Korean Rogues’ Slapfight Bonanza
The other day, Threat Reseacher Dan Para sent along the video clip below, which gave us all a good laugh. Dan had been researching a Korean-language Trojan downloader, but when he ran the file, he didn’t expect the downloader to retrieve not one…not two…but three separate rogue antivirus products.
The most amusing thing about the video is that these three rogues — named Smartscan, Antiguard, and Bootcare — decided to duke it out amongst themselves to be front-and-center on the desktop. But each time one of the apps would bring itself to the front, both of the others would respond in what can only be generously described as a slap fight. The results were, well, you can see for yourself.
In addition to pushing one another out of the top position, each vied with the other to concoct outrageous numbers of detections on what was, ostensibly, a clean testbed system. Antiguard reported 215 items of concern, while Smartscan reported 225 “detections” and Bootcare reported 245. Like their English-only counterparts, these rogues require you to make a purchase to clean up these purported problems.
[vimeo 22264051]
Facebook-Spamming Worm Wants Your Eyeballs
(Update, July 11, 2011: On May 25, 2011, we were contacted by representatives of Future Ads, LLC, the parent company of both Playsushi and Gamevance. Future Ads informed us that they, too, had been victims of a scam perpetrated by rogue affiliates who seemed to be involved with the malicious campaigns we described in this post. Future Ads claims that it has taken action to prevent this type of abuse from happening in the future.)
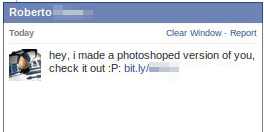 A worm that has been circulating on Facebook in the form of a Facebook application appears to have been engineered to drive traffic to a sleazy online advertising network which tries to connive people into installing software and disclosing a great deal of personal information about themselves in return for the promise of outrageously large gifts or prizes. As I write this, nearly 5 million people have fallen victim to this scam in just the past two days.
A worm that has been circulating on Facebook in the form of a Facebook application appears to have been engineered to drive traffic to a sleazy online advertising network which tries to connive people into installing software and disclosing a great deal of personal information about themselves in return for the promise of outrageously large gifts or prizes. As I write this, nearly 5 million people have fallen victim to this scam in just the past two days.
Last month, we published a report about a spam campaign designed to lure people into clicking a link to a bogus YouTube video. In that case, when you tried to play the video, your browser was instead redirected into an advertising network called CPALead. A convoluted series of steps eventually led victims to a page where they were prompted to fill out surveys (with outrageous promises for high-value gift cards or other valuable prizes) or download and install software from a Web site named Gamevance, which publishes online games and promises players cash prizes for high scores.
In this case, the campaign uses a clearly deceptive Facebook app — actually, dozens of duplicate apps with slightly different names — that (when you click the Accept button in Facebook) spams a shortlink to all of the victim’s contacts through Facebook’s chat mechanism. The spam messages all imply that the link leads to some sort of modified photo of the message recipient, but lead into a feedback loop which tries to spread itself further by infecting the Facebook accounts of new victims. Then it displays the ads.
Webroot Answers Your Security Questions
I’m very pleased to present today the first in a series of videos we’ve produced. The videos have the lofty goal of addressing the most pressing questions relating to malware, cybercrime, and online fraud. We’ll take you behind the scenes at Webroot and introduce you to some of our Threat Research team in the process.
In this first video, Webroot’s Director of Threat Research, Jeff Horne, answers a question submitted to us via Twitter direct message about the motives behind most cybercrime, and whether there are any examples of malware or other types of malicious online activity that have been motivated by anything other than financial gain.
[vimeo 21951624]
We’re planning to release a new video every other Monday from now on. When you’ve thought of that question you always wanted to know the answer to, tweet @webroot or send an email to blog (at) webroot.com, and we’ll answer the ones about cybercrime. We’ll try not to disappoint, but offer no promises. If you think of questions about something else, send them to Dr. Phil or Craig. We look forward to your letters!
Pinball Corp’s Appbundler Employs Malware-like Techniques
 For a couple of weeks now, I’ve been noticing a curious (and increasingly prevalent) phenomenon: Some of the free Web hosts popular among those who engage in phishing are popping new types of multimedia ads over the tops of the pages they host. Not only does the victim, in this case, risk having their login credentials to banks or social media sites phished, but many of those ads behave almost identically to “missing codec” social engineering scams that have been popular among malware distributors for years.
For a couple of weeks now, I’ve been noticing a curious (and increasingly prevalent) phenomenon: Some of the free Web hosts popular among those who engage in phishing are popping new types of multimedia ads over the tops of the pages they host. Not only does the victim, in this case, risk having their login credentials to banks or social media sites phished, but many of those ads behave almost identically to “missing codec” social engineering scams that have been popular among malware distributors for years.
The ads — and I use the term very loosely, because these contrivances fall well over the shady side of the ethical line for online advertisements — appear in banners or (in the multimedia-heavy version) glide down in front of the page the Web surfer happens to be browsing, annoyingly obscuring the page. In most cases, these “ads” take on the appearance of some sort of media player window that appears to be stuck in a “video loading” loop, but this is a ruse. There is no media player. The Flash animation is designed to look like one, with the goal to convince the viewer to click the fake video player window, which initiates the download of something called XvidSetup.exe from a server on the domain appbundler.net.
That domain, as well as appbundler.com and clickpotato.tv, appear to be owned by a company with a less than stellar online reputation called Pinball Corp. The executables are not malware, but they also don’t entirely do what they say they will, either. And while the programs also distribute an old, outdated version of the XviD codec (in addition to other sponsored apps, more about this below), they do so without the permission of the publisher of that software, and possibly in vi0lation of the GPL software license terms that XviD uses. A new term of art seems to be required to describe this type of advertising; I propose calling the ads scads, a concatenation of scam and ads. Scadware describes the fraudulent software more precisely than the prosaic Potentially Unwanted Application.
The deceptive way in which Pinball Corp’s ad convinces users to download and install the sponsored software certainly leaves a bad taste in my mouth. Read on for the details.
Shipping Confirmations Back on the Radar
![]() After a prolonged absence, waves of Trojans distributed as Zipped email attachments have been showing up in our spam traps for a few weeks. The spam messages employ the same hackneyed shipping confirmation pretext as many previous iterations of this scam. This technique’s emergence as a common malware distribution method correlates with the emergence of Trojan-Downloader-Tacticlol.
After a prolonged absence, waves of Trojans distributed as Zipped email attachments have been showing up in our spam traps for a few weeks. The spam messages employ the same hackneyed shipping confirmation pretext as many previous iterations of this scam. This technique’s emergence as a common malware distribution method correlates with the emergence of Trojan-Downloader-Tacticlol.
The messages claim to come from various express shippers, including DHL, UPS, and FedEx, as well as one that may have originated in a malware guy’s imagination: Post Express. And even though the distribution method mimics those used by Tacticlol, the payloads haven’t been limited to that Trojan. This time around, the files belong to a wider variety of malware, including not only several new variants of Tacticlol but also Trojan-Downloader-Karagany, Trojan-Relayer-Highport, and SpyEye.
The Trojans’ icons look like Office documents or Acrobat PDFs, which serve to further convince victims that the file isn’t dangerous. The email attachments — Zip files with names such as tracking.zip, Post_Express_Label.zip or DHL_tracking.zip — aren’t dangerous unless you open the attachment, extract the Trojan, and execute it. But once you do, you’re in for a world of trouble.
Spammed YouTube Comments Promote Adware – Successfully
(Update, July 11, 2011: On May 25, 2011, we were contacted by representatives of Future Ads, LLC, the parent company of both Playsushi and Gamevance. Future Ads informed us that they, too, had been victims of a scam perpetrated by rogue affiliates who seemed to be involved with the malicious campaigns we described in this post. Future Ads claims that it has taken action to prevent this type of abuse from happening in the future.)
By Curtis Fechner and Andrew Brandt
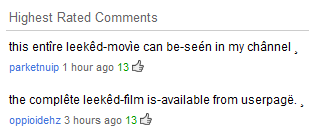 I was poking around at the end of the work day last week, checking out the newly-released trailer for X-Men: First Class. But something in the comments caught my eye: The two highest-rated commenters don’t appear to be human. Their messages invite readers (using some goofily accented characters) to visit a profile and see the whole movie.
I was poking around at the end of the work day last week, checking out the newly-released trailer for X-Men: First Class. But something in the comments caught my eye: The two highest-rated commenters don’t appear to be human. Their messages invite readers (using some goofily accented characters) to visit a profile and see the whole movie.
I’m sure the film’s director, Matthew Vaughn, would also love to see that, especially because he may not have finished shooting the movie yet. And, of course I wanted to see just how they’d manage to get “this entîre leekêd-movìe” or “the complête leekêd-film” in their user channel, given the absence of a completed film, let alone YouTube’s limits on video length.
When I click through to the profile, it suddenly makes sense. The profile links to an outside site where (the profile’s owner claims) you can watch the full movie. It only took 13 thumbs-up clicks on those comments to make those comments the most popular, but a real user isn’t going to ‘like’ glaringly obvious comment spam. The comments are probably being boosted by the spammers themselves. With just under 7 million page views, this is apparently an effective scam. Not good!
Shorty Worm Spams Links, Hijacks Browsers
![]() A novel worm we’re calling Worm-IM-Shorty appears to be winding its way through Facebook and some instant messaging services, with its come-on disguised as a link to a photograph hosted elsewhere. But when recipients click the link, they receive an executable Trojan instead, dressed up with the name and icon of a JPEG image.
A novel worm we’re calling Worm-IM-Shorty appears to be winding its way through Facebook and some instant messaging services, with its come-on disguised as a link to a photograph hosted elsewhere. But when recipients click the link, they receive an executable Trojan instead, dressed up with the name and icon of a JPEG image.
If one double-clicks the file, the Trojan turns the computer into an advertising cash cow for some enterprising malware distributor. The Trojan modifies the active browser’s home page setting to a malicious page on domredi.com, which in turn redirects the browser, at random, to one of several domains hosted on a server in The Netherlands. Each page the browser loads is filled with ads, and when you load an ad-filled page, someone likely gets paid. Follow the money, and you’ll find the perps.
read more…
New Bank Phisher Brings Added Functionality, Problems
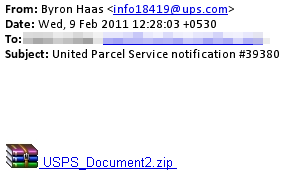 I didn’t want to let too much time pass before I wrote about a new Zbot-like bank phishing Trojan variant that came across my desk last week. The keylogger started arriving the first week of February as an attachment to a spam email designed to look like it came from United Parcel Service. No, the old malware trope of spammed shipping invoices is not dead yet, Alice, but we’re going to follow this one down the rabbit hole anyhow.
I didn’t want to let too much time pass before I wrote about a new Zbot-like bank phishing Trojan variant that came across my desk last week. The keylogger started arriving the first week of February as an attachment to a spam email designed to look like it came from United Parcel Service. No, the old malware trope of spammed shipping invoices is not dead yet, Alice, but we’re going to follow this one down the rabbit hole anyhow.
The brief message had a Subject line of “United Parcel Service notification” followed by a random, five-digit number, and a file named USPS_Document.zip attached to the message. Why spammers seem to confuse the US Postal Service with UPS eludes common sense, but I think it has been made abundantly clear by now that, by and large, the people who send these kinds of files around aren’t the sharpest tacks in the box. The HTML body of the message indicated that the .zip file contains a tracking number, but that’s just part of the ruse.
![]() The Trojan is readily identified by its appearance. It uses an old Adobe PDF document icon, but the programmers picked a version of that icon with an X drawn over the top. D’oh. The file also throws an error when run in a virtual machine that forces the VM to bluescreen, but that didn’t affect our ability to analyze the file. We could execute it and observe its behavior without a problem. This new Trojan installs services that remain memory resident after the installer has run, dropped its payloads in the Application Data folder, and deleted the original copy of itself.
The Trojan is readily identified by its appearance. It uses an old Adobe PDF document icon, but the programmers picked a version of that icon with an X drawn over the top. D’oh. The file also throws an error when run in a virtual machine that forces the VM to bluescreen, but that didn’t affect our ability to analyze the file. We could execute it and observe its behavior without a problem. This new Trojan installs services that remain memory resident after the installer has run, dropped its payloads in the Application Data folder, and deleted the original copy of itself.
Fishing for Phishers is a Full-Time Job
By Ian Moyse, EMEA Channel Director
 We seem to take phishing attacks for granted these days, in much the same way that we’ve accepted spam as a natural, and inevitable, by-product of email. Some experts believe that one of the best solutions to thwart phishing attacks is end-user training, but I doubt training alone can be a viable solution. Can we really train every computer user to be sufficiently security literate, such that anyone can distinguish a phishing message from a genuine bank email? I doubt that it is possible, especially given how specific the details in spear phishing (phishing targeted at specific people and/or companies) attacks have become.
We seem to take phishing attacks for granted these days, in much the same way that we’ve accepted spam as a natural, and inevitable, by-product of email. Some experts believe that one of the best solutions to thwart phishing attacks is end-user training, but I doubt training alone can be a viable solution. Can we really train every computer user to be sufficiently security literate, such that anyone can distinguish a phishing message from a genuine bank email? I doubt that it is possible, especially given how specific the details in spear phishing (phishing targeted at specific people and/or companies) attacks have become.
It used to be that thieves could satiate their hunger for evil (and money) merely through the emulation of a consumer bank or a PayPal login screen. While those low-hanging-fruit scams show no signs of abating, even following some major busts of phishing rings, we’ve seen new types of phishing attacks that wear the mask of a Web security product, persuading users to follow through on fake spam quarantine messages, or security update alerts, sometimes using the name of real vendors. It’s all very plausible.
Unfortunately, the average user is not a trained security expert—and why should he or she be? Criminals lure us into phishing and email scams in much the same way that street cons lure some people into losing their wallet at Three-card Monte. We let our curiosity get the best of us, and at times can be gullible. Like street hustlers, cybercriminals aren’t afraid to experiment with hacking our inclinations (or, as many security experts call it, social engineering). The volume of phishing attacks has increased, as have their variety and sophistication. Even security experts struggle to identify some of the fakes.
The phishers cast their rods farther and with more efficiency than ever before. They can easily download phishing site creation tools (yes they exist) and produce convincing messages and pages. Expecting an average PC user to beat these guys without any help is tantamount to pitting an average golfer against Tiger Woods (albeit a few years ago; no offense, Tiger). The criminal’s job is to create online scams that work, and the returns on their investments are huge. Why would we expect non-criminally-minded users to be more adept at spotting scams, than scammers are at reeling in the users?
Technology has to step up its game. We need to continue to make it harder and less lucrative for online scammers to do their “jobs.” That’s really the most effective way to stop phishers from attacking our end users.
Malicious PHP Scripts on the Rise
Last week, I gave a talk at the RSA Security Conference about malicious PHP scripts. For those who couldn’t attend the conference, I wanted to give you a glimpse into this world to which, until last year, I hadn’t paid much attention.
My normal week begins with a quick scan of malware lists — URLs that point to new samples — that come from a variety of public sources. I started noticing an increasing number of non-executable PHP and Perl scripts appearing on those lists and decided to dig a little deeper.
In a lot of ways, PHP is an ideal platform for malicious Web pages. For programmers and techies, PHP is easy to learn. Virtually all Web servers run the PHP engine, so there are vast numbers of potential “victims” (though the numbers aren’t anything close to the number of Windows-using potential malware victims). And just like many forms of executable malware that runs on Windows — the type I’m more familiar with — the most successful malicious PHP scripts permit their users (the criminals) to control and manipulate Web servers for their own benefit and, most commonly, profit.
read more…With Great Power Comes Great Responsibility
By Ian Moyse, EMEA Channel Director
 The cloud delivery model gives vendors a great amount of power. It is easier to create, deploy, maintain and enhance a service than it has been at any other point in computing history. Just look at Facebook, which grew to 500 million members in a very short period of time. People readily share within it, many with a limited understanding of the potential risks to their private information.
The cloud delivery model gives vendors a great amount of power. It is easier to create, deploy, maintain and enhance a service than it has been at any other point in computing history. Just look at Facebook, which grew to 500 million members in a very short period of time. People readily share within it, many with a limited understanding of the potential risks to their private information.
The ability to make an enhancement and almost instantly put it into the customer’s hands is immensely powerful – and immensely dangerous. If you’re a software vendor and distribute software with a bug, the effect propagates slowly as people install the update. And often, you’ll hear about the problem and get a chance to fix it before many customers even become aware. With cloud technology, however, such mistakes instantly propagate to all users. Because of this ability to quickly affect a wide range of customers, the responsibility for a cloud vendor is greater than we have seen before.
As the industry rushes to capitalize on the cloud delivery model, users are faced with more and more choices, making it harder to distinguish between a robust, reputable vendor and a small, possibly risky, player. Selecting a safe bet vendor is critical. Many are software vendors that are just dipping their toes into cloud technology. But the cloud is a very different world, and there is a different approach and mindset to deliver upon.
It is up to customers and resellers to perform due diligence on cloud vendors so they can deliver success stories to their customers and business associates. As in any market, there are pros and cons and good and bad providers. Customers and resellers need to take the time to make educated decisions to discern the good from the bad, the safe from the risky. And cloud vendors need to invest in the expertise and solutions required to deliver the high quality of service customers expect.
The benefits of cloud technology far outweigh the potential risks, both in terms of power and quality of service. Smaller businesses and individual consumers can now access robust applications that were previously affordable only by larger firms. The risks can be mitigated by performing educated decisions and being diligent in your choices. There are plenty of options, and it is up to you to select a vendor who can responsibly manage the power of the cloud.
A Cryptogram a Day Keeps the Malware Away
 As a child, one of my favorite daily pastimes was solving the cryptogram puzzle published in the LA Times (after my mom finished the crossword puzzle, of course). I used to plow through paperback word puzzle books obsessively, finishing them in days. Appropriately, a Trojan that popped onto my radar last week had me flexing my cryptogram muscles yet again.
As a child, one of my favorite daily pastimes was solving the cryptogram puzzle published in the LA Times (after my mom finished the crossword puzzle, of course). I used to plow through paperback word puzzle books obsessively, finishing them in days. Appropriately, a Trojan that popped onto my radar last week had me flexing my cryptogram muscles yet again.
The Trojan is a fairly common game password stealer, and it wouldn’t have merited a second look except that it also runs through a few routines to disable various antivirus products sold exclusively in Korea. Most game phishing Trojans we see originate in China and target gamers (and antivirus products sold) in China.
The application is designed to drop a copy of itself into the Windows directory, rename that copy canima.exe, then insert the appropriate registry keys to install itself as a service (with the implausible name “Nationaldddeew Instruments Domain Service” — hasn’t anyone told these game-snarfing saps about the uncanny valley?). It then sits around and wait for someone to enter credentials to log into any of at least seventeen online games popular in Korea, including Maple Story, Aion, WoW, and FIFA Online. The Trojan finally submits the stolen passwords to a Web site, but it doesn’t make that connection until it has something to upload. If you don’t have any games installed (as I don’t on my default testbed), the malware simply waits patiently until you install some.
So, I dumped the running file out of memory and took a look at whatever plain text strings were present. Sometimes you find domain names or other clues that reveal the origin of the attack (or the destination of any exfiltrated data). Several lines of text caught my eye, but they weren’t words, or even legible data. What was most apparent about these strings was that a large group of them began with a pattern that follows the paradigm 1223455 — the actual string in the file that caught my eye was s{{8HSS. If that pattern looks familiar, it should: The http:// prefix follows that same pattern.
























































