Maze Ransomware is Dead. Or is it?
“It’s definitely dead,” says Tyler Moffitt, security analyst at Carbonite + Webroot, OpenText companies. “At least,” he amends, “for now.”
Maze ransomware, which made our top 10 list for Nastiest Malware of 2020 (not to mention numerous headlines throughout the last year), was officially shut down in November of 2020. The ransomware group behind it issued a kind of press release, announcing the shutdown and that they had no partners or successors who would be taking up the mantle. But before that, Maze had been prolific and successful. In fact, shortly before the shutdown, Maze accounted for an estimated 12% of all successful ransomware attacks. So why did they shut down?
I sat down with Tyler to get his take on the scenario and find out whether Maze is well and truly gone.
Why do you think Maze was so successful?
Maze had a great business model. They were the group that popularized the breach leak/auction website. So, they didn’t just steal and encrypt your files like other ransomware; they threatened to expose the data for all to see or even sell it at auction.
Why was this shift so revolutionary?
The Maze group tended to target pretty huge organizations with 10,000 employees or more. Businesses that big are likely to have decent backups, so just taking the data and holding it for ransom isn’t much of an incentive.
Now think about this: those huge businesses also would’ve been subject to pricey fines for data breaches because of regulations like GDPR; and they’re also more likely to have big budgets to pay a ransom. So, instead of simply saying, “we have your data, pay up,” they said, “we have your data and if you don’t pay, we’ll expose it to the world – which includes the regulators and your customers.” Most of the time, paying the ransom is going to be the more cost effective (and less embarrassing) option. We don’t know if the Maze group invented this tactic, but they definitely set the trend, and a bunch of other ransomware groups started following it.
Other than the leak sites, did they do anything else noteworthy or different from other groups?
One of the bigger threat trends we saw in 2020 was malware groups partnering up for different pieces of the infection chain, such as Trojans, backdoors, droppers, etc. The botnet Emotet, for example, was responsible for a huge percentage of ransomware infections from various different groups. Maze, however, was pretty self-contained. We saw them working with a few other groups throughout 2020, but they had their own malspam campaign for delivery and everything else they needed in-house, so to speak. They were like a one-stop shop.
Do you think the move to remote work during the pandemic contributed to their success?
Absolutely, though you could say that about any ransomware group. Phishing and RDP attacks really ramped up when people started working from home. Home networks and personal devices are generally much less secure than corporate ones, and cybercriminals are always looking for ways to exploit a given situation for their gain.
If Maze was doing so well, why did they shut down?
Probably because they’d gotten too much attention. The more notoriety you get, the harder it is to operate. We see this with a lot of malware groups. They shut down for a while, either to lie low because the heat is on, or to just spend the money they’ve gotten from their payouts and enjoy life. Or, sometimes, they don’t lie low at all but just rebrand themselves under a new name. Either way, they tend to come back. For example, a ransomware variant called Ryuk went dark and came back as Conti. Emotet went away for a long time too and then came back under the same group name.
How can you tell when an old group has rebranded?
Unless they announce it in some way, the only way to really tell is if you can get a sample of the malware and reverse engineer it and look at the code. One of our threat researchers did that with a sample of Sodinokibi and discovered it had “GandCrab version 6” in its code. So, that’s an example of a rebrand, but it can be hard to spot.
Do you think Maze is done for good?
Not a chance. They attacked huge targets and got massive payouts. Most ransomware groups attack smaller businesses who are less likely to have strong enough security measures. Even the ones that targeted larger corporations, like Ryuk, still attacked businesses one-fifth the size of a typical Maze target. Now, the Maze group can relax and take a lavish vacation with all the money they got. But I’d be pretty shocked if they just abandoned such a winning business model entirely.
The verdict: Maze may be gone for now, but experts are fairly certain we haven’t seen the last of this virulent and highly successful malware group. In the meantime, Tyler advises businesses everywhere to use the lull as an opportunity to batten down their cyber resilience strategies by implementing layered security measures, locking down RDP, and educating employees on cybersecurity and risk avoidance.
Stay tuned for more ransomware developments right here on the Webroot blog.
How to Build Successful Security Awareness Training Programs in 2021 and Beyond
Security awareness training is one of the most straightforward ways to improve a business’ overall resilience against cyberattacks. That is, when you get it just right.
Thanks to the disruptions to “normal” work routines that COVID-19 has brought, launching a company-wide training program to teach end users how to avoid phishing scams and online risks is a big challenge. Unfortunately, COVID-19 has also brought a major acceleration in phishing activity. With so many office employees working outside the safety of corporate network protections, you can see why the need for training has never been more critical.
But there’s another issue: training is outside the skillset for most IT admins, and the level of effort to set up and run a program of training courses, compliance accreditations and phishing simulations can be daunting.
To help you get started, here are our top 5 recommendations for starting your security awareness program so you can maximize the impact of your efforts.
- Get buy-in from stakeholders.
While you probably already have some combination of security tools in place, such as endpoint protection, DNS or web filtering, etc., the 2020 Verizon Data Breach Investigations Report states that phishing and social engineering are still the primary tactics used in successful cybersecurity breaches.
Make sure your stakeholders understand these threats. Send an email introducing the program to management and clearly explain the importance of educating users and measuring and mitigating your risk of exposure to phishing and other social engineering attacks.
- Start with a baseline phishing campaign.
When you run your first phishing campaign, you establish your starting point for measuring and demonstrating improvement over time. (You can also use this real-world data to accurately show the need for improvement to any still-skeptical stakeholders.) Ideally this initial campaign should be sent to all users without any type of forewarning or formal announcement, including members of leadership teams. Make sure to use an option that simply shows a broken link to users who click through, instead of alerting them to the campaign, so you can prevent word-of-mouth between employees from skewing the results.
- Set up essential security and compliance training.
Create training campaigns to cover essential cybersecurity topics including phishing, social engineering, passwords and more. Establish which compliance courses are appropriate (or required) for your organization and which employees need to complete them.
- Establish a monthly phishing simulation and training cadence.
Repetition and relevance are key for a successful security awareness training program. By setting up a regular simulation and training schedule, you can more easily measure progress and keep an eye on any high-risk users who might need extra attention. Using our shorter 4-5-minute modules in between more substantial training is an effective tactic to keep security top of mind while avoiding user fatigue. And if you can’t run phishing simulations monthly, strive for a quarterly cadence. If you get pushback on sending emails to everyone, then we recommend you prioritize testing users who failed the previous round.
- Communicate results
A great way to raise awareness and increase the impact of your phishing campaigns is to share the results across the organization. Keep in mind, the goal is to capitalize on collective engagement and share aggregate results, not to call out individuals. (Your “offenders” will recognize themselves anyway.)
The critical piece is seeing the statistics on where the organization stands as a whole. After the baseline phishing simulation, send out an email to all employees with the results and the reasoning for the campaign. Communicating these numbers will not only help show improvement over time, it’ll also demonstrate the value of the program overall and reinforce to employees that cyber resilience isn’t just IT’s job – it’s a responsibility we all share.
Although there are numerous other tips and tricks that can help ensure the success of your security awareness training program, these are our top five basic pieces of advice to get you on your way. When you follow these steps, it won’t take long to see the very real returns on your training investment.
For more detailed tips on how you can put Webroot® Security Awareness Training to work to improve your business’ cyber resilience posture, view our white paper.
Cyber News Rundown: Trickbot Spreads Via Subway Emails
Trickbot spreading through Subway company emails
Customers of Subway U.K. have been receiving confirmation emails for recent orders that instead contain malicious links for initiating Trickbot malware downloads. Subway has since disclosed that it discovered unauthorized access to several of its servers, which then launched the campaign. Users who do click on the malicious link initiate a process in Task Manager that can be stopped to prevent additional illicit activities typical of Trickbot infections.
Scores of municipal websites attacked in Lithuania
At least 22 websites belonging to various municipalities in Lithuania were compromised after a sophisticated cyberattack allowed intruders to take control. After gaining access to the sites, the attackers began delivering misinformation emails under the auspices of Lithuanian government and military ministries. Much of the misinformation being spread revolved around military enlistment and the suspicion of corruption at an airport housing a NATO facility.
Researchers discover millions of medical records online
Researchers at CybelAngel have uncovered over 45 million healthcare records on unprotected servers. Amongst the sensitive data was personal health information and other personally identifiable data, all left on servers with a login page that allowed access without credentials. It’s likely this data was left unsecured because of the number of medical professionals needing to access, though the security lapse is inexcusable. With healthcare facilities prime targets for ransomware attacks, communications between organizations should entail strict security to protect the valuable data.
Ransomware strikes city of Independence, Missouri
Officials for the city of Independence, Missouri, have been working for weeks to recover from a ransomware attack that forced them to take several essential services offline. Fortunately, recent file backups were available to restore some of the encrypted systems to normal. At this point, officials remain uncertain if customer or employee data was stolen during the attack, and no ransomware group has come forward to take credit for the attack or post the stolen data for sale.
Data Breach Compromises Patient Data at California Hospital
California’s Sonoma Valley Hospital recently delivered letters to roughly 67,000 patients regarding a data breach back in October that may have compromised personally identifiable information and other healthcare records. While the hospital was able to shut down some of their systems to prevent the breach from spreading, the attackers are believed to have gained access to and stole sensitive data.
Remote Work is Here to Stay, and Other Cybersecurity Predictions for 2021
The cybersecurity industry and end-of-year predictions go together like Fall and football or champagne and the New Year. But on the heels of an unprecedented year, where a viral outbreak changed the landscape of the global workforce practically overnight, portending what’s in store for the year ahead is even trickier than usual.
One thing the cybersecurity experts at Webroot agree on is that work from home is here to stay for 2021, or at least it won’t recede to pre-pandemic levels in even the medium-term. What is likely to change is how companies respond to their remote workforces. The security measures they take (or don’t), the educational opportunities they provide (or fail to) and their commitment to innovation (or lack thereof) will likely separate the winners from the losers in the year ahead.
Yes, cybersecurity for remote workforces will likely be a prevailing concern throughout 2021, even following positive news on the vaccine development front, according to Webroot experts. Another prevailing theme from the professionals here, when asked to make their annual predictions for the new year, is that a cybersecurity skills gap will continue to haunt businesses and pose opportunities for those looking to start their careers in the field or make the switch to it. As such, automation and the adoption of AI technologies will be critical to plugging the gap.
Read on for more details from leading engineers, security analysts and product specialists from around our organization for complete cybersecurity predictions for 2021. Take heart because, whatever happens, 2020 won’t be easily outdone (knock on wood).
On remote workforces and the problem of personal devices
David Dufour, VP of engineering, Carbonite + Webroot
In 2021, many businesses will continue to operate remotely as a result of the pandemic and there must be an emphasis on training employees on security best practices, how to identify modern threats such as phishing, and where company data is being accessed and stored. Phishing is going to remain one of the most prominent ways to attack users and will become more sophisticated as it’s tailored to take advantage of work-from-home setups and distractions.
Grayson Milbourne, security intelligence director, Carbonite + Webroot
The biggest change for 2021 will be securing remote workforces and remote perimeters, which include home networks and home devices, particularly personal devices. These all add their own challenges. Home networks and their configurations are diverse. Many use out-of-date routers with insecure settings. Personal devices are often used for work and, as we saw in our 2020 Threat Report, are twice as likely as business devices to encounter infections. If not addressed, this could have a serious impact on businesses in the coming year.
Hal Lonas, CTO and SVP of SMB engineering, Carbonite + Webroot
We shouldn’t overlook the incredible societal and behavioral changes underway right now. These put all of us in new situations we’ve never encountered before. These new contexts create new opportunities for social engineering attacks like phishing and scare tactics to get us to open emails and click on fraudulent links.
Tyler Moffitt, Sr. security analyst, Carbonite + Webroot
It really doesn’t matter the company or the length of the work-from-home stint, one thing that’s constant is that professionals at home are using their personal devices and personal network. Securing the remote perimeter is going to be the biggest challenge for cybersecurity professionals now through 2021 because laptops issued to professional workforce are much more secure than personal devices.
Personal devices are twice as likely to be infected than business devices. Even more worrying, we saw with our new COVID-19 report that one-third of Americans will use personal devices when working from home. Businesses will need to account for that.
Jamie Zajac, VP of product management, Carbonite + Webroot
I predict that in 2021 vulnerable industries like hospitality, travel and retail will start to use even more remote access platforms like Square and others. This transfers a lot of control to a third-party, so it’s essential companies make sure their data is protected on their end, that their vendors are trustworthy and that their reputation is safe from the damage an internal breach could cause
On the cybersecurity skills shortage
Briana Butler, engineering services manager, Carbonite + Webroot
Moving forward, cybersecurity professionals will need greater data analysis skills to be able to look at large sets of data and synthesize the information so organizations can derive actionable value from it. In 2021, organizations need to start implementing programs to upskill their current cybersecurity workforce to focus on the skills they’ll need for the future such as analyzing complex data, developing algorithms, and understanding machine learning techniques.
David Dufour, VP of engineering, Carbonite + Webroot
The cyber skills gap will continue to be an issue in 2021 because companies continue to believe they understand cybersecurity and, as a result, tend to spend less on external cybersecurity resources. This leads to a feeling of false security and, unfortunately, inadequate security.
Cybersecurity requires a financial investment to truly meet an organizations’ needs and to enact processes for securing systems. It’s much more effective to invest in a few, solid security processes and to address gaps at the outset than it is to implement an inexpensive, broad security solution that falls short in key areas.
Hal Lonas, CTO and SVP of SMB engineering, Carbonite + Webroot
The pandemic has also changed the game for managed service providers (MSPs). They’re used to running a thin-margin business, but this has become even more difficult as their small business customers struggle. MSPs are fortunately heavily automated, but now they are under increasing pressure to deliver more with less. MSPs more than ever need automated solutions that make it easy for them to manage, secure and restore customers when incidents do occur. Some of that automation will come from AI, but auto-remediation, backup and restore capabilities are also important.
Looking ahead to 2021
Whatever 2021 is, at least 2020 will be over, right? But in all seriousness, the virus does not respect our calendar transitions and its implications will certainly bleed over into the New Year. Much has been made of a supposed “new normal,” but to truly arrive there, companies must account for the new realities of pervasive remote work and an exacerbated cybersecurity skills shortage.
If there’s one takeaway from our experts’ predictions for 2021, it’s that.
Staying a Step Ahead of the Hack
Hackers, never at a loss for creative deception, have engineered new tactics for exploiting the weakest links in the cybersecurity chain: ourselves! Social engineering and business email compromise (BEC) are two related cyberattack vectors that rely on human error to bypass the technology defenses businesses deploy to deter malware.
Social Engineering
Social Engineering is when hackers impersonate trusted associates or acquaintances to manipulate people into giving up their passwords, banking information, date of birth or anything else that could be used for identity theft. As it turns out, it’s easier to hack our trust than our computers. Social engineering covers a range of tactics:
- Email from a friend or family member – A hacker gets access to the email password of someone you know. From there, they can send you a malicious link in an email that you’re more likely to click on because it came from someone you trust.
- Compelling story (pretexting) – This includes urgently asking for help. This can read like, “Your friend is in danger and they need your help immediately – please send me money right away so they can get treatment!”
- Standard phishing tactics – Phishing techniques include website spoofing emails appearing to come from an official source asking you to reset your password or confirm personal data. After clicking the link and entering the info, your security is compromised.
- “You’re a winner” notifications – Whether a lottery prize or a free trip to Cancun, this tactic catches many off guard. It’s known as “greed phishing” and it takes advantage our fondness for pleasure or weakness for the word “free.”
Business Email Compromise
Business email compromise is a targeted attack against corporate personnel, usually someone with the authority to request or fulfill a financial transaction. Victims execute seemingly routine wire transfers to criminals impersonating legitimate business associates or vendors.
This form of fraud relies on a contrived pretext to request a payment or purchase be made on the attacker’s behalf. According to the FBI, BEC attacks resulted in more than $26 billion (you read that right) between June 2016 and July 2019. Here are a few tips for protecting users and businesses from BEC attacks:
Slow down – BEC attacks combine context and familiarity (an email from your boss) with a sense of urgency (I need this done now!). This causes victims to lose their critical thinking capabilities.
Don’t trust, verify – Never use the same channel, in this case email, to verify the identity of the requester. Pick up the phone and call, or use video chat.
Prepare for the inevitable – Use all the technology at your disposal to ensure a BEC attack doesn’t succeed. Machine learning-enabled endpoint security solutions can help identify malicious sites.
Address the weakest link – Train users to spot BEC attacks. Webroot testing shows that phishing simulations can improve users’ abilities to spot attacks.
Perfecting Your Posture
Webroot Security Intelligence Director, Grayson Milbourne, offers several suggestions that companies can do to increase their security posture. First, he says, “Whenever money is going to be sent somewhere, you should have a two-factor verification process to ensure you’re sending the money to the right person and the right accounts.”
Milbourne is also a big advocate of security awareness training. “You can really understand the security topology of your business with respect to your users’ risk factors,” he says. “So, the engineering team might score one way and the IT department might score another way. This gives you better visibility into which groups within your company are more susceptible to clicking on links in emails that they shouldn’t be clicking.”
With the increase in scams related to the global COVID-19 pandemic, timely and relevant user education is especially critical. “COVID obviously has been a hot topic so far this year, and in the last quarter we added close to 20 new templates from different COVID-related scams we see out in the wild,” Milbourne says.
“When we look at first-time deployment of security awareness training, north of 40% of people are clicking on links,” Milbourne says. “Then, after going through security awareness training a couple of times, we see that number dip below 10%.”
Where to learn more
Our newest research on phishing attacks and user (over)confidence, “COVID-19 Clicks: How Phishing Capitalized on a Global Crisis” is out now, check it out!
Cyber News Rundown: Global Cybercrime Costs Surpass $1 Trillion
Cybercrime surpasses $1Trillion in global costs
A recent study has put the global cost of cybercrime at over $1 trillion for 2020. This figure is up significantly from 2018, which was calculated at around $600 billion. And while most effects are financial, roughly 92% of affected organizations cited by the study reported additional issues stemming from cyberattacks. Over half took no measures to prevent or recover from common types of attack.
Major hosting provider affected by cyberattack
The worldwide hosting service provider Netgain was forced to take many of its servers and data centers offline following a recent ransomware incident. The attack occurred just before Thanksgiving and continues to cause intermittent outages for customers as the company works to restore their systems. Due to the volume of systems Netgain provides services for, they remain unsure how long customers will be inconvenienced by the fallout from this attack.
Default passwords compromising radiology equipment
Researchers have discovered that GE has implemented default passwords that can be easily found online across a wide range of medical equipment. These passwords, used by technicians to perform routine maintenance, could also be used illicitly to take control of the machines or cause them to malfunction. Users are unable to change these credentials on their own and require a certified GE tech to come to make on-site adjustments. While GE has stated it does not believe any unauthorized access has been identified, the critical nature of these machines makes this a high priority vulnerability.
Educational technology still lacking proper security
An alarming number of schools and educational institutions switching to remote learning have made no changes to their security policies or implemented any cybersecurity training for staff and/or students. Additionally, nearly 40 percent of the schools surveyed weren’t even able to provide devices for their employees or students to work remotely during the pandemic, though 70 percent had switched their regular communications to video conferencing services.
Payment card skimmers hiding in CSS
Camouflaging payment card skimmers into the CSS of compromised e-commerce site is the latest evasion tactic being used by cybercriminals. The skimmer is run by the Magecart group, which is known for successfully evading detection software and innovating to boost longevity on compromised systems. The embedded script launches during the checkout process by redirecting the customer to a new page where it begins stealing information entered into a form.
Cyber News Rundown: Biological Worries Over Malware Attacks
Biological Worries Over Malware Attacks
Researchers have recently unveiled the latest potential victim for malware authors: biological laboratories. By illicitly accessing these facilities, hackers may be able to digitally replace sections of DNA strings, causing unexpected results when biologists go to create or experiment with these compounds. While it is fortunate that this specific targeted attack was simulated in a closed environment, it brought to light the extreme focus that a cyber-attack may be capable of implementing, and the lengths some attackers may go to accomplish their goal.
SMS App Exposes Messages of Millions
Despite the weeks of effort from the developer, GO SMS Pro an instant messaging app with over 100 million users is still suffering from messages being leaked. What originated as a bug has left the messaging app critically flawed for upwards of three months, with no clear signs of resolution, as even new versions of the app have been unable to rectify the problem. The researchers who discovered the flaw were able to view video and picture messages, along with other private messages, due to the URL shortening that occurs when the messages are sent to contacts that don’t have the app installed.
Colorado Health Service Provider Suffers Patient Data Breach
Sometime during the middle of September, the Colorado-based health service provider AspenPointe suffered a data breach that may have compromised the sensitive health information of nearly 300,000 patients. The facility noticed the unauthorized access over a two-week period, but only began notifying patients of the breach in the third week of November. Officials have also confirmed that everything from names to medical history, and other highly sensitive personal information was stolen, though no reports of misuse have yet arisen.
Ransomware Shuts Down Alabama School District
The Huntsville City school district, one of the largest in Alabama, has been forced to close all operations following a ransomware attack that took place as students and staff were returning from Thanksgiving break. District officials worked quickly to take all devices offline, be them computers or smart phones, to stop the spread of the attack. Students were also sent home early, with no firm statement on when classes would resume, as the attack could take them days or weeks to recover from.
Five Arrested in Louisiana Child Crime Sweep
At least 5 individuals have been arrested by the Louisiana Cyber Crime Unit, following an investigation into the online exploitation of children. By tracing IP addresses and even simply viewing social media profiles of all 5 individuals, law enforcement agents have been able to confirm charges of possession or creation of child pornography, thus removing another group of child predators from the general population.
Why Workers Aren’t Confident in their Companies’ Security (and What to Do About it)
According to data from a recent report, only 60% of office workers worldwide believe their company is resilient against cyberattacks. Nearly one in four (23%) admit to not knowing, while nearly one in five (18%) flat-out think it isn’t.
In the anonymous, write-in responses to the survey, many workers agreed that their employers could be doing more to support them and ensure their security. When asked to elaborate on why they didn’t believe their company was resilient against attacks, the most-repeated answers were along the following lines:
- My company has been hacked before.
- My company doesn’t prioritize security/security spend.
- My company’s equipment and software are poorly maintained.
- My company outsources its security, so we have no direct control.
- I still get phishing emails. Our filtering must not be good enough.
These types of responses highlight two things: a general lack of faith in the company’s security and the perception that companies aren’t investing enough in security systems OR their employees. When considered alongside another question from the survey, there seems to be a third factor at play: there is also confusion as to who should be responsible for a company’s cyber resilience in the first place.
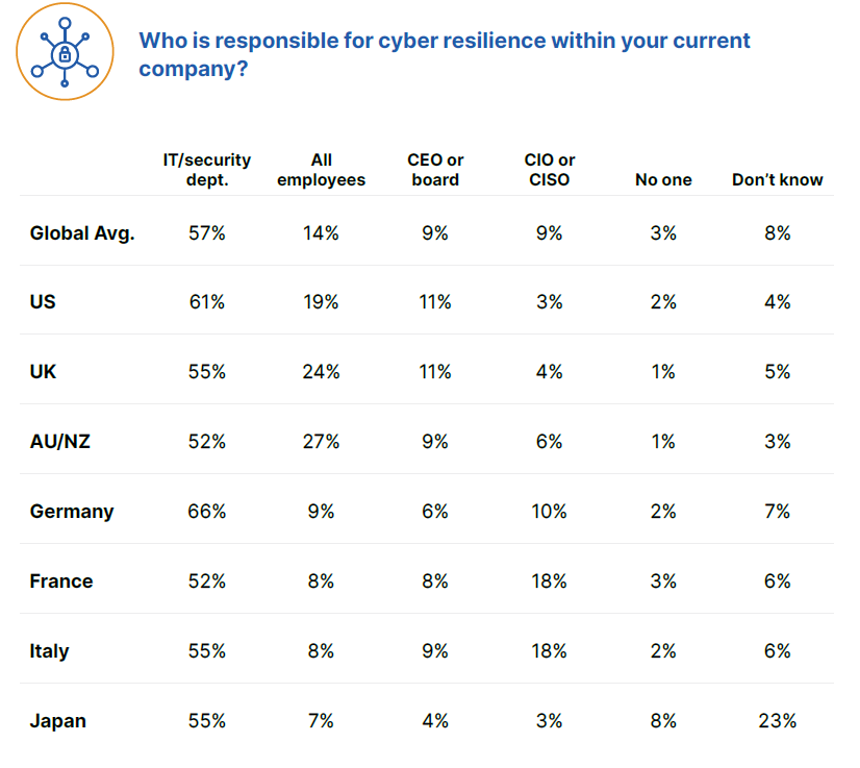
Overall, only 14% of office workers worldwide consider cyber resilience to be a responsibility all employees share. If workers also feel their companies don’t invest enough in them or the tools that protect them, it makes sense that they might not feel like cyber resilience is something they should worry about. If a person feels their employer doesn’t value them appropriately or empower them with the right tools to do their jobs, then the notion of having to expend one’s own time and energy on the company’s security could rankle. So how do you overcome the challenge of personal investment?
How to empower your people and your security
Investment
Dr. Prashanth Rajivan, cybersecurity and human behavior expert, says businesses that want to foster a feeling of personal investment must first tackle the notion of shared responsibility. He explains that, when people perceive themselves to have a greater responsibility to others, their average level of willingness to engage in risky behavior decreases.
“If you’re asking individuals to make changes to their own behavior for the greater safety of all, then you need to make it clear that you are willing to invest in them. By creating a feeling of personal investment in the individuals who make up a company, you encourage the employees to return that feeling of investment toward their workplace. That’s a huge part of ensuring that cybersecurity is part of the culture.” – Prashanth Rajivan, Ph.D.
One way to both empower your workforce to become a strong first line of defense while also demonstrating investment is by implementing a security awareness training program with phishing simulations, as well as giving employees enough time to carefully and thoughtfully complete the learning exercises and understand any applicable feedback.
Consistency
According to Phil Karcher, principal product manager in charge of Webroot® Security Awareness Training, running regular, up-to-date training on an ongoing basis is one of the best ways to help end users avoid attacks and become a strong first line of defense for the company as a whole.
“Data from Webroot® Security Awareness Training shows that, if you want people to make lasting changes to their behavior, you have to run consistent, relevant training courses and phishing simulations that are also varied enough that people won’t get bored or find them predictable. Running a second simulation makes a dramatic impact — and it only gets better from there.”
– Philipp Karcher, principal product manager, Carbonite + Webroot, OpenText Companies
| Number of Phishing Simulations | Click-through Rate |
| 1 | 11% |
| 2-3 | 8% |
| 4-10 | 6% |
| 11-14 | 5% |
| 15-17 | 4% |
Feedback
Dr. Rajivan also reminds us that human behavior is shaped by experience and reinforcement. He and Phil agree that consistency is key for empowering your workforce to become more resilient. But Dr. Rajivan also stresses the importance of feedback over consequences.
