Spamvertised bogus online casino themed emails serving adware
Cybercriminals are currently spamvertising online casino themed emails, which ultimately redirect users to a bogus casino site offering an executable download. Upon deeper examination, it appears that the download is actually adware.
More details:
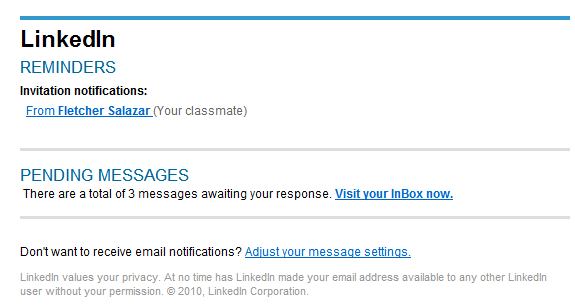
Ongoing ‘LinkedIn Invitation’ themed campaign serving client-side exploits and malware
Remember the ‘LinkedIn Invitations’ themed malware campaign which I profiled in March, 2012?
A few hours, ago, the cybercriminals behind it launched another round of malicious emails to millions of end and corporate users.
More details:
A peek inside a managed spam service
Just how easy is it to become a spammer in 2012? Too easy to be true.
Especially in times when everything needed to become a spammer, starting for a managed spam appliance, DIY email harvesters, and millions of harvested emails, are available for sale within the cybercrime ecosystem. Despite the numerous botnet take downs we’ve seen in recent years, spam and phishing attacks continue plaguing millions of end and corporate users, potentially exposing them to malicious links, malicious payloads and fraudulent propositions.
In this post, I’ll profile a Russian managed spam service that’s been in operation for 5 years, allowing novice cybercriminals an easy entry into the world of spamming.
More details:
Poison Ivy trojan spreading across Skype
Last night, a friend of mine surprisingly messaged me at 6:33 AM on Skype, with a message pointing to what appeared to be a photo site with the message “hahahahaha foto” and a link to hxxp://random_subdomain.photalbum.org
What was particularly interesting is that he created a group, and was basically sending the same message to all of his contacts. Needless to say, the time has come for me to take a deeper look, and analyze what appeared to be a newly launched malware campaign using Skype as propagation vector.
More details:
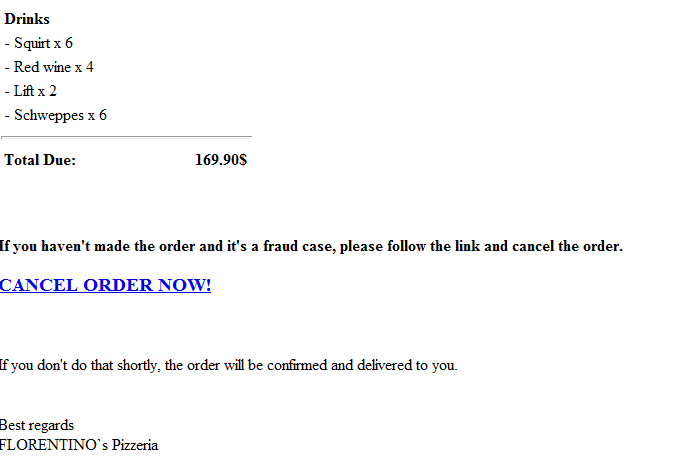
Spamvertised ‘Pizzeria Order Details’ themed campaign serving client-side exploits and malware
End and corporate users (and especially Pizza eaters), beware!
Cybercriminals are currently spamvertising hundreds of thousands of emails, impersonating FLORENTINO`s Pizzeria, and enticing users into clicking on a client-side exploits and malware serving link in order to cancel a $169.90 order that they never really made.
More details:
Cybercriminals release ‘Sweet Orange’ – new web malware exploitation kit
From DIY (do-it-yourself) exploit generating tools, to efficient platforms for exploitation of end and corporate users, today’s efficiency-oriented cybercriminals are constantly looking for ways to monetize hijacked web traffic. In order to do so, they periodically introduce new features in the exploit kits, initiate new partnerships with managed malware/script crypting services, and do their best to stay ahead of the security industry.
What are some of the latest developments in this field?
Meet Sweet Orange, one of the most recently released web malware exploitation kits, available for sale at selected invite-only cybercrime-friendly communities.
What’s so special about Sweet Orange? Does it come with customer support? What client-side exploits is it serving? How are the Russian cybercriminals behind it differentiating their underground market proposition in comparison with competing kits, such as the market leading Black Hole web malware exploitation kit?
Let’s find out.
A peek inside a boutique cybercrime-friendly E-shop
The vibrant cybercrime ecosystem is populated by a diverse set of market players. From sellers, to buyers and vendors, sophisticated cybercriminals next to novice cybercriminals, everyone is persistently looking for ways to monetize their assets and increase their revenue.
Over the past two years, the industry witnessed the maturing business models in use by cybercriminals, and the rise of the so called cybercrime-as-a-service underground market propositions. Cybercriminals of all kinds have realized that managed services are the future that offer an efficient revenue generating platform for everyone to take advantage of.
In this post, I’ll profile a recently advertised boutique cybercrime-friendly E-shop, operated by what appears to be a novice cybercriminal looking for ways to monetize his fraudulently obtained assets.
Managed SMS spamming services going mainstream
Are you receiving SMS spam? According to the latest reports, millions of mobile users do.
The trend is largely driven by what Webroot is observing as an increase in underground market propositions offering managed SMS spamming services to new market entrants not interested in building and maintaining the spamming infrastructure on their own.
In this post, I’ll profile a recently advertised managed service offering SMS spamming capabilities to potential customers, discuss the latest innovations in this field, their impact to mobile security, and what are some of the key factors contributing to the growth of SMS spam.
More details:
“You Want To Pay For What!?”
by Nathan Collier
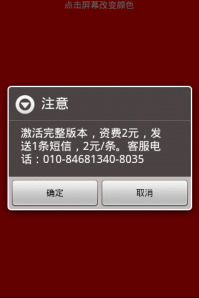
Recently we found new apps in alternative Chinese markets that we are considering a Potentially Unwanted Application (PUA). We are calling these apps Android.PUA.SMS.QuickPay. Lets look at a sample of this app. The sample we will look at is an app called “Screen Detection” which is an app that helps find dead pixels on your screen by displaying the colors red, green, blue, black, and white making it easy to see the dead pixel in contrast to these colors. Pretty simple app. Within a few seconds of opening the app this message pops up:
“Activate the full version, charges 2 Yuan, sending an SMS, 2 /. Customer Service Phone :010 -84681340-8035”
This app has limited functionality before requesting a premium SMS be sent for the full version, and that limited functionality only lasts a few seconds. If you do not agree to sending the premium SMS the app will just keep asking you to activate the full version whenever you click. Once you agree to the message it turns on your Wifi if not already on (Okay, that’s a little fishy), and sends a premium text message. After that the app works. Two Yuan is about 32 US cents, so people may just pay the small fee instead of spending the time to find a free version; which with a simple app that only shows four different colors as it’s functionality you would think there is something out there in the Chinese android market that will do the same for free.
It may not seem like much, but two Yuan at a time these guys are making a fortune off of apps that should be free. This is only one sample, there are several more very simple apps that we found that do various things, but all ask for a payment for it to function. Although there are legitimate Android Box apps out there, these apps are different in that they have very limited functionality, are signed by a different developer, and exploits simple apps that should be free by requesting payment for full versions before you even have a chance to see what it does.
Remember to always download from apps from a trusted source and be weary of messages asking to pay money for the full version so quick on the draw.
London’s InfoSec 2012 Event – recap
As many of you know, Webroot attended London’s annual security event — Europe’s largest 3 day security show — last week.
The show was a blast! Countless number of new partnerships being formed, dozens of press briefings on a daily basis, daily presentations on “Current and Emerging Trend Within the Cybercrime Ecosystem”, and best of all – many new users of the industry’s leading endpoint protection – Webroot SecureAnywhere Complete.
Taking into consideration the fact that a picture is worth a thousand words, consider going through the photos from London’s InfoSec 2012 event that we’ve prepared for you, to get an inside view of the event, and Webroot’s stand.
Upcoming Webroot briefing at InfoSec, 2012, London – “Current and Emerging Trends Within the Cybercrime Ecosystem”
Dear blog readers, are you going to this year’s InfoSec 2012, event in London?
If so, don’t forget to stop by Webroot’s stand G90, where I’ll be briefing our visitors on “Current and Emerging Trends Within the Cybercrime Ecosystem” on the 24th of April to 26th of April.
More details:
New DIY email harvester released in the wild
In order for cybercriminals to launch, spam, phishing and targeted attacks, they would first have to obtain access to a “touch point”, in this case, your valid email address, IM screen name, or social networking account.
Throughout the years, they’ve been experimenting with multiple techniques to obtain usernames (YouTube user names, IM screen names, Hotmail email addresses) and valid email addresses from unsuspecting end and corporate users.
In this post we’ll profile a recently released Russian DIY email harvester, and emphasize on the difference between notice and experienced cybercriminals in the context of the tactics and techniques they use to obtain a potential victim’s email address.
More details: