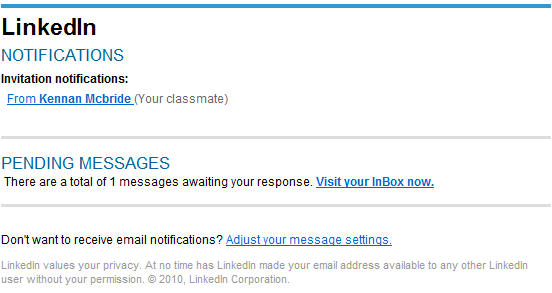
Spamvertised LinkedIn notifications serving client-side exploits and malware
Cybercriminals are currently spamvertising LinkedIn themed messages, in an attempt to trick end and corporate users into clicking on the malicious links embedded in the emails.
The campaign is using real names of LinkedIn users in an attempt to increase the authenticity of the spamvertised campaign.
More details:
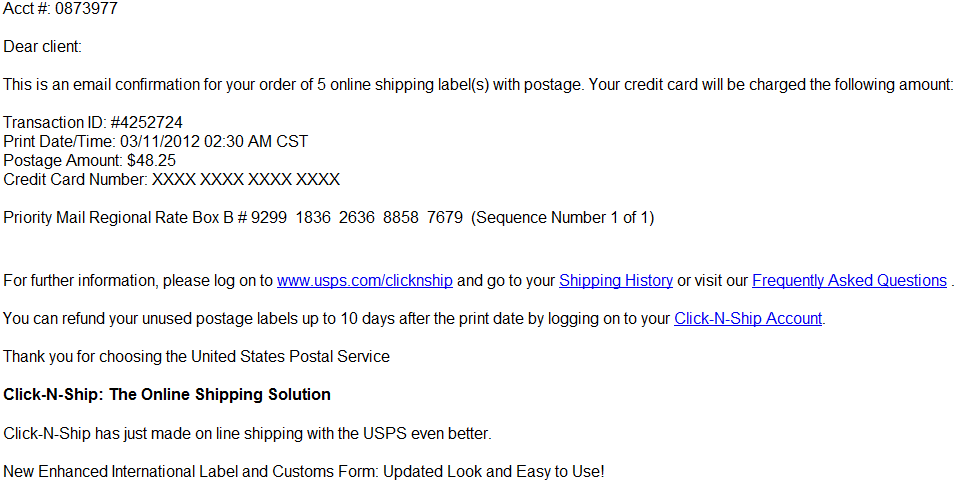
read more…Malicious USPS-themed emails circulating in the wild
Cybercriminals are currently spamvertising malicious USPS-themed emails, that entice end and corporate users into clicking on malicious links found in the emails.
More details:
Rogue APKs continue to find new homes
by Armando Orozco
We’ve been tracking rogue premium-sms Android apps for sometime now. Here’s an interesting site we came across offering a download of the Google Music application, but this one comes with a cost. This site serves up a premium-sms Trojan of the ransom variety. Targeting Russian speakers these Rogue’s, we call Android.FakeInst, offer to give access to the app but for a fee.
Spamvertised ‘Your tax return appeal is declined’ emails serving client-side exploits and malware
Cybercriminals are currently spamvertising with IRS (Internal Revenue Service) themed emails, enticing end and corporate users into downloading and viewing a malicious .htm attachment.
More details:
Trojan Downloaders actively utilizing Dropbox for malware distribution
By Curtis Fechner
It’s never surprising to see the multitude of tactics a cybercriminal will use to deliver malware. In this case, I came across a collection of files masquerading as RealNetworks updater executables. These files were all located in a user’s %AppData%realupdate_ob directory, and the sizes were all quite consistent.
At first glance there was nothing too special about this finding – malware appearing to be legitimate software is nothing new.