“Without appropriate feedback, no amount of training will be effective. And because the average person handles uncertainty poorly, training must include a variety of different scenarios. Human behavior is shaped through varied experiences, with a mix of positive and negative outcomes and applicable feedback.
– Prashanth Rajivan, Ph.D.
This feedback and incentive structure needs to be carefully calibrated. Too much could lead to heightened anxiety and false alarms, but too little could lead to underweighted risk, i.e. people knowing the correct actions, but not taking them.”
Next steps
As phishing attacks continue to be a primary way that businesses get breached, the need for consistent end user education is clear. And by implementing a regular training regimen, you can demonstrate care and investment in your people, educate employees on scams, risks and what to do if the unthinkable happens, and successfully build cyber resilience into your overall company culture.
To take the first step towards cyber resilience and trial an engaging Security Awareness Training program, Take a Free Trial.
Small Businesses are Counting on Their MSPs this Small Business Saturday
This November 28 may be the most important Small Business Saturday since the occasion was founded by American Express in 2010.
As early as July, nearly half (43 percent) of small businesses had closed at least temporarily, according to a study published in the Proceedings of the National Academy of Sciences. Research also suggests that 30 percent of small businesses expect to exhaust their cash on hand before year’s end. Eighty-eight percent have already spent the funds allocated to them by the U.S. government’s Paycheck Protection Program loan.
While hopes will be buoyed for some by recent positive developments in the search for a vaccine, uncertainty and hard times no doubt still lie ahead. That’s why Webroot encourages advocates and partners to shop small this November 28. For our customers, we aim to be a source of support and sound consultation as we recover together.
Challenges and opportunities for small businesses and MSPs
Many of the small businesses affected by COVID-19 are among Webroot’s clientele. Many more, especially managed service providers, count small businesses as their most important customers. We’ve heard from many who are suffering from lost contracts following office closures, fewer onsite projects, disappearing budgets for business development projects and a general slowdown of new business.
Others are witnessing a shift in the work they do and the services most in-demand. For some, COVID-related challenges have presented opportunities to step up and offer services made necessary by new realities. Unsurprisingly, the already trending adoption of cloud infrastructure has quickened its pace in the age of remote work.
“We’ve had to speed up migrating some clients on-premise file servers to online cloud solutions,” according to Russell Harris, a support engineer and project manager at Maya Solutions Ltd., a UK-based MSP specializing in Apple product support
For David Yates, president of Geeks R Us, a West Coast provider of various technical services, the shift to remote work was the push some of his customers needed to leave physical servers behind.
“A few clients who were reluctant to move to the cloud have now embraced it. This was the impetus that they needed to finally migrate away from on-premise servers,” he said.
Many MSPs have also taken it upon themselves to guide their clients through the transition to remote work, especially in terms of security.
“We’ve had to shift to more cloud, VPN and helping our clients work remotely,” says Nathan Hardester, a telecoms administrator with Whidbey Tech Solutions, a Washington-based MSP.
Cybersecurity education is another opportunity for MSPs looking to help small business clients up their cyber resilience. We know that many office workers are overly confident in their ability to detect a phishing attack, so MSPs should position themselves as educators. Already, in the COVID-era, some are finding themselves do exactly that.
Asked what’s changed at Maya Solutions since the pandemic, Harris responds “needing to provide additional training on online safety due to many working from home on their own devices.”
Making it through together
Many MSPs—often small businesses themselves—rely on their small business clients run for their success. And on this Small Business Saturday, small businesses need us all more than ever. Despite the challenges, there are opportunities for MSPs to step up and guide their clients through the changing way we work.
For more tips on staying cyber resilient through COVID-19 and beyond, stay tuned to our Community threat and check out these tips for MSPs looking to help small businesses bounce back.
Cyber News Rundown: REvil Ransomware Strikes
REvil Ransomware Strikes Hosting Provider
In recent days the web hosting provider Managed.com has been working to recover from a ransomware attack targeting many of their core systems. While the company was able to stop the spread of the attack by shutting down their systems and client websites, it remains unclear what information may have been encrypted and sent elsewhere. The demanded ransom is equal to $500,000 in Monero cryptocurrency and is set to double if not paid in the next week.
Cyberattack Shuts Down Americold Operations
Cold storage provider Americold revealed this week it was forced to shut down many of its systems after discovering evidence of a cyberattack. Some variant of ransomware is thought to be responsible for the attack, which has disabled several customer-facing services and could still be affecting Americold. Fortunately, the company responded quickly and was able to stop the attack from spreading across its network, which could have caused significantly more damage, especially if financial information was accessed.
Ticketmaster Receives Fine for 2018 Data Breach
More than two years after Ticketmaster announced a data breach had compromised a significant amount of customer information, the Information Commissioner’s Office (ICO) has settled on a fine of £1.25 million. The attack was significant because, while multiple organizations warned Ticketmaster of the breach, the company did nothing to resolve the security lapse. Officials also discovered that upwards of 60,000 customer payment cards were used for additional fraudulent activity after the Ticketmaster breach.
Healthcare Remains Easiest Target for Cyberattacks
A recent survey of healthcare organizations found that 73% had computer systems totally unprepared to repel a cyberattack. Attackers are improving their operations rapidly compared to security improvements being implemented by these organizations, even with the increasing year-over-year cybersecurity spending. To make matters worse, pressure put on the healthcare industry by the COVID-19 pandemic has forced many facilities to put security improvements on hold as they deal with increased patient numbers.
Severity of Capcom Breach Continues to Rise
A ransomware attack on Capcom that was initially suspected to not affect customer data has been found to be more severe than first thought. Upwards of 135,000 customers, employees and other individuals with ties to the company may have had sensitive personal information compromised. While Capcom has confirmed that payment data is processed through a third-party and isn’t stored on their systems, internal documents and statements seem to have been compromised by the attack.
6 Tips for a More Cyber-Secure Holiday Season
In any other year, many of us would be gearing up for airline travel, big family dinners, cocktail hours or potlucks with friends, and much more. But with all the challenges this year has brought in terms of how we work and connect during a global pandemic, I’m guessing all our plans look a little different than we thought they would.
Since most of us are now online more than ever before for work, school, personal connection, shopping, etc., it’s critical that take extra steps to keep our digital selves safe. With that in mind, we’ve put together a list of 6 (ish) tips to help you and your family stay safe online this holiday season, no matter how or where you celebrate it.
1. Watch out for an increase in scam emails and websites
What follows are just a few of the ways scammers may target you this holiday season. We recommend you install easy-to-use tools such as Fakespot, which is an add-on that protects consumers by detecting fraudulent product reviews and third-party sellers in real time, to help you avoid the fakes.
- Flash sale alerts
During the holidays, the number of promotional emails you receive is likely to go up as online stores run flash sales. With that in mind, scammers are likely to up their game, mimicking legitimate offer emails and websites in the hopes that your desire for a sweet deal will pay out for them. Use extra caution and don’t click anything in an offer email. Go to the retailer’s official website (type it directly into your browser instead of clicking a link in an email) to help ensure you’re shopping securely. - “Free” gift cards
You may get offers for “free” gift cards to online retailers, such as Amazon, Walmart or Target. Remember: very little in life is free. This is another way that criminals may try to trick you into downloading malware or exposing sensitive information that they can use to steal your money or identity. - Fake “missed delivery” notices
Since 94% of people are shopping online more or about the same as they were pre-pandemic, fake package notifications are another way that cybercriminals may target you. If you receive an email or text message about a missed delivery, be sure to double-check the details, such as the shipper (for example, maybe you’re only expecting a Prime or USPS delivery, so a FedEx notification should throw a red flag), the tracking numbers, etc. And, of course, don’t click or download anything in the text or email message itself - Discounts so deep they can’t be real
If you see an ad or email for a high-ticket item that suddenly costs less than 10% of the regular retail price, it’s practically guaranteed to be 100% fake. Let’s face it: there’s just no way you’re going to get real Ray-Bans for the low, low price of $24.99.
2. Use caution with your charitable donations
It’s the giving season and, thanks to the pandemic, natural disasters, and other current events, there are plenty of people in the world who could use a little extra help. Good on you for contributing to the public good! Unfortunately, not even charities are sacred to scammers, and they will take advantage of your desire to help others.
It’s critical to do your research! We recommend you visit trusted organizations, like Charity Watch, to learn more about the charities you’ve chosen and their efficiency, governance and accountability before committing money. Additionally, be suspicious of aggressive pitches including multiple calls and emails or tactics that require immediate donation. Lastly, never pay by gift card of wire transfer. Use a credit card instead, as it’s easier to track and recover fraudulent transactions.
3. Research your smart devices
When we say “smart devices,” we don’t just mean things like Alexa or Google Home. There are internet-enabled fridges that tell you when you’re low on groceries, let you hear and speak to someone at your front door, function as a baby monitor, and even tell you when your laundry’s done. There are also smart thermostats, garage door openers, light fixtures, and so much more. All of these gadgets form a network of connected devices known as the Internet of Things (IoT). And each one could potentially let a hacker into your home network.
Be selective when it comes to purchasing connected smart home and IoT devices. Choose reputable brands that include security, such as the ability to change passwords and perform firmware updates. Cheaper knockoffs of name brand devices might be easier on your wallet, but they are often designed without security in mind. Additionally, since the business model for knockoffs is typically to turn a profit as quickly as possible, there’s no guarantee the device manufacturer will even be around in a year or two to send out security updates or offer support if your device malfunctions
4. Secure any new tech toys right away
Get a cool new gadget in the family gift swap? (Or buy something awesome just for yourself? Don’t worry, we won’t tell the kids.) Protect that tech investment by installing security right away. It’s not the most exciting thing to do with a new toy, but it’ll help make sure you get to enjoy it without worrying about malicious actors joining in on the fun
5. Use reputable video chatting services to connect with loved ones
When planning your virtual holiday get-togethers, use trusted video conferencing providers like Zoom, who have paid close attention to security issues this year and adapted product defaults to enable safer user experiences. Also, be cautious of any websites that request permissions from your browser to access your camera and microphone. If you get one of these notifications, close out of your browser. Do not engage with the permissions request in any way
6. Remember the basics
We’ve said it before, we’ll say it again. Good online habits are your best defense – and it really doesn’t take much effort to keep yourself and your family safe
- Use strong, unique passwords for all your accounts and don’t share them. Length is strength, so passphrases are a good help.
- Install virus protection on all your devices and keep it up to date.
- Use a secure cloud backup.
- Connect to the internet using a VPN, even on your home network (and especially if transmitting sensitive info, like credit card numbers or online banking details.)
- Keep your device operating systems up to date so you have the latest patches against exploits.
- Don’t enable macros. Ever. If a document or website asks you to enable macros or hidden content or “allow access”, just don’t do it. There are very few legitimate reasons for documents or websites to request these permissions.
