of most websites:
Example1234!
This would be considered “secure” in most cases because it meets the most common internet standard for password creation. Now swap “Example” out for the name of a child or pet, and the easily remembered combination is very likely to be someone’s actual, real-life password. It’s easy for the user to remember, and therefore convenient to use across multiple sites.
Let’s assume a user has a pet named Toby and plug it into the above example format.
Toby1234!
This is not a strong password. Pet’s names, children’s names and birthdays are often easily discoverable, especially by mining social media accounts. An attacker may just need to do a little recon on Facebook to scrounge up a handful of likely options.
Passwords vs. Passphrases
A password is a short character set of mixed digits. A passphrase is a longer string of text making up a phrase or sentence. The important thing to know about passphrases is that, when allowed, they’re far more secure than passwords. The idea that a password should be one word is outdated and retiring it would benefit user security greatly.
A method for devising a passphrase is to simply pick a line from your favorite movie, book or song and mix it with capitals and numbers. If we take Arnold’s famous line “I’ll be back,” we can easily make it into a secure passphrase.
Original: “I’ll be back”
Remove quate marks and spaces, since they can’t be used as password inputs.
Illbeback
Add some capitals: iLLbeBack
Add Numbers: iLL3beBack
And finally, a special character: iLL3beBack$
As a fun test, you can use this password-checking tool to see how long it would take a computer to crack your new creation. How long would it take to crack yours?
For comparison, let’s take one of our simple password examples from above and see how long it would take to crack. We can use Toby1234! (and yes, some people do use such simple passwords).
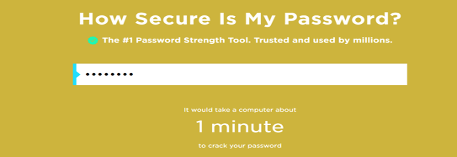
As you can see, it wouldn’t take long at all.
What about our new passphrase iLL3beBack$
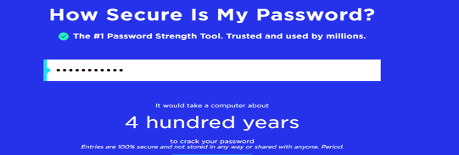
I think we’ll be secure for now.
More tips and tricks for password safety
Using a password manger is the most practical way for making passwords more secure. Users tend to gravitate toward the most convenient solution to a given problem, and password managers keep them from having to memorize a series of complex passwords for different sites. The user can automatically save passwords with an internet browser plugin and let autofill features handle the rest.
Here are some other good rules of thumb for password safety:
- Use a password generator
- Use two-factor authentication (2FA) as much as possible
- Don’t reuse passwords
- Be unpredictable in password formatting
Don’t let a predictable password come back to bite you. When made up of easily guessable public information, a weak password can be cracked in minutes. Instead, choose a passphrase or rely on one of the many secure password management tools available on the web today.
An MSP and SMB guide to disaster preparation, recovery and remediation
Introduction
It’s important for a business to be prepared with an exercised business continuity and disaster recovery (BC/DR) plan plan before its hit with ransomware so that it can resume operations as quickly as possible. Key steps and solutions should be followed to prepare and respond to cyber threats or attacks against your organization.
It may be as simple as the deployment of antivirus plus backup and recovery applications for your end users, or a more complex approach with security operations center (SOC) tools or managed response solutions coupled with network security tools such as DNS and Web filtering, network and endpoint firewalls, VPNs, backup and recovery and others.
It’s also essential to ensure end-users are trained on ransomware threats as a part of a good security awareness training program. The bottom line is, if prevention tools and training fail and your organization is compromised, you need to have a protection plan that gets your company assets and resources back to work quickly and securely.
What preparation is needed
When contemplating an in-depth plan, specific questions come to mind—the whats, the hows, the whys, and most importantly, the whos must be defined in the plan. When asking these questions, we need to be prepared to identify the resources, people and applications inlcuded. We must determine how to react to the situation and execute the logical steps and processes required to reduce damage as quickly as possible.
Below are some questions to get us started.
Key questions
- Who will be involved in recovery and communication when your DR plan is in action?
- How much downtime can your organization withstand?
- What service level agreement (SLA) do we need to provide to the business and users?
- What users do we need to recover first?
- What tools do we have to reduce risk and downtime within the environment?
- How are user networks separated from operational or business networks?
- How quickly can data protection tools get us up and running again?
- Can users get their data back if an endpoint device is compromised?
- Can we determine when the ransomware first hit the network or endpoint devices?
- Are we able to stop the proliferation of ransomware or malware throughout the network?
- Can we recover quickly to a specific point in time?
- Can our users access their data from the cloud before it has been restored?
Application Needs
The solutions below, coupled with an exercised BC/DR plan, will help reduce your organizational risk exposure and allow for quick remediation.
- An endpoint security solution capable of determining what events took place and when
- A DNS security solution capable of turning away security threats at the network level
- A solution for endpoint backup and recovery that can safeguard data should these other solutions be compromised
Lines of Communication
Equally important as the technology are the people who manage and maintain the systems that support the different business units within an organization. For example, your security team and your endpoint support team need to be in regular discussions about how the teams will communicate when under attack. You need to determine who is responsible, what systems, and when they should be brought into the process when under attack.
System Response Ratings
A system response rating system can assist in determining which systems or employees require a higher degree or speed of response. To do this, organizations must specify the value of the system or resource and where that resource sits regarding protection or remediation priority. This is often determined by the value of the resource in monetary terms. For example, suppose the loss of a specific system would incur a massive loss of incoming revenue. In that case, it might be necessary to place a higher priority in terms of protection and remediation for it over, say, a standard file server.
The same can be said for specific individuals. Often C-level resources and mid-tier executives need to be out in front of a situation, which highlights the importance of making sure their resources like laptops and portable devices are protected and uncompromised. They are often as important as critical servers. It is necessary to classify systems, users and customers regarding their criticality to the business and place priorities based on the rating of those resources.
Now that we know a bit of the who, what, and how, let’s look at how to recover from a single system to an entire enterprise.
Recovery and Remediation
Recovery is an integral part of any BC/DR plan. It gives organizations a playbook of what to do and when. But it’s not enough to recover your data. Admins also need to understand the remediation process that should be followed to prevent further infection of systems or proliferation of malware within an organization.
Scenario
Ransomware hits user’s laptops, encrypting all of the data. The laptops have antivirus protection, but no DNS protection. All network security is in as firewalls and VPNs, with some network segmentation. There is also a security team in addition to the end-user support team. The ransomware that hit is polymorphic, meaning that it changes to prevent detection even if the first iteration of the ransomware is isolated.
Solution
The first step is consulting the endpoint security console to learn when and where the malware was first seen. If backups are still running, they should be suspended at this point to prevent infected data from being being backed up with malware. This can be done either from the dashboard or from an automated script to suspend all devices or devices that have been compromised.
A dashboard should provide the ability to do single systems easily, while scripts can help with thousands of devices at a time. APIs can help to automate processes like bulk suspend and bulk restore of devices. At this time it may be prodent to block traffic from the infected areas if network segmentation is enabled to prevent the spread of malware.
Now it’s time to review the protection platform to determine the date the file was noticed, the dwell time and when the encryption/ransomware started executing. Once these facts have been determined, it’s possible track down how the organization was breached. Understanding how malware entered the network is critical to prevent future infections. Since, in our example, ransomware infected devices, a tested and reliable recovery process is also necessary.
Understanding the timeline of events is critical to the recovery process. It is essential to know the timing for the first step in the restore process to set your time to restore. Once an admin can zero in on date and time to restore, affected devices can be compiled into a CSV file and marked with a device ID number to reactivate any backups that were halted once the breach was discovered..
Once the data, source, target device IDs, date, and time to restore from are combined with a bulk restore script, a bulk restore can be pushed to the same laptops or new laptops. As heppen, solutions offering web portals can return to work quickly.
Summary
Thre right tools, planning, importance hierarchy and communication channels across a business are essential for establishing cyber resilience. Once a timeline of a breach has been determined, these elements make restoring to a pre-infection state a process that can be planned and perfected with practice.
Oh no! A client failed a pen test. Now what?
In a previous post, we talked a bit about what pen testing is and how to use the organizations that provide them to your benefit. But, what about when one of them hands a client a failing grade?
Consider this, you’re an MSP and you get a letter or email from one of your customers that reads:
“Dear ACME MSP,
We regret to inform you that you’ve had a Penetration Test Failure produced by: “FreindlyHacker-Pentesting Inc” and we’d like to discuss the details further to determine if you have what it takes to continue to handle our security needs.
Regards,
Largest MSP Customer.”
A customer may not pass along this exact wording, but the implications are clear. The results can be embarrassing or at worst devastating. When a customer reaches out after failing penetration testing, it can put an MSP on its heels and create unnecessary angst. Should the MSP have been more involved in the testing? Did my tools cause the failure Has the MSP soured its relationship with its client? Will the business be lost?
So, how should an MSP respond when a customer fails a pen test?
Some MSPs turn to self-doubt and start wondering if the layers of protection they’ve put in place are worth the costs. Others will immediately start pointing fingers at the tools that were identified in the pen test report. When a report comes through with a failure, it’s usually unexpected and can take time away from more important activities.
To save time and effort if this should happen to you, here are a few key elements of a good response to a pen test failure.
Immediately start asking questions.
- What kind of penetration testing was involved?
- Who performed the testing and what are their credentials?
- How was the penetration testing organization positioned to start taking action?
- Where the testers acting as “Red Team” or “Blue Team” actors?
- When did the testing take place?
- May I examine the data and reporting?
Review your tools configurations.
Rather than immediately assume bad tech, it’s best to step back and evaluate each tool identified in the pen test report and the associated configurations, policies and control points. Often, a security tool is designed to identify, evaluate and/or stop bad actors along the threat chain. If it failed, it could be that a setting was disabled or miss-configured. Review all tools’ “best practice” guides, documents and suggestions before making assumptions.
Ask for partnership with the customer during their next review.
If the customer did not provide a heads up or pretesting communication, request that you be more involved during their next review. If pen testing is important enough for them to do once, it’s probably that they’ll do it bi-annually or annually, depending on the industry and regulatory concerns. It’s always good to be involved in advanced than after the fact.
Blue Teams vs. Red Teams: Which type of test was conducted?
The difference between a Blue Team and Red Team is how much previous access they have to a target’s networks and devices. This can make a huge difference in how the results of a pen test are interpreted. When a Blue Team—with some previous knowledge of an organization and its IT systems—is able to breach a business, it may not be representative of real-world circumstance. It could be an internal IT admin who was able to find a vulnerability after poking around in a system she previously had access to.
When a Red Team compromises a client, on the other hand, it’s time to examine the reporting closely. Starting with zero knowledge of an organization’s systems, this type of breach could point to serious flaws in the defenses an MSP has set up for a client. Likely there are real holes here which need to be patched.
Evaluate the pen testing organizations
While there are many levels of testing capability, keep in mind that pen testers come from many IT walks of life. Former sysadmins, hackers and network administrators make the most common tester. They come with their own experiences, specialties and biases.
One question to always ask is, what are the testing organizations credentials? What is their background and how did they come to the business? How long have they been testing?
The goal is to guage whether the individuals who’ve conducted the test are knowledgeable enough to make judgments about your organization’s defenses? Did they actually breach the defenses or are they simply reporting on a “potential” for a breach?
Not all testers are alike, not all testing organizations are alike. Each has to successfully make the case of its own expertise in coming to the conclusion that it has.
As I say, trust but verify. And be prepared to ask LOTS of questions if a client ever fails a pen test.
An Inside Look at Cybercrime-as-a-Service
You’ve likely heard of software-as-a-service (SaaS), infrastructure-as-a-service (IaaS), and numerous other “as-a-service” platforms that help support the modern business world. What you may not know is that cybercriminals often use the same business concepts and service models in their own organizations as regular, non-criminal enterprises; i.e., the same practices the majority of their intended victims use.
As senior threat research analyst Kelvin Murray explains to Joe Panettieri, editor of Channel E2E and MSSP alert, in our most recent Hacker Files podcast, cybercrime-as-a-service “essentially follows the same path as most as-a-service things in business.” He goes on to explain, “If you were a small company in 2002 and needed to set up email, you’d set up a mail server, a mail relay, mail clients, and you might hire an email admin. And then you might have to set up things like spam filters yourself. People like Microsoft figured out that they could just provide all of [these services] from a web page and rent it out to companies and take all the hassle out of companies’ hands.” That’s the as-a-service model in a nutshell.
According to Kelvin, a very similar thing happened in the cybercriminal space. Effectively, talented criminals who’ve written successful malicious code have begun renting access to their own cybercrime “solutions” to lower-level criminals who either don’t have the resources or know-how to design, write, and execute cyberattacks on their own.
Of course, the people providing the so-called service don’t do so out of any goodness in their hearts; they do it for a cut (sometimes a significant one) of any profits made in an attack that uses their code.
Hear more about the evolution of cybercrime-as-a-service in the full podcast. Be sure to check out other discussions and recordings in our Cybersecurity Sound Studio.