When I looked into the specific behaviors of the file, it became clearer that the software is in fact malicious, and that it is actually downloading malicious files from the popular web-based file hosting service Dropbox. These files came in two varieties: some files were randomly-named; other files were named for legitimate software. For example: utorrent.exe, Picasa3.exe, Skype.exe, and Qttask.exe.
Millions of harvested U.S government and U.S military email addresses offered for sale
Remember the underground service offering millions of harvested emails for sale profiled at the Webroot Threat Blog in January?
It appears that cybercriminals are continuing to innovate in this underground market segment by offering geolocated databases of millions of harvested emails for better targeting in their upcoming spam campaigns.
In this post, I’ll profile yet another cybercrime underground service selling millions of harvested emails to potential cybercriminals.
Research: U.S accounts for 72% of fraudulent pharmaceutical orders
Just how profitable is spam? Who’s buying the counterfeit pharmaceutical items advertised so heavily in a huge percentage of the spam campaigns currently circulating in the wild?
According to a newly released report by the University of California at San Diego, although hundreds of thousands of people visit the fraudulent pharmaceutical scam sites, only a small percentage of them is actually purchasing the counterfeit pharmaceutical items.
In this particular case, the United States leads with 72% of total purchases from fraudulent pharmaceutical sites.
More details:
Spamvertised ‘Google Pharmacy’ themed emails lead to pharmaceutical scams
Cybercriminals are currently spamvertising a Google-themed email campaign that’s enticing home and corporate PC users into clicking on bogus link leading to pharmaceutical scams.
More details:
Spamvertised ‘Your accountant license can be revoked’ emails lead to client-side exploits and malware
Cybercriminals are currently spamvertising a malicious email campaign that’s designed to trick you into clicking on a bogus complaint.pdf link which ultimately leads to client-side exploits and malware.
The campaign is launched by the same gang that launched the “Spamvertised ‘Termination of your CPA license’ ” malicious campaign last month.
More details:
Research: proper screening could have prevented 67% of abusive domain registrations
On a daily basis, spammers register thousands of new domains across multiple domain registrars, and take advantage of WHOIS privacy services to ensure that security researchers and anti-spam fighters will have hard time taking them down. So what can we do about it?
According to a newly released research by Knujon.com, proper screening could have prevented 67% of those abusive domain registrations.
More details:
A peek inside the Darkness (Optima) DDoS Bot
With politically motivated DDoS (distributed denial of service attack) attacks proliferating along with the overall increase in the supply of managed “DDoS for hire” services, it’s time to get back the basics, and find out just what makes an average DDoS bot used by cybercriminals successful.
Continuing the “A peek inside…” series, in this post I’ll profile the Darkness X (Optima) DDoS bot, available for purchase at selected cybercrime-friendly online communities since 2009.
More details:
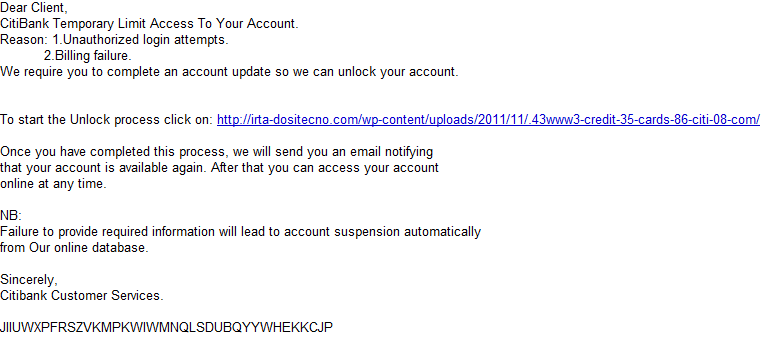
Spamvertised ‘Temporary Limit Access To Your Account’ emails lead to Citi phishing emails
Cybercriminals are currently spamvertising a fraudulent email campaign impersonating Citi, using ‘Temporary Limit Access To Your Account‘ themed emails as a social engineering attempt to trick end users into clicking on the link found in the phishing emails.
More details: