Bouncing Back from the Pandemic A Step-By-Step Guide for MSPs
To try to fight the isolation and uncertainty brought on by the COVID-19 outbreak, a few weeks ago we began what we’re referring to as “Office Hours” on the Webroot Community. It’s meant to be a forum where users can come together and pose their COVID/cybersecurity-related questions to some of our experts, and we try to help however we can.
The quality of questions and value of the dialogue were high right off the bat. It’s proven to be an excellent reminder of the usefulness of the Community in general. Some of the questions were even topical and popular enough to warrant a deep dive.
“How can MSPs help their clients bounce back from these challenging times?” is a good example.
As the question suggests, it’s not all bad being an MSP right now. With many employees migrating to remote work, IT services are in high demand. That could explain why, according to a study by the RMM platform Datto, though about 40% of MSPs anticipate cutting revenue projections for the year, 84% still say it’s a good time to be an MSP.
There’s both opportunity and necessity in developing a plan to help small business clients stay afloat in a flagging economy. On the opportunity side, exceptional customer service can be a great way MSPs to stand out in an industry with typically tight margins. On the other hand, if an MSP’s clients’ tank, they will longer be around to need the MSPs services. So, the ability to be an IT advisor for clients’ through tough times is intimately tied to the success of the MSP themselves.
What follows are a few pieces of advice for doing that, but’s important to remember that there’s no stock solution for bouncing back as a business. Every client is unique and so are the pressures applied by the coronavirus and subsequent economic slowdown. But here are some generic tips for being your client’s go-to adviser for weathering the storm.
- Set-up a virtual ‘discovery’ meeting to discuss with them what their situation really is? This should be a (perhaps painfully) honest conversation about the state of the business and what obstacles stand on the way of then getting back to “business as usual.”
- Devise an agenda based on the services you provide today and the associated costs. Based on the client’s challenges (or strengths) what is affordable what can maybe be minimized? Has the business direction changed at all? Many SMBs may be looking to pivot considering COVID-19.
- Aim to be flexible (while remaining profitable) and willing to accommodate the period between their business restarting and establishing a new normal. Ask yourself if taking a slight hit in monthly income or margins is an acceptable sacrifice to make in order to help keep a potentially long-term client afloat?
- Next, work with a client to draw up a joint “Recovery Plan” with a timeline for scaling back up the workload and how you can specifically assist with their recovery. This may involve stressing the costliness of a data breach, downtime, and other ways your services help the clients bottom line suffering.
- Finally, schedule regular client account reviews (hopefully, you already have some version of these in place) to monitor technology-related pain points and assist with addressing them as reasonably as possible.
Economic recovery for small businesses will undoubtedly entail some tough decisions. But doing everything you can as an MSP to assist with that recovery by being proactive and establishing a common recovery plan will lead to a much stronger business relationship in the future. Not to mention establishing you as a trusted, reasonable business advisor for the life of the relationship. So, take advantage of the opportunity of helping your clients’ bounce back from this pandemic.
Cyber News Rundown: ATM Jackpotting Attacks Rise
ATM Jackpotting Attacks on the Rise
ATM manufacturer Diebold Nixdorf has identified a malicious campaign that uses proprietary software to “jackpot” the machines. The attack requires malicious actors to breach the ATM manually and then use the software to force the machine to dispense cash at a rapid rate, known within the industry as jackpotting. While these attacks don’t seem to affect customer data or finances, the company is unsure how the attackers obtained the proprietary software used in the scam.
Ransomware Locks Down Telecom Argentina
Telecom Argentina is being extorted for over $7.5 million following a ransomware attack last week. The hacker group REvil is believed to be behind the attack, which may mean the stolen data is set to be posted on the group’s auction site. Officials are still unsure of how the intrusion occurred, but it’s likely to have stemmed from a compromised remote access point.
Maryland Health Services Breach Affects Thousands
More than 40,000 individuals may have had personal information leaked after a ransomware attack on Lorien Health Services in Maryland. The breach was discovered in June, but after the healthcare provider refused to pay the ransom the hackers began publishing the stolen data, which includes Social Security Numbers and other highly sensitive information. Lorien was quick to notify affected clients and had begun offering credit monitoring services to those affected within two days of the attack being confirmed.
University of York Data Breach
The University of York in the UK has learned of a data breach that occurred in May and could affect a considerable number of students and staff. The breach itself was enabled by a third-party service provider and contained personally identifiable information on an unknown number of victims. While there is little the university can do to contain this type of attack, it comes as another reminder of the importance of supply chain data security and the knock-on effect of such attacks.
Meow Attacks Target Vulnerable Databases
Dozens of unsecured databases from Elasticsearch and MongoDB were wiped in a new malicious campaign that seems to attack indiscriminately. Discovered within the last week, the Meow attacks as they’re known appear to use an automated script to overwrite any data in vulnerable databases and destroy any remaining data. This string of attacks may encourage stronger security policies among previously lax database administrators, but the lesson is costly for affected businesses.
The Changing Face of Phishing: How One of the Most Common Attacks is Evolving
Most people are familiar with phishing attacks. After all, they’re one of the most common forms of data breach around.
At their most basic, phishing attacks are attempts to steal confidential information by pretending to be an authorized person or organization. Standard phishing is not targeted. It relies on achieving a few successes out of hundreds or thousands of attempts. But because it’s so cheap to pull off, both in terms of effort invested and cost to conduct, even one person taking the bait make a campaign worth a malicious actor’s time.
But phishing has evolved. “Standard” phishing as we commonly think of it is now only a subsection of tactics carried out to achieve the same end: to swipe confidential information from an unsuspecting target in order to extract something of value.
To better be on guard across the diverse group of tactics that fall under the umbrella of phishing, users should be familiar with the ways these attacks are conducted.
We’ll cover a few here, but to learn more, download the 11 Types of Phishing Attack eBook.
Spear Phishing
If standard phishing is akin to trawling the High Seas to catch users indiscriminately, spear phishers are out for the trophy catch. Where most phishing attacks cast a wide net, hoping to entice as many users as possible to take the bait, spear phishing involves heavy research of pre-defined, high-dollar target—like a CEO, founder, or public persona—often relying on publicly available information for a more convincing ruse. When the target is sizeable enough, the CEO of a large, publicly traded company say, spear phishing is sometimes called ‘whaling.’
Smishing
SMS-enabled phishing uses text messaging to delivering malicious links, often in the form of short codes to obscure the ultimate destination of a link, to ensnare smartphone users in their scams. The term is a portmanteau of SMS and phishing, and it’s an attractive method for cybercriminals because oh the high engagement rates for texts. According to some sources, SMS open rates are around 98% compared to 20% for email. Messages are often are often disguised as sweepstakes winnings, flash sales, coupon codes, and requests for charitable or political contributions.
Business Email Compromise (BEC)
One of the most expensive threats facing businesses today, business email compromise involves a phony email, usually claiming to be someone from within or associated with a target’s company, requesting a payment or purchase be made (often of gift cards). A “confidence game” according to the FBI, BEC attempts are often accompanied by a sense of high urgency to discourage critical thinking. Of the $3.5 billion the FBI estimates businesses lost to cybercrime in 2019, nearly half ($1.7 billion) was blamed on business email compromise.
Search Engine Phishing
In this type of attack, cyber criminals wait for you to come to them. Search engine phishing injects fraudulent sites, often in the form of paid ads, into results for popular search terms. These ads often promise amazing deals, career advancement opportunities, or low interest rates for loans. Remember, if it seems too good to be true, it probably is. Often, the only difference between the scam result and the one you’re looking for is a .com that should be a .org or a .org that should be a .gov. Be on the lookout for strange endings to URLs. It may be just a country-specific domain, but they can also be hiding something more sinister.
Protecting Yourself from Phishing Attacks
Protecting yourself from phishing attacks starts with knowing what’s out there. But while staying vigilant will keep most attackers at bay, no one can be 100% secure on their own. That’s why it’s important to use an antivirus that relies on up to date threat intelligence that can block these threats in real time as they are clicked. Also, it is imperative for businesses to train their users on the types of phishing attacks employees could fall for.
For more types of phishing attacks, real-world examples, and more tips for keeping yourself or your business safe from such attacks, download the 11 Types of Phishing Attack eBook.
Cyber News Rundown: GoldenSpy
Malware Discovered in Chinese Tax Software
As part of an official Chinese tax initiative, researchers have found multiple backdoors into mandatory tax software installed on all Chinese business systems. The new malware is called GoldenHelper, in a nod to the command-and-control domain tax-helper.ltd, and has been in active development and use since 2018. The latest campaign, dubbed GoldenSpy, is adept at avoiding detection and began within months of the old command-and-control servers going offline.
Texas Collections Company Suffers Data Breach
The Texas billing and collection company Benefits Recovery Specialists Inc. has announced that a breach containing data on over 250,000 customers occurred in April. The breach leaked personally identifiable information including Social Security Numbers, birthdates and physical addresses, that could all be used to launch additional attacks. Affected clients began receiving notifications about the breach in June, though the company has still not shared what malware was installed by the perpetrators.
Microsoft Fixes 17-Year-Old DNS Flaw
After nearly 17 years of being active and exploitable, Microsoft has finally identified and resolved a major vulnerability involving a worm-like transmission that requires no human interaction. With the help of a third-party security firm Microsoft was able to patch the vulnerability before it caused significant damage, though the time was certainly there for malicious actors to use the flaw to execute any number of malicious executables onto an endless string of compromised machines.
UK Ticket Provider Leaves 4.8 Million Logins Unsecured
A collection of roughly 4.8 million login credentials have been found in a leaked database belonging to a major UK ticker provider serving customers around the world. Among the credentials were domains belonging to several government agencies along with millions of consumer webmail users. The site has also been targeted in the past by attackers looking to deface the website and has been called vulnerable to SQL injection should attackers pursue that method.
Wattpad Database Compromises Millions of Users
Officials have been working over the past week to remediate a data breach that could affect over 200 million users of Wattpad. The compromised database was listed for $100,000 on a Dark Web sale site, but was later re-listed with no price. Its owners claim to hold records for over 271 million users. Wattpad has stated that, though personally identifiable information was revealed in the breach, no financial information was accessible since Wattpad doesn’t store it directly on its servers.
Summer fitness: Let’s get digital
Summer is upon us. For some, summer is all about physical fitness. While exercise is essential to our overall well-being, we shouldn’t forget about our digital fitness, either. Just as our bodies serve our needs and help us go about our daily lives, so too do our computers and digital systems. And they deserve the time and effort it takes to make them as healthy as they can be. With that in mind, we talked with Webroot Security Analyst, Tyler Moffitt about digital fitness – and cyber resilience – for individuals and businesses. Be sure to add the following tips to your summertime fitness goals.
How is cyber resilience analogous to physical fitness?
Cyber resilience is all about having a robust security posture and making sure you take care of your digital presence with your internet-connected devices and accounts. These are all parallels with physical fitness in that it’s a life choice and not something you can just do only once in a while.
What are the things we can do to maintain healthy digital lifestyles?
Take care of devices and accounts, be it work or personal. Use two-factor or multi-factor authentication (2FA/MFA) whenever possible and never re-use passwords across multiple accounts. Using password phrases is one of the best ways to create long and unique passwords. Length is strength. Backing up and encrypting confidential data and using virtual private networks (VPNs) are great best practices as well.
What are the consequences of neglecting to maintain a healthy digital lifestyle for both individuals and businesses?
The risk of being infected with malware or having accounts breached skyrockets. This can then cascade to a whole organization, resulting in its data being held for ransom. Someone may even be held responsible and could perhaps even lose their job. There’s also a risk of criminals committing identity theft against you, which can be very costly.
Exercise is only helpful if it’s done on an ongoing basis. What ongoing practices should people be mindful of to protect themselves digitally?
A few things come to mind:
- Use reputable layered security
- Embrace user education
- Lock down remote connections
- Disable what you don’t use
- Do inventory and patch management
- Have multiple backups
- Educate yourself and, if applicable, your workforce
We’re supposed to undergo regular doctor checkups to ensure we’re maintaining a healthy lifestyle. Are there “checkups” people can perform to gauge the status of their digital health?
Education! Specifically, security awareness training. We recommend phishing simulations to test yourself and ensure you can tell the difference between a standard, benign email and a phishing scam. Also, educational courses help you understand the current threat landscape and how criminals try to trick you. Cyberthieves are always adapting their approaches as people become more educated, so it’s important stay informed about the latest tactics.
There’s only so much we can do on our own before we have to seek medical intervention from a doctor. What are the scenarios where people may want to reach out to an IT expert to address a digital health issue?
Whenever you’re unsure of something, ask – just like you would with a doctor. If you’re unsure of something going on with your body, you would ask the doctor for more info. The same holds true for your digital life. If you receive an email that you think might be phishing but are unsure, don’t just click and hope for the best. Immediately ask an IT professional who can advise you. And do the same when handling or storing sensitive information. Make sure the methods you use to transmit and store data are encrypted. For handling business data, find out what your organization’s data retention policy is and make sure you’re complying with it.
Carry it forward
Summer motivates us to get fit more than other times of the year. But just like physical fitness is best when it’s practiced year-round, so is digital fitness. Cyberthieves don’t take breaks at any time of year. And neither should you when it comes to practicing good cyber resilience behaviors.
There Are Savings to be Had in Cybersecurity. Just Not Where You Might Think.
Prior to the outbreak of the novel coronavirus, Webroot’s annual Threat Report highlighted a 640% increase in active phishing sites on the web. However difficult it may be to believe (or easy, depending on your outlook), things have gotten even worse since.
From fake anti-malware sites named for the virus (Really. See below.), to phony tracker apps that actually stalk users, to Netflix and Disney+ phishing scams that steal login data by taking advantage of a coronavirus-induced “streaming boom,” cybercriminals are getting crafty with COVID-19.
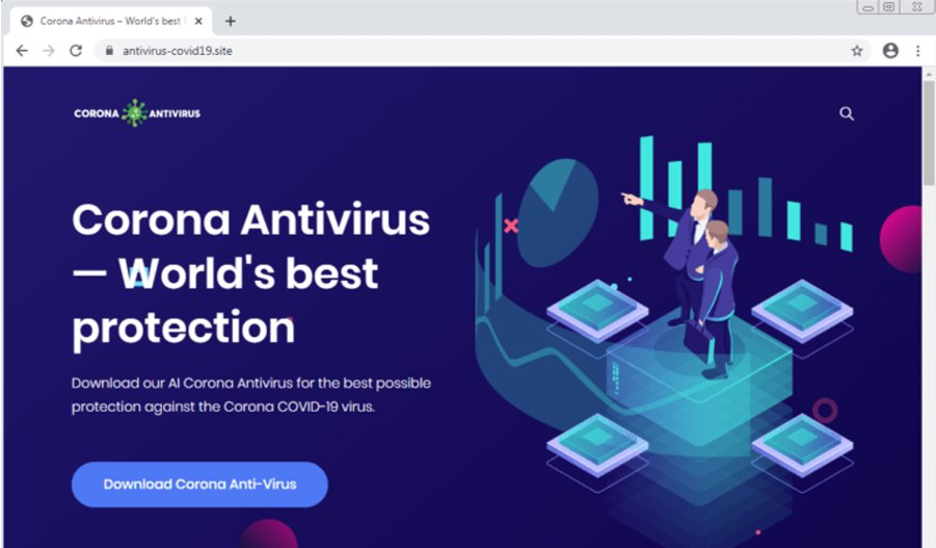
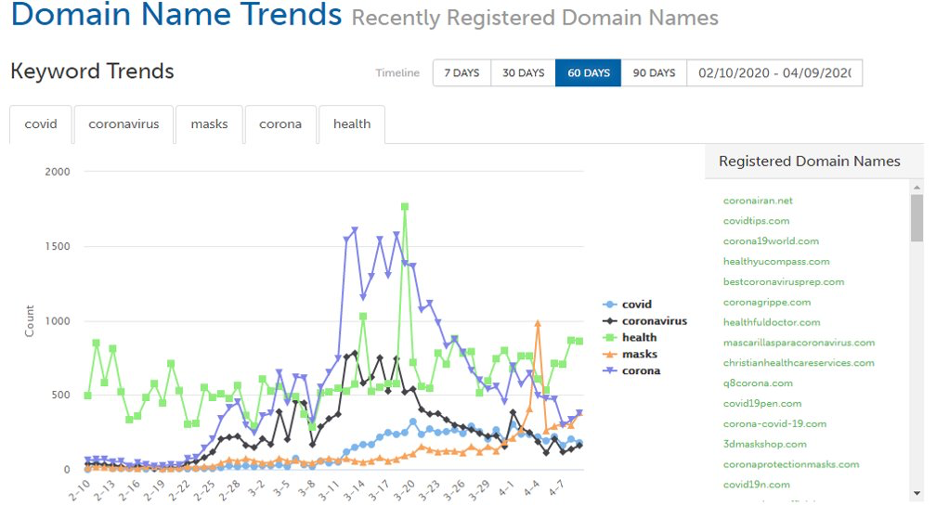
Threat analysts at Webroot have been tracking the rise in registered domain names with names including “covid,” corona,” and “coronavirus” since the outbreak began, noting that 2 percent of the more than 20 thousand newly registered domains containing those terms are malicious in nature. Files marked malicious that included the word “Zoom” grew more than 2,000 percent.
All these threats have arisen concurrently with an economic downturn that’s brought about fear, uncertainty, and the need to cut costs. Depending on the shape the recovery takes, we could be living with these unfortunate realities for some time. That means cybersecurity spending will inevitably be considered for the chopping block within many organizations. This is a bad idea for the reasons listed above and a great many more.
What’s needed, instead, is a greater investment in cybersecurity. As the World Economic Forum stated in an article entitled “Why cybersecurity matters more than ever during the coronavirus pandemic,” cybercrime flourishes during times of fear and uncertainty. We’re also spending more time online and relying on digital productivity tools as much as ever.
“Pressure will mount on business leaders to take action to cut costs and security spend may be highlighted for reduction,” say’s Webroot Sr. Director of Product Nick Emanuel. “However, the economics here are clear—cybercriminals are not cutting their budgets and are waiting to exploit weaknesses.”
And if organizations decide to preserve their remote workforces in order to promote employee safety and cut facility costs, as many tech companies are already doing, the cybersecurity landscape could be altered permanently.
“With the unprecedented shift from office to work from anywhere, it’s crucial that businesses review their remote working policies for data protection, as well as security, and be prepared for the variety of different work environments,” said Emanuel.
Cybersecurity in a Strange New World
So, what can you do to enhance cybersecurity for your business or clients? Rather than dropping products or sacrificing protection, develop a laser focus on these four principles:
- Automation—Companies must consider how AI and machine learning can assist with cybersecurity tasks. Adoption of these technologies is already high, but understanding remains low. When used effectively, they can reduce the need for high-paying, talent-scarce positions, freeing up the talent you do have to think strategically about larger business issues. Automated backup for businesses also reduces workload and guards against data loss, which can be costly in terms of loss productivity and potential fines.
- Education—Phishing is still the largest single source of data breaches, according to the latest Verizon Data Breach Investigation Report. Again, this is a quick way for malicious actors to install ransomware or to gain access to sensitive information, leading to downtime and fines. Luckily, users can be taught with some reliability to spot phishing attacks. Webroot’s research has found that, with ongoing training with a phishing simulator, click rates for phishing attacks can be reduced by more than 85%.
- Insurance—Data breaches are existential threats for many small and mid-sized businesses (SMBs). According to IBM, data breaches for organization between 500 and 1,000 cost an average of $2.65 million. Normally, organizations would hedge against such astronomical threats. Cybersecurity shouldn’t be any different. The U.S. Cybersecurity & Infrastructure Security Agency (CISA) recommends cybersecurity insurance both as a means of promoting additional protection in exchange for more coverage and encouraging best practices for better premium rates.
- Investment—Finally, businesses should invest wisely in their cyber resilience. This can be thought of as a holistic approach to cyber wellness that allows an organization to remain on its feet, even in the face of serious threats. Data security and data protection are essential components of cyber resilience. Data security entails endpoint security, sure, but also DNS filtering and security training for protection at the network and user levels. Data protection entails automated, encrypted backup and recovery for endpoints and servers to defend against ransomware, hardware failure, and device loss or theft. Together, these elements of cyber resilience reduce the likelihood of any one cyber setback being catastrophic for your business or clients.
MSPs and SMBs, rather than cutting costs by sacrificing their cybersecurity, should look to enhance it. While some of these steps may seem aimed at companies in a growth phase, they can actually improve the bottom line over the long run. After all, the costs of preparation pale in comparison to the cost of a breach.
Cyber News Rundown: Ragnar Locker
Ragnar Locker Attacks Portuguese Energy Producer
It was recently confirmed that Energias de Portugal (EDP), one of the largest energy producers in the world, has fallen victim to the Ragnar Locker ransomware variant. The original attack took place in April but was only discovered in May after nearly three weeks of being active on their systems. After contacting affected customers, the company also revealed it was subject to a Bitcoin ransom of roughly $10 million to ensure the stolen data wasn’t publicly released.
Xchanging MSP Falls Victim to Ransomware
An MSP known as Xchanging, which primarily serves the insurance industry, was hit with a ransomware attack over the weekend that forced it to take many of its systems offline. Though the attack was largely confined to Xchanging’s systems and only affected a small number of customers, it is still unclear how long the infection was active before discovery. In a statement, the company says it’s working to restore access to customer operating environments as quickly as possible.
Fitness Firm Exposes Customer Info
Nearly 1.3 million customer files and photos were compromised after the fitness firm V Shred was breached, potentially affecting up to 100,000 clients. The data was stored on an improperly configured Amazon S3 bucket that was discovered as a part of a larger mapping project that had already located several similar leaks. While V Shred confirmed much of the data was publicly available, it originally denied that the dataset itself contained full names, addresses, and other highly sensitive personal information that could be used maliciously.
Magecart Group Surpasses 570 Victim Sites
In the three years since Magecart Group 8’s initial foray onto the card-skimming scene, it has successfully compromised over 570 e-commerce sites around the world. More than 25 percent of the attacks targeted US domains and stemmed from 64 unique attack domains that were able to distribute injected JavaScript software with relative ease. Many were nearly identical to legitimate domains. It’s believed the group has netted over $7 million from selling stolen payment card information since April 2017.
Clubillion Casino App Leak Could Affect Millions
A database containing personally identifiable information on millions of users of the casino app Clubillion was compromised in late March. The breach was discovered and secured within five days, though heavy traffic to the site may have enabled the compromise of hundreds of thousands more individuals in that time. These types of apps are common targets of cyberattacks because they hold such large quantities of sensitive data that can be used for further attacks by leveraging the stolen data.
Evasive Scripts: What They Are, and What We’re Doing About Them
“What’s an evasive attack? At a very basic level, it’s exactly what it sounds like; it’s a cyberattack that’s designed to hide from you,” says Grayson Milbourne, Security Intelligence Director at Webroot, an OpenText company.
Based on Grayson’s initial explanation, you can imagine that evasive tactics are pretty common throughout cybercriminal activities. But they’re especially prevalent in the context of scripts. Scripts are pieces of code that can automate processes on a computer system. They have tons of legitimate uses, but, when used maliciously, they can be extremely effective and difficult to detect or block.
With Grayson’s help, we’ll talk you through some of the common script evasion techniques that criminals use.
LolBins
Living off the Land Binaries (“LoLBins”) are applications that a Windows® system already has on it by default. Funny name aside, they’re extremely useful for attackers because they provide a way to carry out common steps of an attack without having to download anything new onto the target system. For example, criminals can use them to create persistency (i.e. enable the infection to continue operating after a reboot), spread throughout networked devices, bypass user access controls, and extracting passwords or other sensitive information.
There are dozens of LoLBins for criminals to choose from that are native to the Windows OS, such as powershell.exe, certutil.exe, regsr32.exe, and many more. Additionally, there are a variety of common third party applications that are pretty easy to exploit if present, such as java.exe, winword.exe, and excel.exe.
According to Grayson, this is one of the ways malicious hackers disguise their activities, because default OS applications are unlikely to be detected or blocked by an antimalware solution. He warns, “unless you have strong visibility into the exact commands that these processes are executing, then it can be very hard to detect malicious behavior originating from LoLBins.
Script Content Obfuscation
Like LoLBins and scripting overall, hiding the true content or behavior of a script—or content “obfuscation”—has completely legitimate purposes. But, in terms of malicious hacking, it’s pretty self-explanatory why obfuscation would lend itself to criminal activities. The whole point is not to get caught, right? So it makes sense that you’d take steps to hide bad activities to avoid detection. The screenshots below show an example of obfuscated code (top), with its de-obfuscated version (bottom).
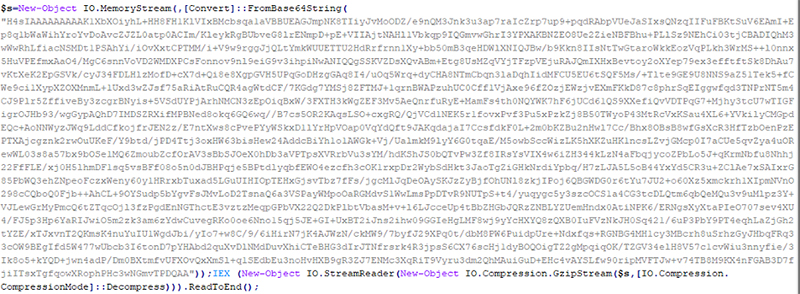
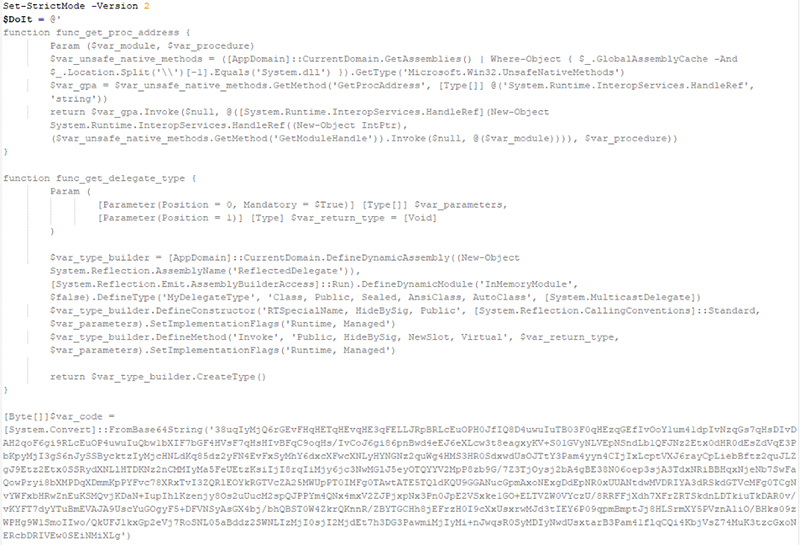
Fileless and Evasive Execution
Using scripts, it’s actually possible to execute actions on a system without needing a file. Basically, a script can be written to allocate memory on the system, then write shellcode to that memory, then pass control to that memory. That means the malicious functions are carried out in memory, without a file, which makes detecting the origin of the infection (not to mention stopping it) extremely difficult.
Grayson explains, “one of the issues with fileless execution is that, usually, the memory gets cleared when you reboot your computer. That means a fileless infection’s execution could be stopped just be restarting the system. Persistence after a reboot is pretty top-of-mind for cybercriminals, and they’re always working on new methods to do it.”
Staying Protected
The Windows® 10 operating system now includes Microsoft’s Anti-Malware Scan Interface (AMSI) to help combat the growing use of malicious and obfuscated scripts. That means one of the first things you can do to help keep yourself safe is to ensure any Windows devices you own are on the most up-to-date OS version.
Additionally, there are several other easy steps that can help ensure an effective and resilient cybersecurity strategy.
- Keep
all applications up to date
Check all Windows and third party apps regularly for updates (and actually run them) to decrease the risk of having outdated software that contains vulnerabilities criminals could exploit. - Disable
macros and script interpreters
Although enabling macros has legitimate applications, the average home or business user is unlikely to need them. If a file you’ve downloaded gives you a warning that you need to enable macros, DON’T. This is another common evasive tactic that cybercriminals use to get malware onto your system. IT admins should ensure macros and script interpreters are fully disabled to help prevent script-based attacks. You can do this relatively easily through Group Policy. - Remove
unused 3rd party apps
Applications such as Python and Java are often unnecessary. If present and unused, simply remove them to help close a number of potential security gaps. - Educate
end users
End users continue to be a business’ greatest vulnerability. Cybercriminals specifically design attacks to take advantage of their trust, naiveté, fear, and general lack of technical or security expertise. By educating end users on the risks, how to avoid them, and when and how to report them to IT personnel, businesses can drastically improve their overall security posture. - Use
endpoint security that includes evasive script protection
In a recent update to Webroot® Business Endpoint Protection, we released a new Evasion Shield policy. This shield leverages AMSI, as well as new, proprietary, patented detection capabilities to detect, block, and quarantine evasive script attacks, including file-based, fileless, obfuscated, and encrypted threats. It also works to prevent malicious behaviors from executing in PowerShell, JavaScript, and VBScript files, which are often used to launch evasive attacks
Malicious hackers are always looking to come up with new ways to outsmart defenses. Grayson reminds us, “It’s up to all of us in cybersecurity to research these new tactics and innovate just as quickly, to help keep today’s businesses and home users safe from tomorrow’s threats. There’s always more work to be done, and that’s a big part of what drives us here at Webroot.”
To learn more about evasive scripts and what Webroot is doing to combat them,
we recommend the following resources:
Cyber News Rundown: WastedLocker Shuts Down US News Sites
WastedLocker Shuts Down US News Sites
Over 30 news sites were compromised in the latest WastedLocker attack that affected many sites under a single parent company. Of the more than 30 companies targeted, eight belong to the Fortune 500 group and were in the early stages of a experiencing a fully encrypting ransomware attack. Luckily, security teams monitoring these sites acted quickly and were able to block attacks against some sites while mitigating extensive damage to others. The infiltration of these sites was caused by employees accessing previously injected websites and compromising themselves in the process.
UCSF Pays Hefty Ransom
Following a ransomware attack on the University of California San Francisco (UCSF) last month, officials have decided to pay a ransom of $1.14 million to decrypt several vital systems. The ransom amount was decided upon after negotiations between the university and the attackers. The original ask was around $3 million but was cut to less than half and was paid the following day. UCSF is one of three universities targeted with ransomware by the Netwalker hacker group in June that decided to pay a ransom to restore normal network function.
EvilQuest Wiper Targets MacOS
A new malicious actor has taken aim at MacOS with an info-stealer disguised as a ransomware attack that goes by the name of EvilQuest. Upon execution of the malicious installer, the malware begins encrypting files indiscriminately and displays a ransom note demanding only $50 in Bitcoin for decryption. The notice of encryption, however, is merely a cover for the damage occurring behind the scenes: sensitive files removed from the system with no way to retrieve them.
Fake DNS Update Looks to Steal Login Credentials
Researchers have spotted a new malicious email campaign that spoofs security companies and claims to offer a DNS update if the domain admin enters their credentials. Using a surprisingly accurate landing page, which mocks the real login sites convincingly, the site user is instructed to log in to update. To make matters worse, the attackers can scan for the site’s hosting service and customize the fake landing page to their specific victim, thus ensuring a higher probability of gaining their login info.
Passports Compromised in COVID19 Scam
In the continuing saga of COVID19 HMRC scams, attackers in Great Britain have begun focusing on the passport details of self-employed individuals in hopes of attaining personal or banking information. The scam itself originates as a text message with an urgent warning for the recipient to access a legitimate looking Her Majesty’s Revenue and Customs site to receive a tax refund. Dozens of victims have been identified across London. With these login credentials alone, attackers could access much of the victims’ data.
5 ways to reduce risky habits online
After surveying more than 10,000 people in 50 states about their cybersecurity habits, we wound up with some pretty surprising results. Like the fact that tech experts demonstrate riskier behaviors than average Americans. But the most significant result of all was the fact that most Americans are more confident than they should be when it comes practicing good cyber hygiene. So, we thought this would be a good opportunity to highlight a few of the riskiest behaviors from the report and suggest ways to correct them and minimize your chances of falling for a cyberattack.
Small business owners beware
- The problem – It’s not easy being a home-based business owner. Also known as very small businesses (VSBs), they’re often too busy and stretched thin just running their businesses. They often lack the time and resources to do everything they should to protect their important business files from online threats.
- Risky habits – Around 80% of VSB owners use the same device for both work and personal use. In addition, 71% use the same password for their personal and business accounts, putting both their personal life and company at risk.
- The fix – Owning separate devices for personal and small business use can be cost-prohibitive. But you can enforce better security by partitioning business files on your hard drive and creating a secure password to access those files. Make sure that password is different from any you’re using for personal use. Again, easier said than done in today’s world of password proliferation. If you’re struggling keeping track of all your passwords, consider using a password management app, especially for business files.
Knowing is half the battle
- The problem – There is a gap between awareness and real understanding of cyber-related attacks. Most Americans can confidently explain phone scams but are not as equipped to explain malware or phishing. This indicates that Americans may not be as prepared to confront risks as they think.
- Risky habits – Americans who never read the news are 70% less likely to recognize malware, phishing, ransomware or crypto-mining, and 51% less likely to be able to confidently explain these risks. Compare this with 89% of Americans who consistently consume technology news and can confidently explain common cybersecurity risks.
- The fix – Not everyone can afford security awareness training, but if you’re a business, consider the cost and consequences of a data breach to your business. Regular security awareness training can significantly increase your ability to identify and prevent a malware or phishing attack. If you’re a consumer or VSB owner, you can easily find free sources of cybersecurity news (like this one!). As the report shows, being a regular reader of tech news can significantly raise your awareness and reduce your risk.
Digital defense and immunity
- The problem – One in five Americans say they’ve been impacted by malware in the past year. While 61% of Americans say they’ve not been impacted, 18% aren’t sure. And with only 32% of Americans who feel they understand cyber-related attacks, it’s likely that many more have been impacted and just don’t know it.
- Risky habit – Many businesses and users haven’t updated their defenses. They haven’t updated their antivirus protection to include cloud-based threat intelligence, AI and machine-learning (ML). Or they’re failing to install necessary patches to plug holes in applications. And they’re still running obsolete operating systems, like Windows 7 or Server 2008, leaving them highly exposed.
- The fix – For today’s advanced threats, you need multiple layers of protection, including advanced antivirus as well as backup. Having just one of these layers is not enough. Perimeter protection with AI/ML functionality is critical for identifying polymorphic code that changes with each device it seeks to infect. Backup is essential for mitigating phishing attacks and disaster scenarios. Cybercriminals can also identify outdated operating systems. So, it’s worth the extra cost to update them, even if the hardware they’re running on is still functioning normally.
Identity theft
- The problem – Poor cybersecurity often leads to identity theft. Failing to wipe a device before discarding it is one problem. So is sharing personal information on social media and video streaming sites. The more hackers know about you, the easier it is for them to impersonate you online.
- Risky habits – A quarter of Americans have had their identity stolen, including 8% who have been a victim of identity theft more than once. Twice as many people who use mobile banking apps have been victims compared with those who don’t. Across industries, those in technology, banking and automotive are most likely to become victims of identity theft.
- The fix – Cover your tracks wherever you go. Erase the contents on a device before discarding it. Beware of the personal information you reveal on social media. And be careful when using banking apps and websites. Use two-factor authentication (2FA) when using the app. If you’re using the bank’s website, go directly to it by typing the URL into your browser, or use a bookmark that you trust and have used before. Be careful when searching or googling the bank’s name, which could return a spoof site in the top results.
Something phishy
- The problem – We knew phishing was a problem. In fact, it may be even bigger than our results indicate. A lot of users don’t know how to identify phishing scams. You can’t protect yourself from threats you don’t see coming.
- Risky habits – According to the report, 36% of respondents claim to have fallen for a phishing scam. But more enlightening is that only 35% claim to know how to identify a phishing attack. Similar to the lack of understanding about cyber-related attacks in general, the report seems to indicate that phishing is far more prevalent than the data indicate.
- The fix – Learn the tricks of the phishing trade, like bogus URLs and emails that ask you to confirm personal and banking information. Remember, bank logos can be easily faked. And banks won’t typically reach out to you for information they already have on file. If someone claiming to be from a bank contacts you by phone, call them back on an authentic customer service number from one of your banking statements.
Where to learn more
Want to read the complete 2020 state-by-state results? You can download a copy here. If you have any questions about improving your cyber security habits, feel free to reach out to us.
DoH Is Here to Stay: Why Businesses Should Embrace It
While the proliferation of encrypted DNS is being driven by consumer privacy, businesses will want to take notice. Encrypted DNS – also known as DNS over HTTPS, or DoH – obscures internet traffic from bad actors. But it also has the potential to decrease visibility for IT admins whose responsibility it is to manage DNS requests for their organizations. So, what’s the solution? Strangely, DoH.
As previously mentioned, DoH is now the default for Mozilla Firefox. It’s also available in Google Chrome and other Chromium-based browsers. This is a win for consumers, who have newfound control over who can see where they’re going on the internet.
However, by surrendering control over DNS requests to the browser, IT administrators lose the ability to apply filtering to DNS requests. Encrypted DNS that skirts the operating system eliminates the visibility that IT admins need to ensure security for internet traffic on their networks. It also prevents the business from being able to run threat intelligence against DNS requests and identify dynamic malware that could circumvent consumer DoH implementations. This leads to gaps in security that businesses can’t afford.
Staying ahead of the curve
There is a way to ensure privacy over DNS requests while maintaining control and visibility into network activity. The solution is to apply DoH across the entire system, not just browser activity. By wresting control over DNS requests from the browser, the agent can instruct Firefox not to engage its DoH feature. The same holds true for Chrome users running DoH. These requests are passed back through the operating system, where the DNS solution can manage them directly. This helps support both filtering and visibility.
An advanced agent will manage DNS requests on the device securely through DoH so the requests go directly to the server with no other entity having visibility into them. At the same time, the agent can apply threat intelligence to ensure requests aren’t resolving to malicious destinations. Admins have visibility into all DNS requests, and the requests are encrypted.
When the agent detects a prohibited resource, it returns the IP address of a block page. So, if there’s a virus on the system and it’s trying to access a command and control server to deliver a malicious payload, it won’t be able to. It also prevents botnets from being able to connect since they also leverage DNS. For any process that requests something from the internet, if it doesn’t get the resource that it’s requesting, it’s not going to be able to act on it.
Privacy plus security
The novel coronavirus didn’t start the mobile workforce phenomenon, but it certainly has accelerated it. The traditional perimeter firewall with all systems and devices living behind it no longer exists. Modern networks extend to wherever users connect to the internet. This includes the router someone bought from a kid down the street, and the home network that was set up by a consulting company 10 years ago and hasn’t been patched or updated since.
When someone on their home network opens a browser and goes to their favorites, they’re not expecting to get phished. But if they’re resolving to an alternative IP address because DNS is not being managed, is broken or is being redirected, they may be exposed to phishing sites. Enter encrypted DNS as another layer of protection within your cyber resilience portfolio. It starts working against a higher percentage of threats when you stack it with other layers, reducing the likelihood of being infected. It also addresses a blind spot that allows exploits to go undetected.
Embracing DoH
Privacy is the main driver for DoH adoption by consumers, while business agendas are generally driven by security. As a business, controlling DNS requests allows you to protect both the business and the user. If you don’t have that control and visibility, the user is potentially more exposed. And, if you don’t apply threat intelligence and filtering to DNS requests, a user can more easily click on malware or land on a phishing site.
To learn more about encrypted DNS read the whitepaper or review the FAQs.

Old Habits vs. New Normal in the Time of Coronavirus
It didn’t take long for COVID-19 to completely alter the way we work. Businesses that succeed in this rapidly changing environment will be the ones that adapt with the same velocity. In our second installment from The Future of Work series, you’ll hear from Webroot Product Marketing Director George Anderson, who shares his perspective on how businesses will need to adapt and evolve to stay on course during and after the global coronavirus pandemic.
How has COVID-19 changed cybersecurity and cyber resilience planning? What will be the most important steps to take moving forward?
In some ways not at all. We were already existing in a fairly perimeter-less network world. There was already a hybrid between on- and off-network staff, and reviewing where data was being worked upon, accessed and secured, and asking how data was being processed and secured during its journey. Many businesses data was already split between user devices and the cloud.
Confidentiality, integrity and availability in the case of cyber-attacks or other forms of potential data loss need to be clearly understood as before, and any weaknesses addressed. The imperative is to have a safe data cloud in place both in terms of security and recovery.
The steps to take include:
- Setting up regular and if practical continuous risk assessment to get visibility of data risks
- Understanding where the greatest risks and weaknesses exist in people, process and technology
- Investing and allocating appropriate budget to address where the greatest data loss and compromises could and would now occur
What could the future look like after the coronavirus? Specifically, what will change in IT and business?
Not everyone will want to choose to continue working from home. While the savings in closing offices down are attractive to businesses, they are not necessarily the same for an employee whose home environment is not conducive to work. These employees may seek alternative employment to remove the burden of working from home if an office option is not available. IT has already, for the most part, moved to the cloud where it can, and remained on-prem where it needs to be because of security, compliance and control. The main IT imperatives will be factors like secure 5G and faster communications for better collaboration.
In business, people buy from people. And face-to-face interaction is the norm. While this will reduce in the near-term, in the long run, peoples’ wellness depends on social interaction. Businesses that ignore that will not thrive. However, businesses are generally going to be more open to remote working roles and a lot better positioned to recruit staff for remote work, without them necessarily being close to physical offices.
IT investments will shift in the coming months, what will take precedence for companies as they go back to ‘business as usual’?
The pandemic will make companies look, in broader terms, at the all the risks to their business. And they’ll use IT where practical to put protections and assistance in place. More holistic Disaster Recovery springs to mind as benefiting from this pandemic, as does better backup of user desktops that particularly among MSPs and SMBS has not been a priority in the past.
What advice do you have for SMBs who will need time and a renewed economy to recover?
There will be many opportunities as the economy comes back and many holes where competitors and others have failed. An approach that is flexible and can react to those opportunities is essential. So, look to business arrangements in IT, Finance, HR and other key areas that will let you maximize your ability to take advantage of new opportunities. If you have not looked to an MSP to help you in the past then now is the time to look at how experts in remote management an remote working like an MSP can help?
For a step by step guide on how to improve business cyber resilience click here.