- Keep a close eye on your financial accounts and look out for any fraudulent activity.
Here’s wishing you a safe and cyber-secure holiday season! Keep an eye on the Webroot Blog and the Webroot Community for more tips and news on the latest cyber threats.
What’s the deal with security product testing anyway?
It’s common for savvy online shoppers to check third-party reviews before making an online purchasing decision. That’s smart, but testing the efficacy of security software can be a bit more difficult than determining if a restaurant had decent service or if clothing brand’s products are true to size.
So, with the arguably more significant consequences of antimalware testing, how can shoppers be sure that the product they choose is up to the task of protecting their family from malware? Which reviews are worthy of trust and which are just fluff?
Red flags in antimalware testing
Grayson Milbourne is the security intelligence director at Webroot and actively involved in improving the fairness and reliability of antimalware testing. While acknowledging that determining the trustworthiness of any single test is difficult, some factors should sound alarm bells when looking to honestly evaluate antimalware products.
These include:
The pay-to-perform model
In any test, the humans behind the product being evaluated have a vested interest in the performance. How far they go to influence those results, however, varies. One extreme way to positively influence results is to fund a test designed for your product to succeed. Often, the platform on which a test appears can be a sign of whether this is the case.
“YouTube tests are almost always commissioned,” warns Milbourne. “So, if you see things on YouTube, know that there is almost always someone paying for the test who’s working the way the test comes out. I try to avoid those.”
If only one product aces a test, that’s another sign that it may have been designed unfairly, maybe with the undisputed winner’s strengths in mind.
Every vendor acing a test
Tests in which all participants receive high scores can be useless in evaluating product efficacy. Because we know catching malware is difficult, and no single product is capable of doing it effectively 100 percent of the time, tests where every product excels are cause for concern.
“If every product aces the test, maybe that test is a little too easy,” says Milbourne. No product is perfect, so be wary of results that suggest so.
Failing to test in “the big picture”
No one piece of software can stop all the threats a user may face all of the time. But many vendors layer their preventative technologies—like network, endpoint and user-level protection—to most effectively protect against cyberthreats.
“Testers are still very worried about what happens when you encounter a specific piece of malware,” says Milbourne. “But there’s a lot of technology focused on preventing that encounter, and reactive technology that can limit what malware can do, if it’s still unknown, to prevent a compromise.”
In addition to how well a product protects an endpoint from malware, it’s also important to test preventative layers of protection which is lacking in 3rd party testing today.
The problem with the antimalware testing ecosystem
For Milbourne, the fact that so few organizations dedicated to efficacy testing exist, while the number of vendors continues to grow, is problematic.
“There are about five well-established third-party testers and another five emerging players,” he says. But there are well over a hundred endpoint security players and that number is growing.”
These lopsided numbers can mean that innovation in testing is unable to keep up with both innovation in security products as well as the everchanging tactics used by hackers and malware authors to distribute their threats. Testing organizations are simply unable to match the realities of actual conditions “out in the wild.”
“When security testing was first being developed in the early 2000s, many of the security products were almost identical to one another,” says Milbourne. “So, testers were able to create and define a methodology that fit almost every product. But today, products are very different from each other in terms of the strategies they take to protect endpoints, so it’s more difficult to create a single methodology for testing every endpoint product.”
Maintaining relationships in such a small circle was also problematic. Personal relationships could easily be endangered by a bad test score, and a shortage of talent meant that vendors and testers could bounce between these different “sides of the aisle” with some frequency.
Recognizing this problem in 2008, antimalware vendors and testing companies came together to create an organization dedicated to standardizing testing criteria, so no vendor is taken off guard by the performance metrics tested.
The Anti-Malware Testing Standards Organization (AMTSO) describes itself as “an international non-profit association that focuses on addressing the global need for improvement in the objectivity, quality and relevance of anti-malware testing methodologies.”
Today, its members include a number of antivirus and endpoint security vendors and testers, normally in competition against one another, but here collaborating in the interest of developing more transparent and reliable testing standards to further the fair evaluation of security products.
“Basically, the organization was founded to answer questions about how you test a product fairly,” says Milbourne.
Cutting through the antimalware testing hype
Reputation within the industry may be the single most important determinant of a performance test’s trustworthiness. The AMTSO, which has been working towards its mission for more than a decade now, is a prime example. Its members include some of the most trusted names in internet security and its board of directors and advisory board are made up of seasoned industry professionals who have spent entire careers building their reputations.
While none of this is to say there can’t be new and innovative testing organizations hitting the scene, there’s simply no substitute for paying dues.
“There are definitely some new and emerging testers which I’ve been engaging with and am happy to see new methodologies and creativity come into play, says Milbourne, “but it does take some time to build up a reputation within the industry.”
For vendors, testing criteria should be clearly communicated, and performance expectations plainly laid out in advance. Being asked to hit an invisible target is neither reasonable nor fair.
“Every organization should have the chance to look at and provide feedback on a tests’ methodology because malware is not a trivial thing to test and no two security products are exactly alike. Careful review of how a test is meant to take place is crucial for understanding the results.”
Ultimately, the most accurate evaluation of any antimalware product will be informed by multiple sources. Like reviews are considered in aggregate for almost any other product, customers should take a mental average of all the trustworthy reviews they’re able to find when making a purchasing decision.
“Any one test is just one test,” reminds Milbourne. “We know testing is far from perfect and we also know products are far from perfect. So, my advice would be not to put too much stock into any one test, but to look at a couple of different opinions and determine which solution or set of solutions will strengthen your overall cyber resilience.”